Understanding the NHI risk
In today's enterprise environments, the majority of identities accessing systems and resources are no longer human — they're machines. These non-human identities (NHIs) — service accounts, applications, API keys, bots, agentic AI, scripts, and more — form the backbone of modern business operations. They enable automation, integration, and cloud operations that drive digital transformation.
Yet they remain largely unmanaged, invisible, and over-permissioned. In fact, a recent study showed 85% of organizations are not highly confident in their ability to prevent NHI attacks.
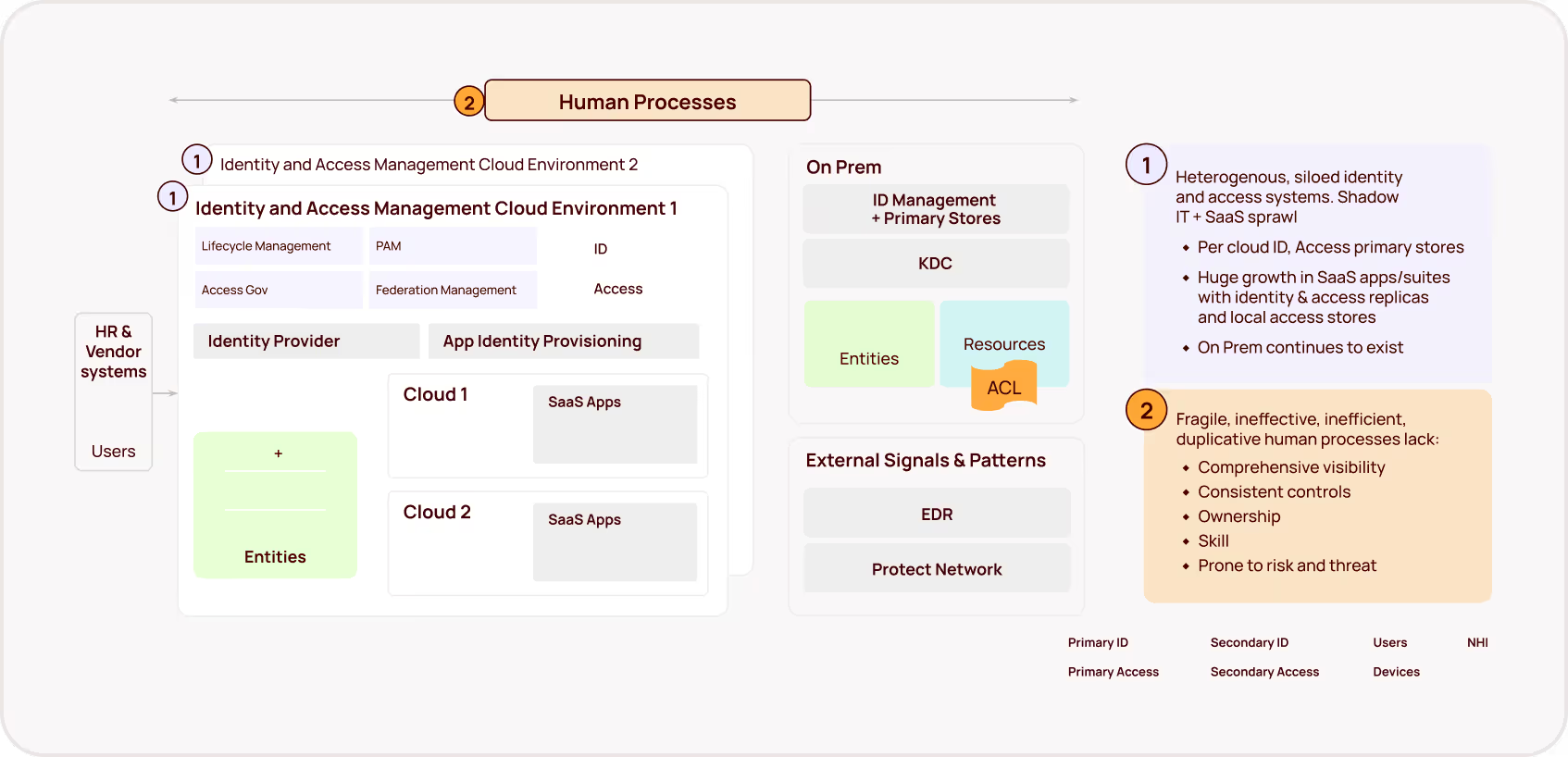
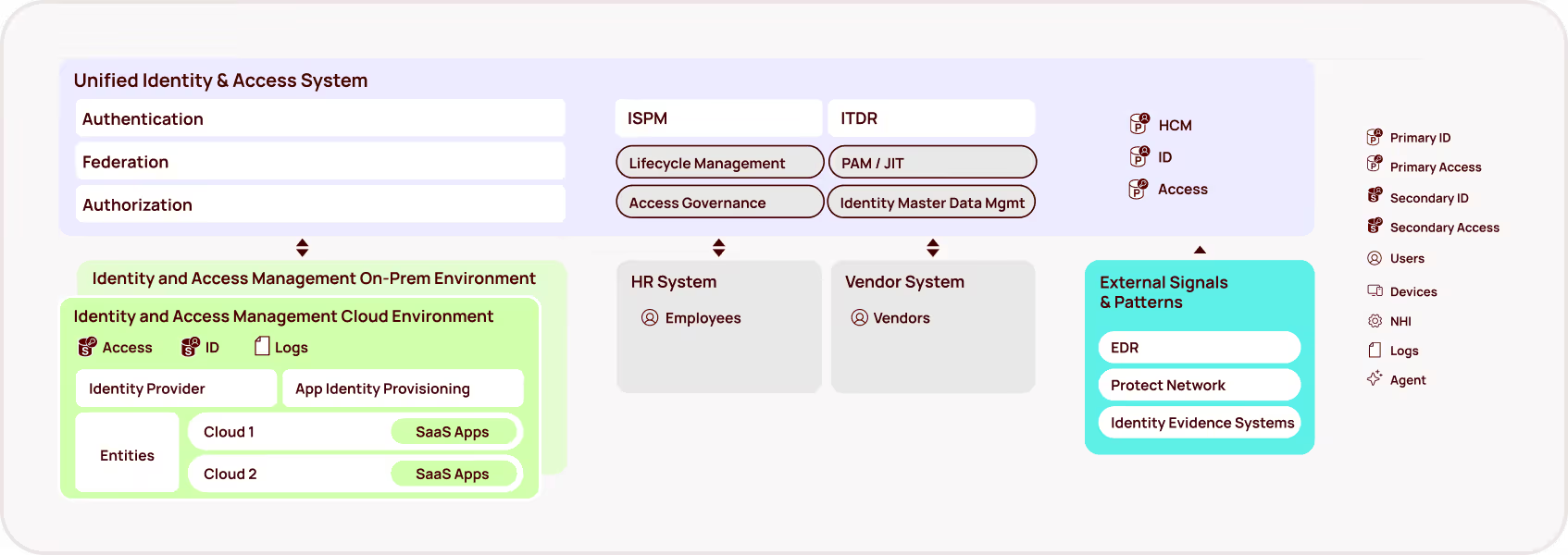
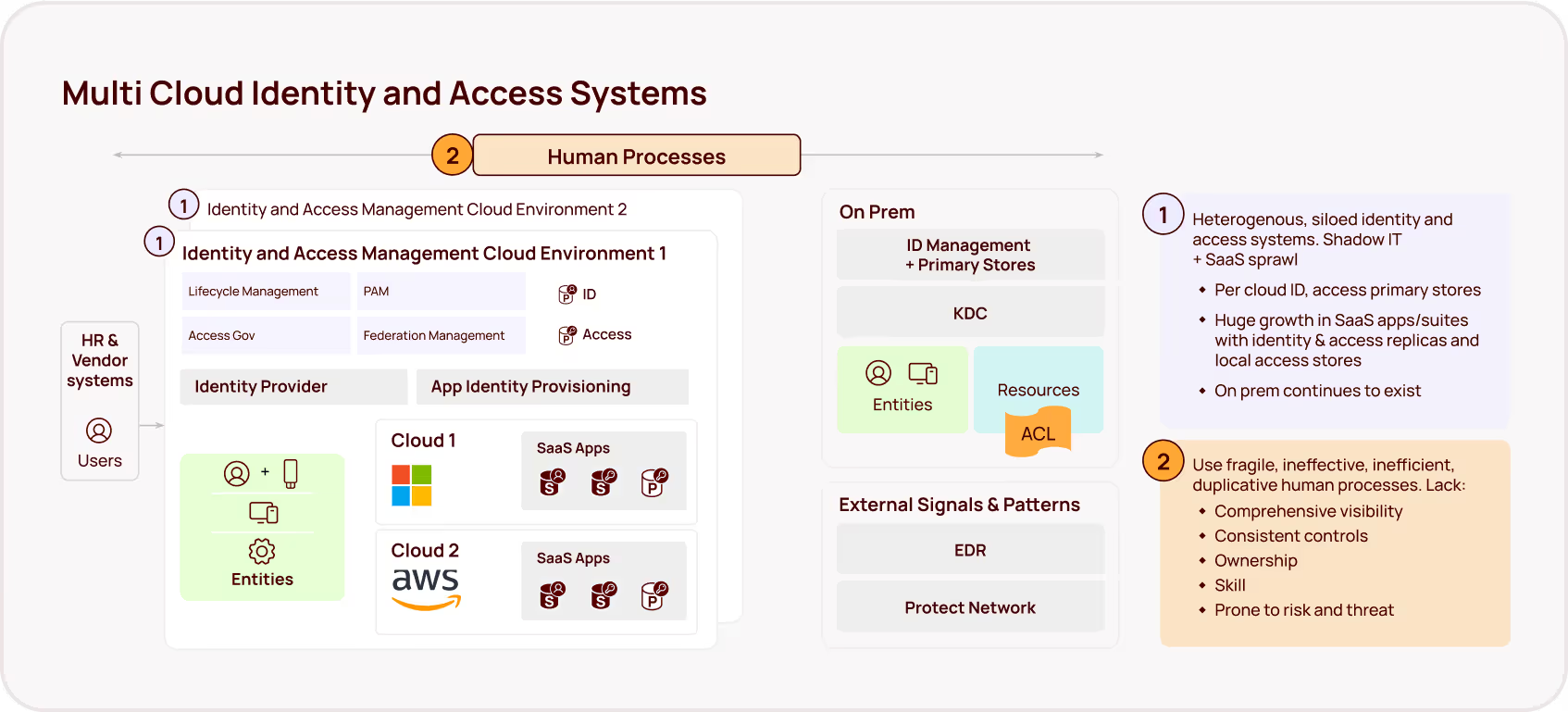
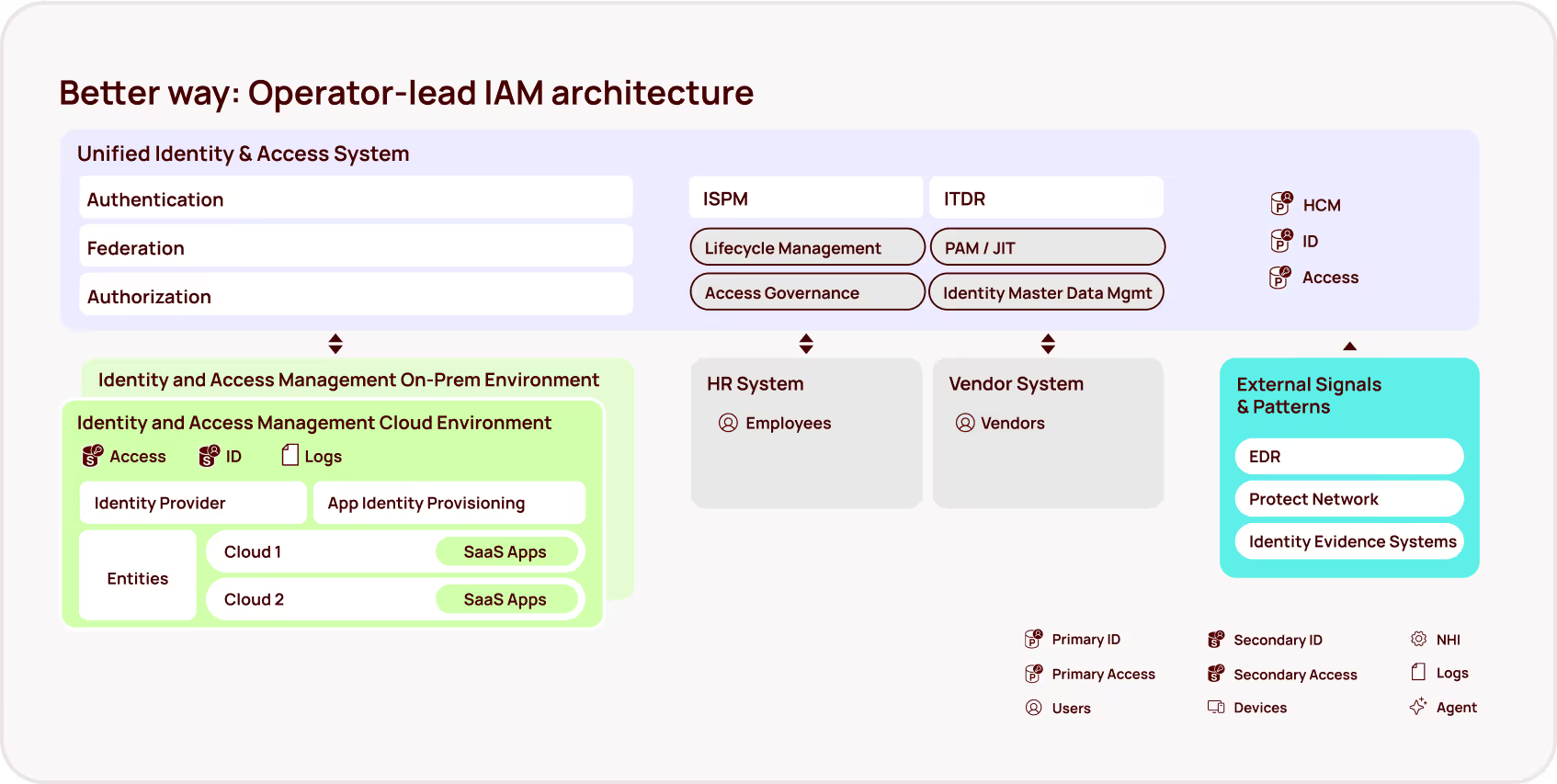
Why? Because while organizations have spent decades refining their