The Solution:
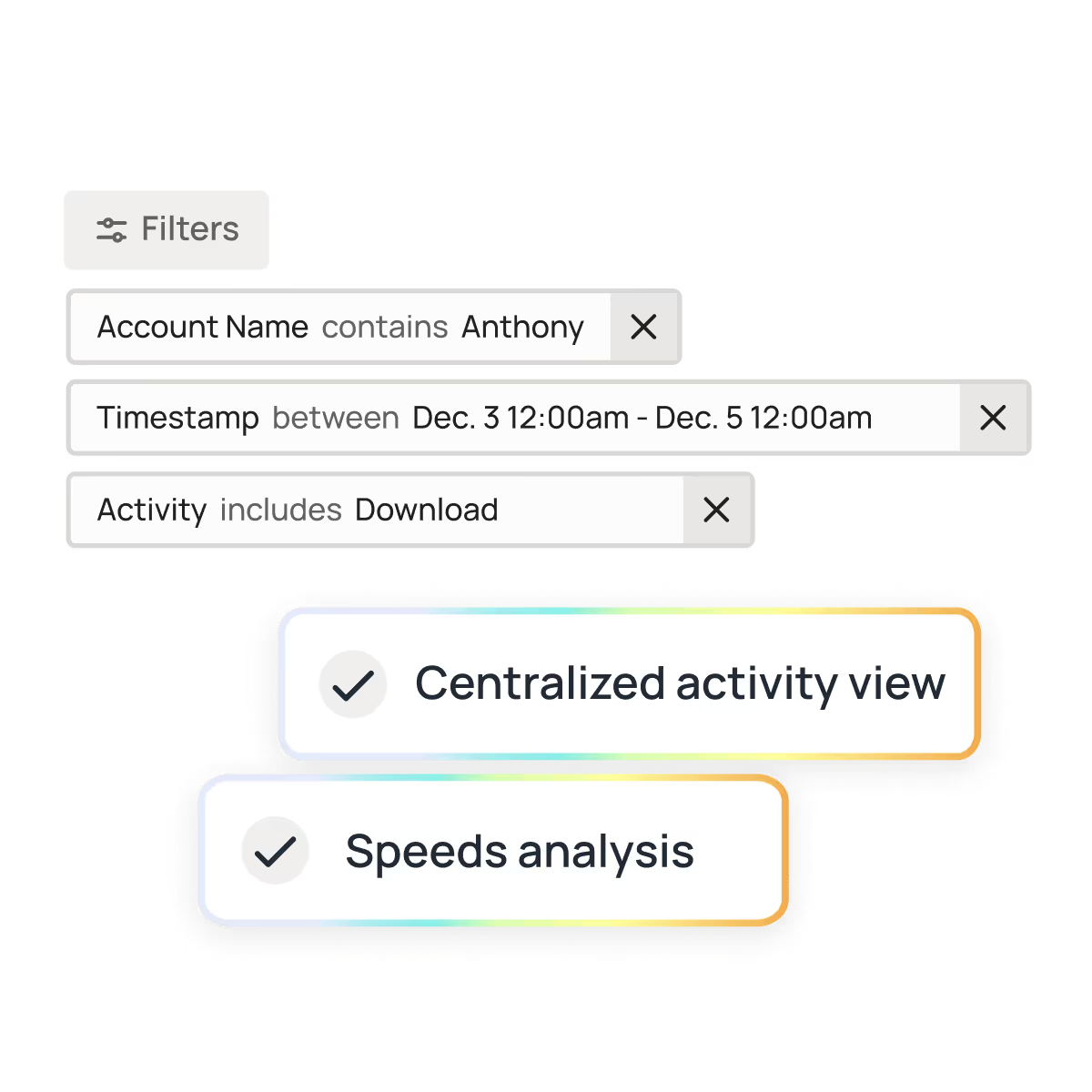
Accelerate incident investigations with comprehensive visibility and traceability.
