The Microsoft Admins' Guide to M365 Copilot Identity Management and Security
An identity-centric approach to protecting sensitive data in the AI era

Data security concerns are stalling M365 copilot deployments
The rapid emergence of enterprise AI-powered assistants — or copilots — is already revolutionizing the way we work and interact with information. These intelligent assistants, powered by advanced AI models, can automate tasks and provide insights that boost productivity, foster creativity, and improve decision-making.
Yet, despite incredible hype and growing enterprise investments in AI assistants like Microsoft 365 Copilot, increasing numbers of enterprises have put the brakes on their copilot deployments because of data security and privacy concerns. In fact, Gartner found that 40% of rollouts of M365 Copilot are being delayed due to security concerns related to oversharing.
Data classification (alone) isn’t enough
Security leaders (and, increasingly, the C-suite) are wary of AI copilots exposing unclassified sensitive information, prompting rapid data discovery and classification efforts. But a solely data-centric approach faces significant limitations. The sheer volume of data, coupled with the rapid genesis of new data, make classification a neverending challenge. Moreover, AI models operate at speeds far exceeding data discovery and classification, making it a perpetual game of catch-up.
Furthermore, even when all sensitive and valuable data has been correctly classified, that does not mean it is safe from unintentional exposure by an AI assistant like M365 Copilot. Organizations must distinguish between active and stale data, verify classification accuracy, and determine appropriate actions — all demanding substantial time and resources.
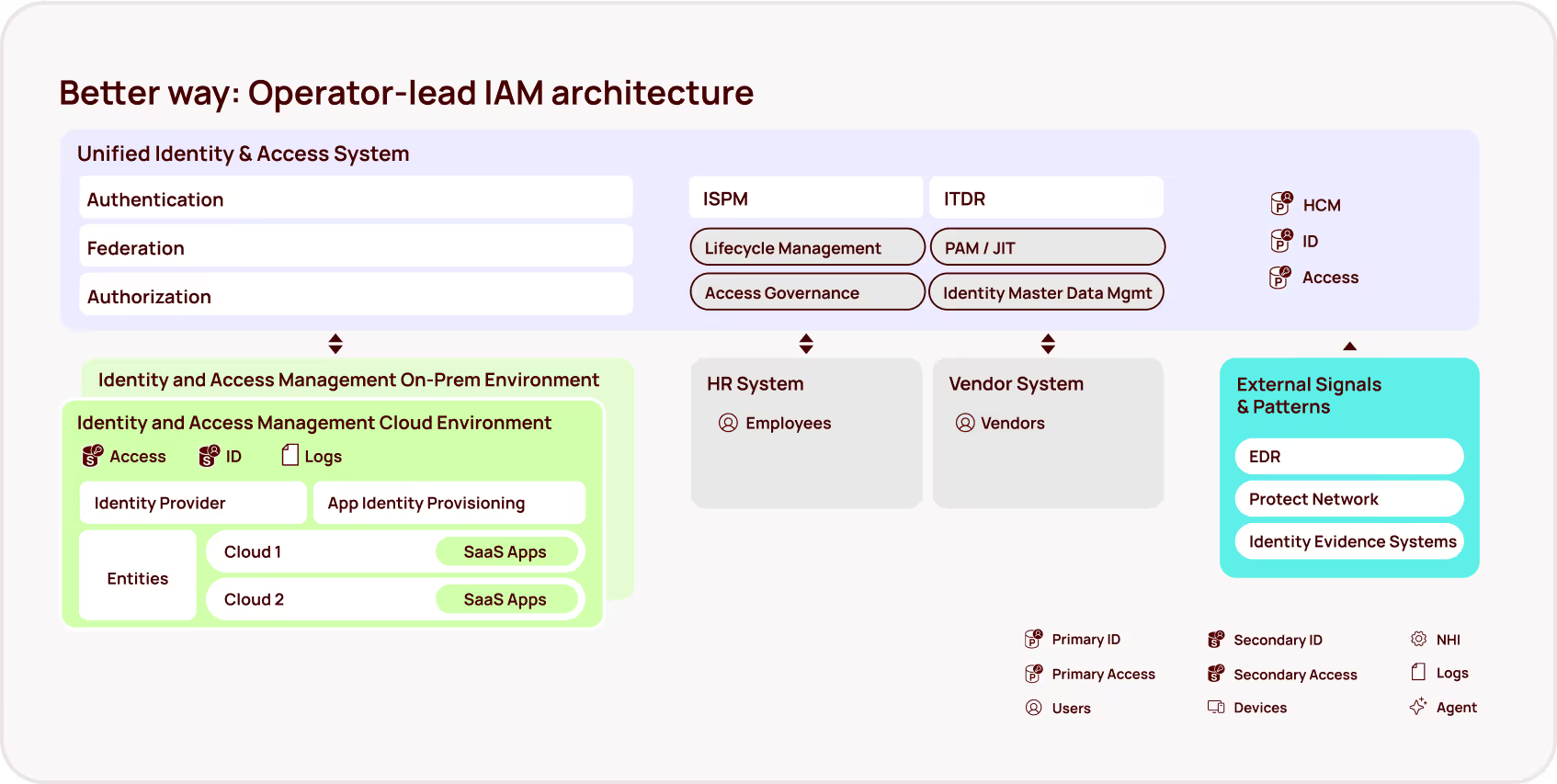
The identity-centric approach to mitigating AI copilot security risk
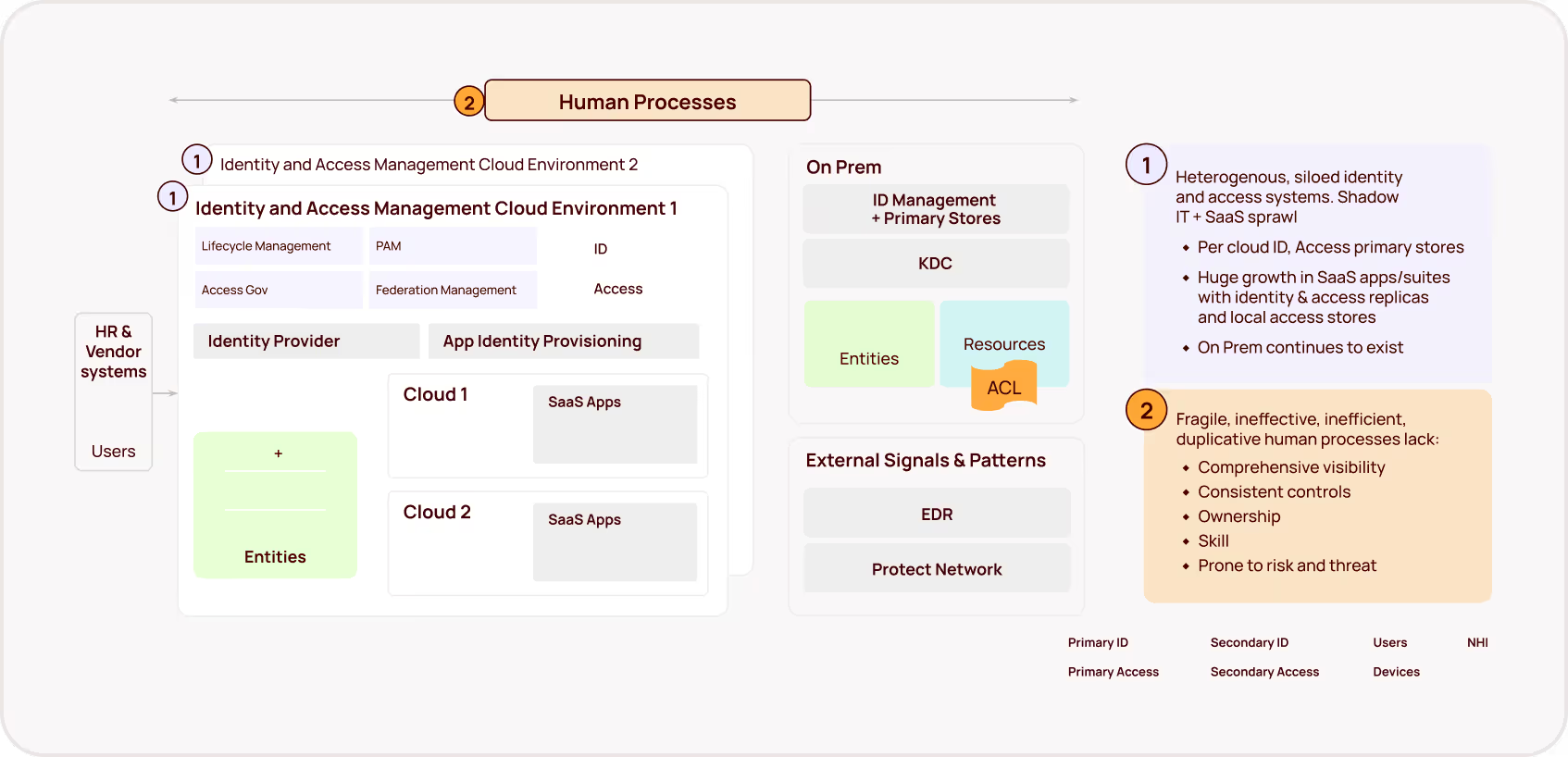
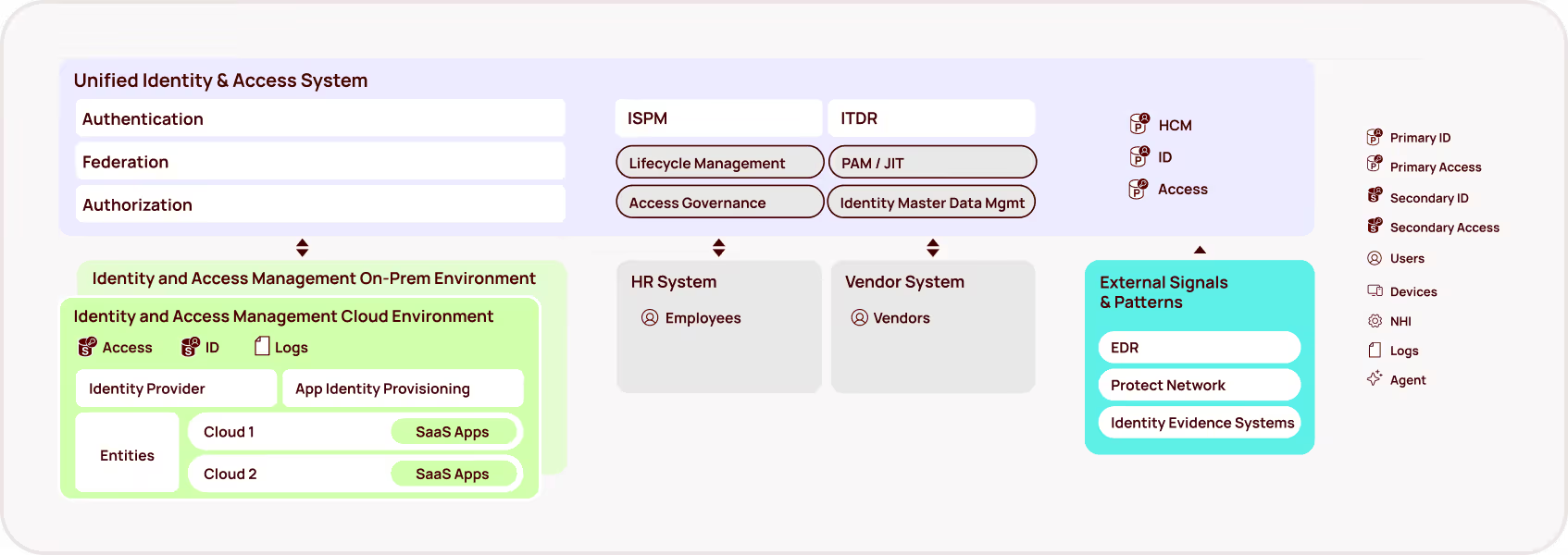
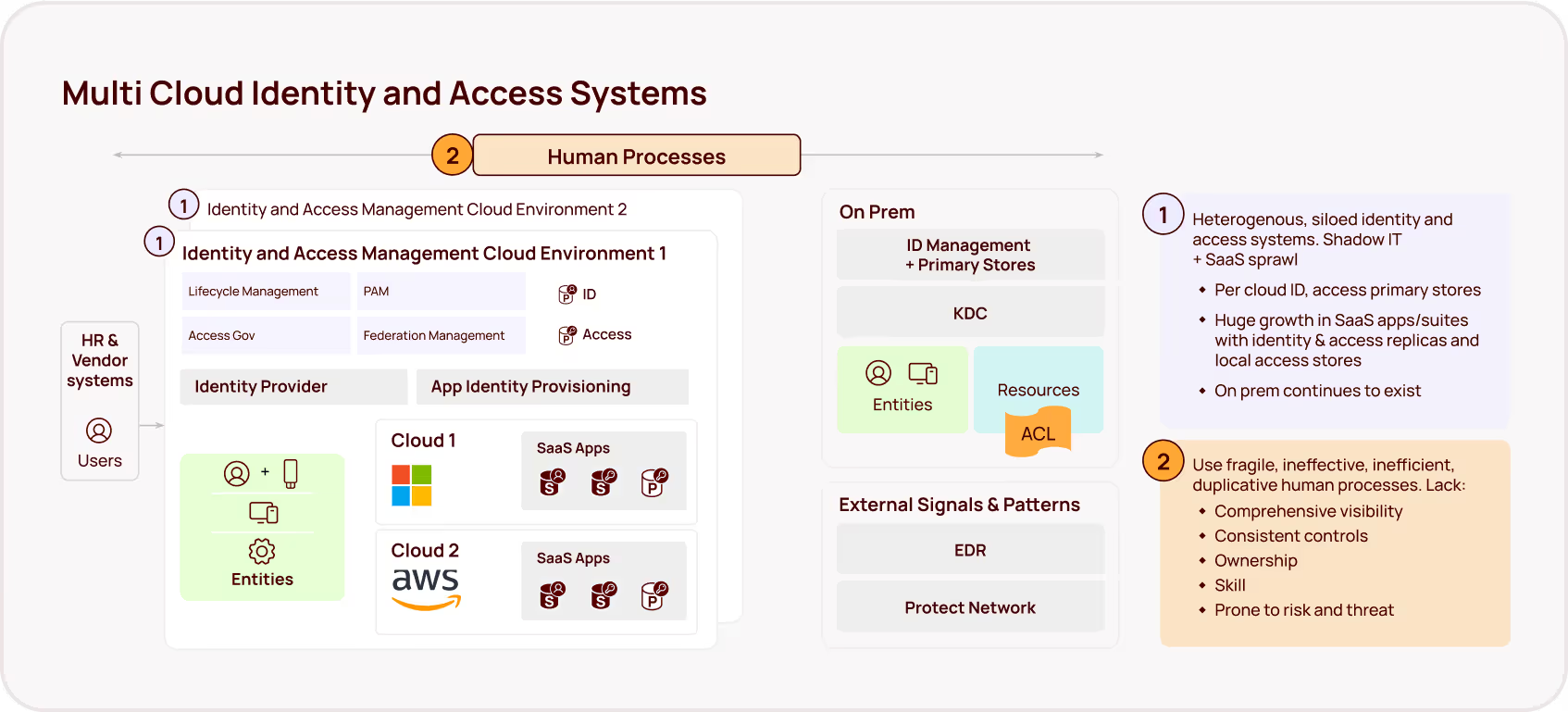