approach to human identity management, NHIs have proliferated in the background with minimal governance. Traditional IAM tools, created primarily to support human identities, were never designed to handle the unique challenges posed by machine identities operating across hybrid environments.
The sprawling, ungoverned web of NHIs represents cybersecurity's fastest-growing blind spot — and an increasingly popular entry point for attackers. With the rise of AI (and agentic AI in particular), this problem is growing exponentially. Tools like GitHub Copilot and other AI assistants are dramatically increasing the creation of NHIs — often without any of the identity governance or lifecycle management that covers human identities.
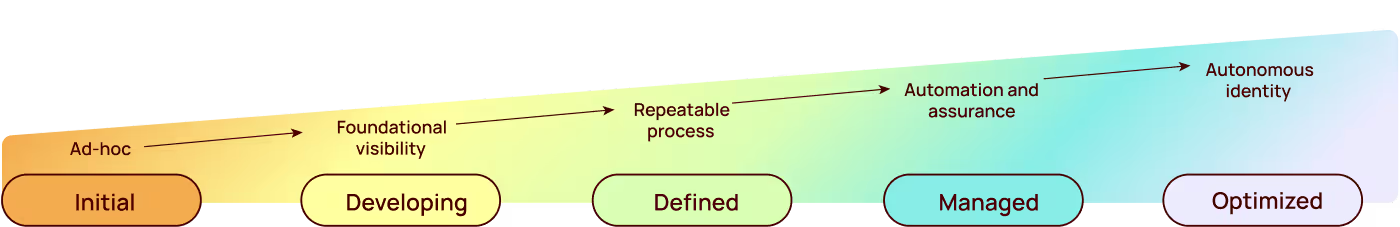
Strategic snapshot
.png)


.png)




.png)

.avif)
.avif)
.avif)