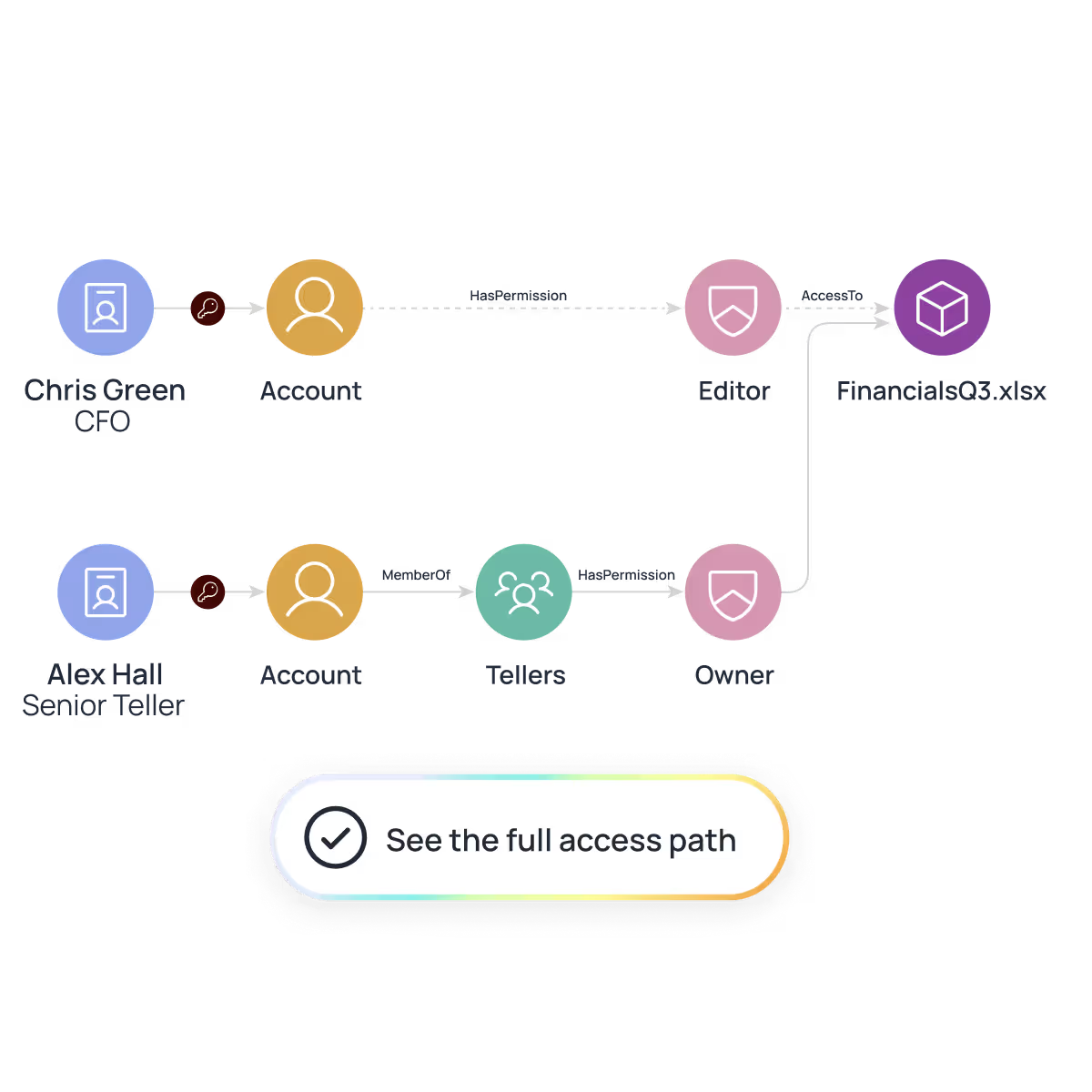
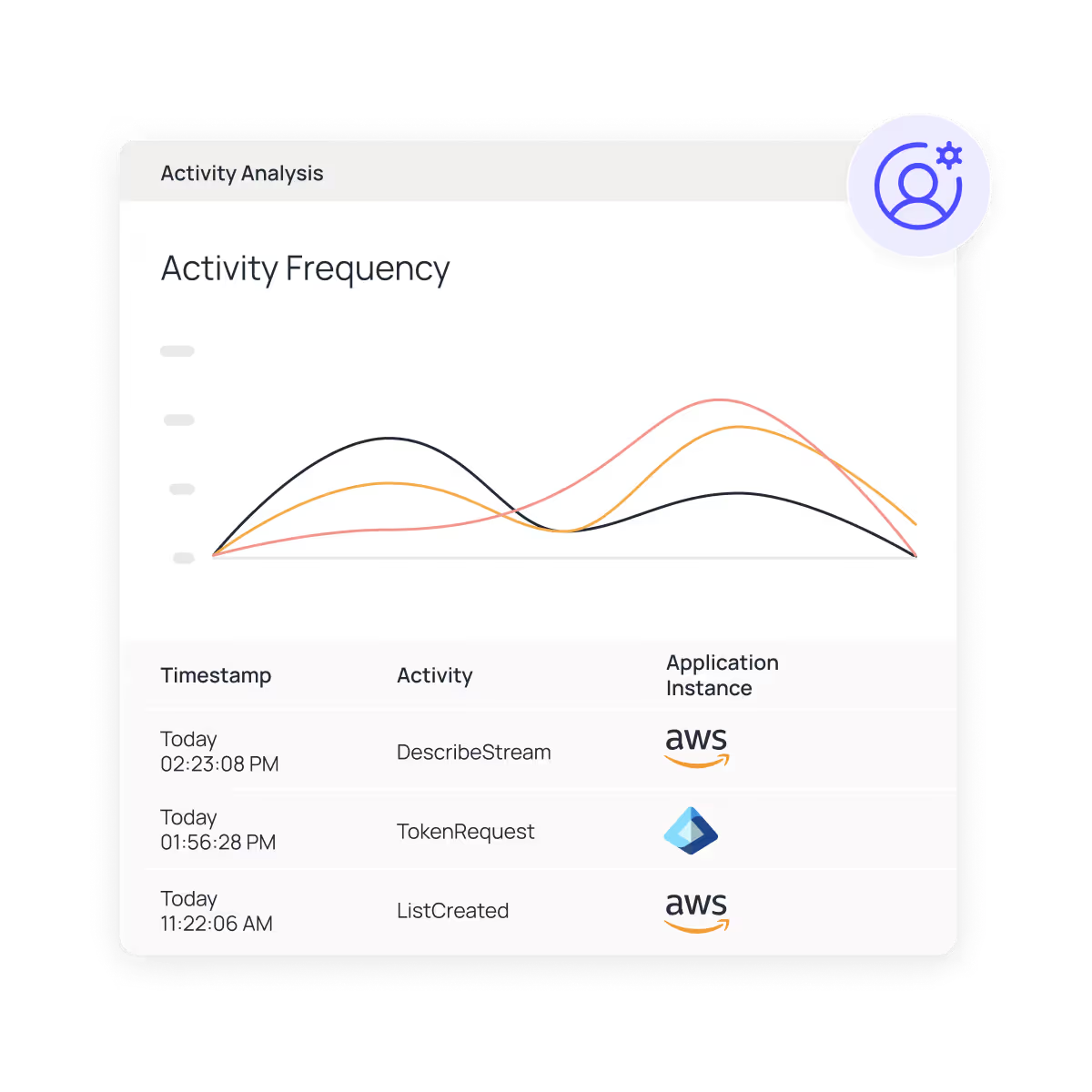
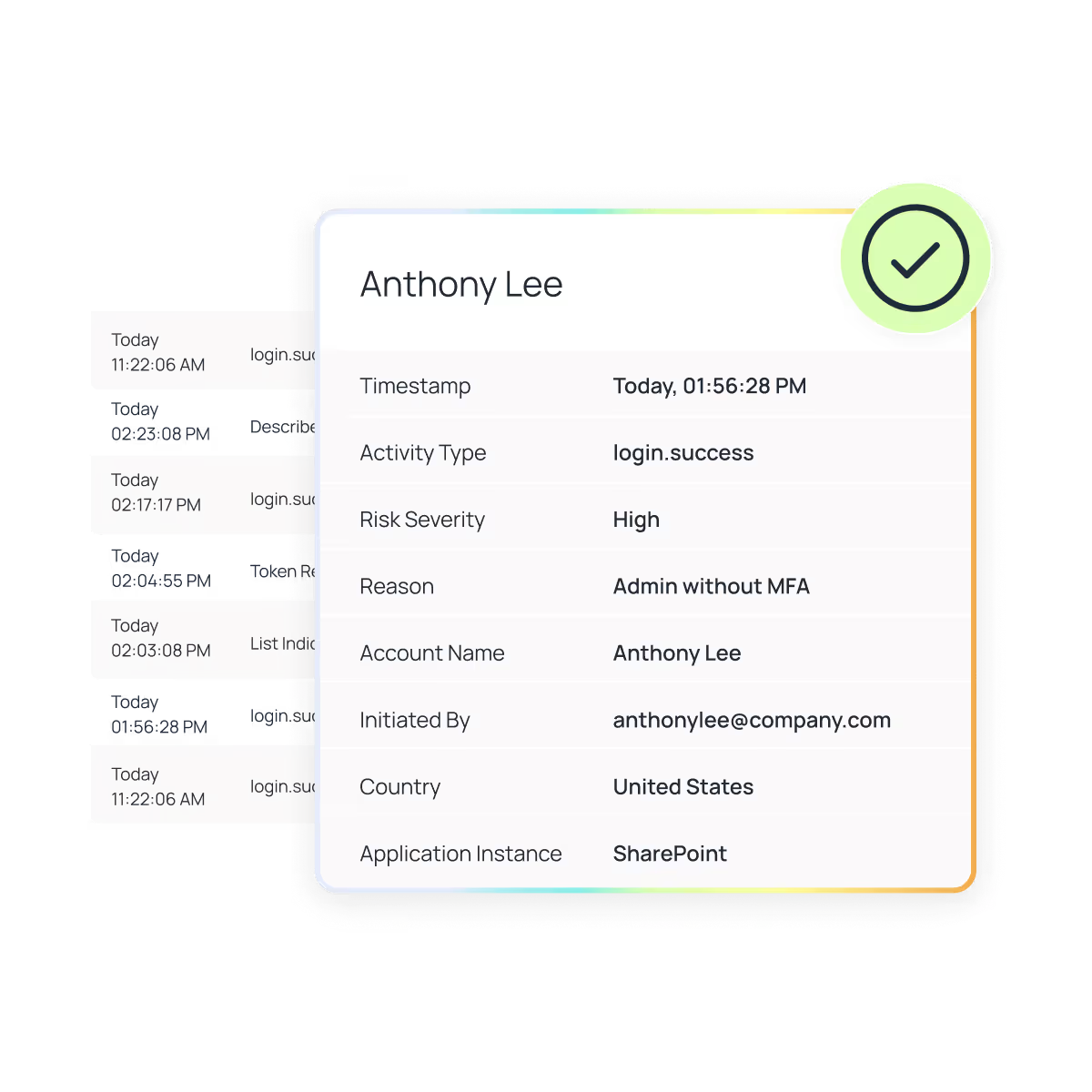