While data classification remains vital, the other side of this equation — permissions and access management — has been dangerously overlooked. AI copilots operate within the existing permissions framework, meaning that if a user has broad access to sensitive data, the copilot inherits that access and can surface that data, regardless of classification. This creates a critical blind spot: over-permissioned accounts become the perfect vector for unintentional data leaks via AI assistants.
Given the challenges and the scale of modern data environments, an identity-centric approach, which focuses on controlling access based on user identities and permissions, offers a more agile, proactive and sustainable path to securing sensitive information. By implementing least-privilege principles, organizations can limit the scope of AI assistant access. This strategy empowers security teams to focus on managing access rather than endlessly chasing the ever-expanding volume of data.
Rampant over-permissioning is the norm
Years of rapid digital transformation — and, most explicitly, the adoption of “permissive-by-default” productivity platforms that encourage easy sharing and collaboration — have made over-permissioning and over-exposure of enterprise data the norm in the typical organization. The magnitude of the issue was masked by the relative complexity of information discovery. Before AI copilots, users had to take deliberate action to find and use over-exposed information. Even prior attempts at enterprise search tools, especially those reliant on metadata tagging and traditional indexing algorithms, failed to surface the true extent of the over-exposed data risk.
But an AI assistant excels at discovering and leveraging every accessible resource — and finding subtle connections between data, unintentionally surfacing sensitive information in the process. These tools have the speed, semantic understanding, and contextual-awareness earlier approaches lacked. Given unchecked access to an unprecedented amount of enterprise data, this fundamental strength of M365 Copilot will turn the rampant over-provisioning that’s common in most enterprises into active security vulnerabilities, potentially exposing highly sensitive, confidential, and valuable data.
How big is the over-permissioning problem?
The unintended risks of Microsoft 365 Copilot
An AI assistant can unwittingly exploit over-provisioned access and misconfigured permissions. Combined with lax governance and inconsistent lifecycle management, this results in unintended exposure of sensitive data that can lead to loss of competitive advantage, reputational harm, and penalties due to non-compliance.
Here are just a few of the dangerous scenarios that can result:
More real-world M365 Copilot risks
- Exposure of strategic information from meeting recordings
- Unintended sharing of compensation or other PII data during routine searches
- Cross-application data leakage through misconfigured integrations
- Compliance violations for GDPR, HIPAA, and CCPA regulated data
The speed vs. security dilemma
A big source of risk is not the AI copilot itself, but rather the typical fashion in which the tool is implemented. Businesses are under immense pressure to move fast, innovate, and adapt. This leads to a strong bias toward speed when rolling out any new SaaS tools. But this longstanding bias — where rapid implementation overshadows robust security measures — sets the stage for AI copilots to inadvertently expose sensitive data.
How Microsoft 365 Copilot exposes access gaps
The unique capabilities of M365 Copilot and similar AI assistants deliver tremendous benefits to enterprise users — but also bring the hidden exposure risks, transforming access control weaknesses into active security vulnerabilities:
Conventional security solutions don’t fit the AI age
Traditional security tools, technologies and strategies are struggling to keep up with the rapidly evolving challenges presented by AI assistants. In short, these conventional solutions fail to provide the comprehensive visibility needed to uncover, remediate, and mitigate the risk of oversharing:
Understanding your copilot risk exposure
Deploying M365 Copilot within an organization introduces a new dimension to identity security. To effectively manage and mitigate potential risks, it's crucial to adopt a proactive and comprehensive approach to risk assessment. This involves asking critical questions and developing a deep understanding of the interplay between M365 Copilot’s capabilities and existing security infrastructure.
Here's a breakdown of key areas to address:
1. Data access scope
- Which employees can access sensitive data through the copilot? This requires mapping all users who have access to M365 Copilot and identifying the specific data they can access through these tools. This includes direct access to sensitive information as well as indirect access through queries and commands that the copilot may execute. It's essential to understand the potential for users to inadvertently or maliciously expose sensitive data via their interactions with M365 Copilot.
- How did they obtain these permissions? Trace the origin of access permissions to identify potential vulnerabilities in the access provisioning process. Were these permissions granted explicitly, inherited through role assignments, or acquired through other means? Analyzing the permission granting process can reveal weaknesses in security policies and practices.
- Is their access appropriate for current roles? Regularly review user access privileges to ensure they align with current job responsibilities and business needs. Employees may change roles, projects may evolve, or access requirements may shift over time. Failing to adjust permissions accordingly can lead to excessive access and increased risk.
- Are they actively using these permissions? Monitor access utilization to identify any anomalies or suspicious activity. Are users accessing data or performing actions that are outside the scope of their typical duties? This analysis can help detect insider threats, unauthorized access attempts, or even misconfigured M365 Copilot settings.
2. Risk quantification
- Potential unauthorized data exposure scope: Assess the potential impact of a data breach involving M365 Copilot. What types of sensitive data could be exposed? How many individuals would be affected? Understanding the scope of potential exposure helps prioritize mitigation efforts and develop incident response plans.
- Compliance violation likelihood: Evaluate the risk of non-compliance with relevant data protection regulations and industry standards. Could M365 Copilot lead to violations of privacy laws, data security requirements, or industry-specific guidelines? Assessing compliance risks is crucial for avoiding legal and financial penalties.
- Financial impact of security incidents: Estimate the financial consequences of a security incident involving M365 Copilot. This includes direct costs, such as legal fees, regulatory fines, and customer notification expenses, as well as indirect costs, such as reputational damage and loss of business. Quantifying the financial impact helps justify investments in security measures and demonstrates the importance of risk mitigation to stakeholders.
- Operational disruption costs: Consider the potential for M365 Copilot-related security incidents to disrupt business operations. Could a breach lead to system downtime, service interruptions, or delays in project completion? Assessing the potential for operational disruption highlights the need for robust security controls and disaster recovery plans.