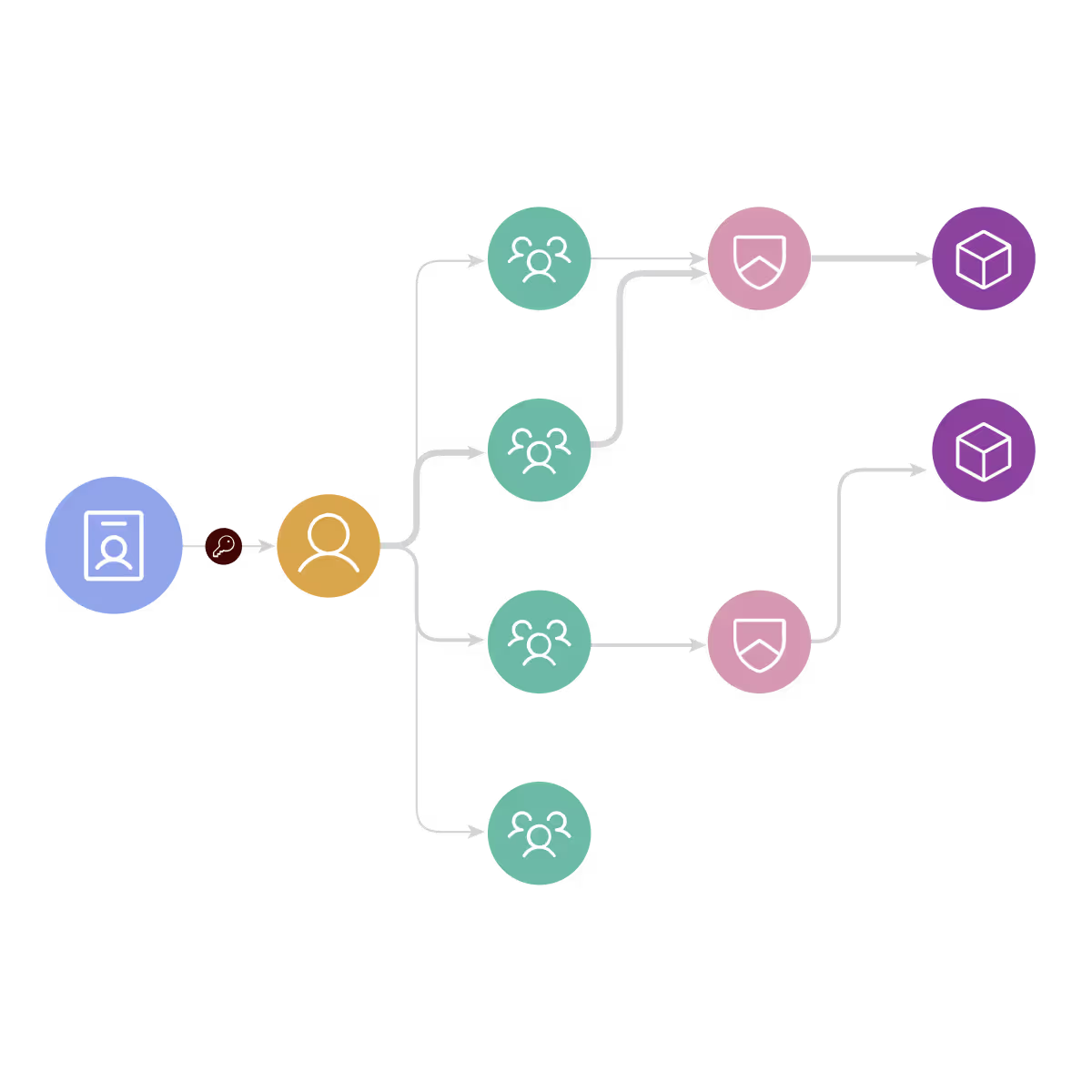
Oleria unifies identity, access, activity, and data classification into one continuously updated access graph. With fine-grained, resource-level detail, you can instantly see who had access, how they got it, what they touched, and what they did — so you can contain threats and revoke risky access immediately.
.avif)