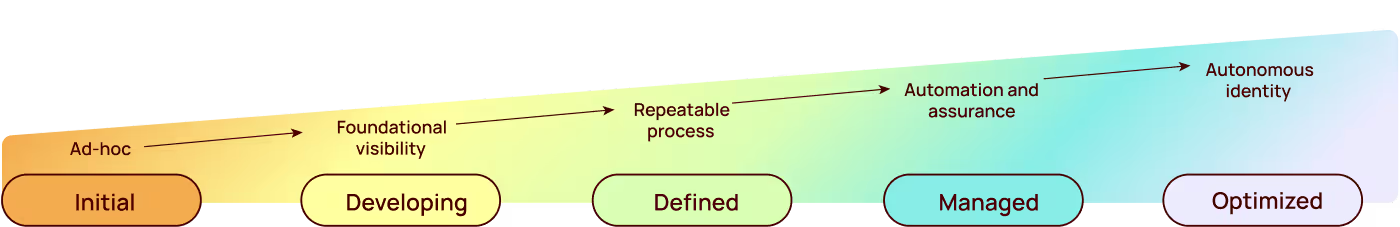
By thoroughly addressing these questions, organizations can gain a clearer picture of their copilot risk exposure and develop targeted strategies to mitigate those risks effectively. This proactive approach is essential for ensuring the secure and responsible deployment of M365 Copilot in the enterprise.
Making the business case for change
Organizations today are focused on the strong business case for implementing and expanding utilization of AI assistants. But for the IT, security and compliance teams that bear the burden of mitigating the inherent risks of these AI tools, it’s critical to build a solid business case for a modernized approach to identity and access that’s fit for the AI era.
Investing in a modern identity security strategy is not just about mitigating risks; it's about unlocking the full potential of AI while creating tangible business value. By embracing AI-driven security, organizations can confidently navigate the evolving threat landscape, protect their valuable assets, and drive innovation in the digital age.
Action plan for security and IT leaders: Navigating the AI copilot revolution
The integration of AI assistants like M365 Copilot into the enterprise presents both exciting opportunities and unique security challenges. To effectively manage these challenges and ensure the secure adoption of AI, security and IT leaders need a proactive and comprehensive action plan. This plan should encompass immediate steps, medium-term initiatives, and a long-term strategy to address the evolving landscape of AI-driven identity security.
Immediate Steps
- Conduct access audit: Audit all user access privileges across your IT environment.
- Identify critical data assets: Create an inventory of sensitive data and its location.
- Review current IAM capabilities: Evaluate if your IAM tools can handle AI copilot access.
- Assess copilot deployment risks: Identify potential security risks tied to AI copilot use.
Medium-Term Initiatives
- Implement modern identity security solutions: Invest in solutions designed for AI copilot access.
- Enforce least-privilege principles: Ensure minimum necessary access for each user and each asset.
- Deploy automated access management: Automate user provisioning and access requests.
- Enhance monitoring capabilities: Improve real-time threat detection and response
Long-Term Strategy
- Build dynamic access control systems: Develop systems that adapt to changing risks.
- Integrate AI-powered security tools: Utilize AI for threat detection and response.
- Develop comprehensive security metrics: Track and measure security program effectiveness.
- Create sustainable compliance frameworks: Ensure ongoing compliance with regulations.
Don't get left behind: Secure your AI advantage
AI assistants are no longer a futuristic concept; they are here, transforming the way we work and offering unprecedented opportunities for innovation and efficiency. But this transformative power comes with a critical caveat: traditional security approaches are simply not equipped to handle the unique challenges posed by AI.
To truly unlock the potential of a tool like M365 Copilot and gain a competitive edge, organizations must act now to modernize their identity security. This means moving beyond static, role-based access control and embracing dynamic, least-privilege models. It requires adopting advanced IAM solutions that provide clear answers to the fundamental questions of identity security:
- Who has access to what resources?
- How was access obtained?
- Is the access appropriate for current roles?
- How is access being utilized?
Failing to address these questions leaves organizations vulnerable to data breaches, compliance violations, and reputational damage. The time for complacency is over. By embracing a proactive, AI-driven approach to identity security, organizations can confidently harness the transformative power of M365 Copilot while safeguarding their most valuable assets. The future of work belongs to those who can innovate securely. The time to act is now.
How Oleria securely unlocks Microsoft 365 Copilot
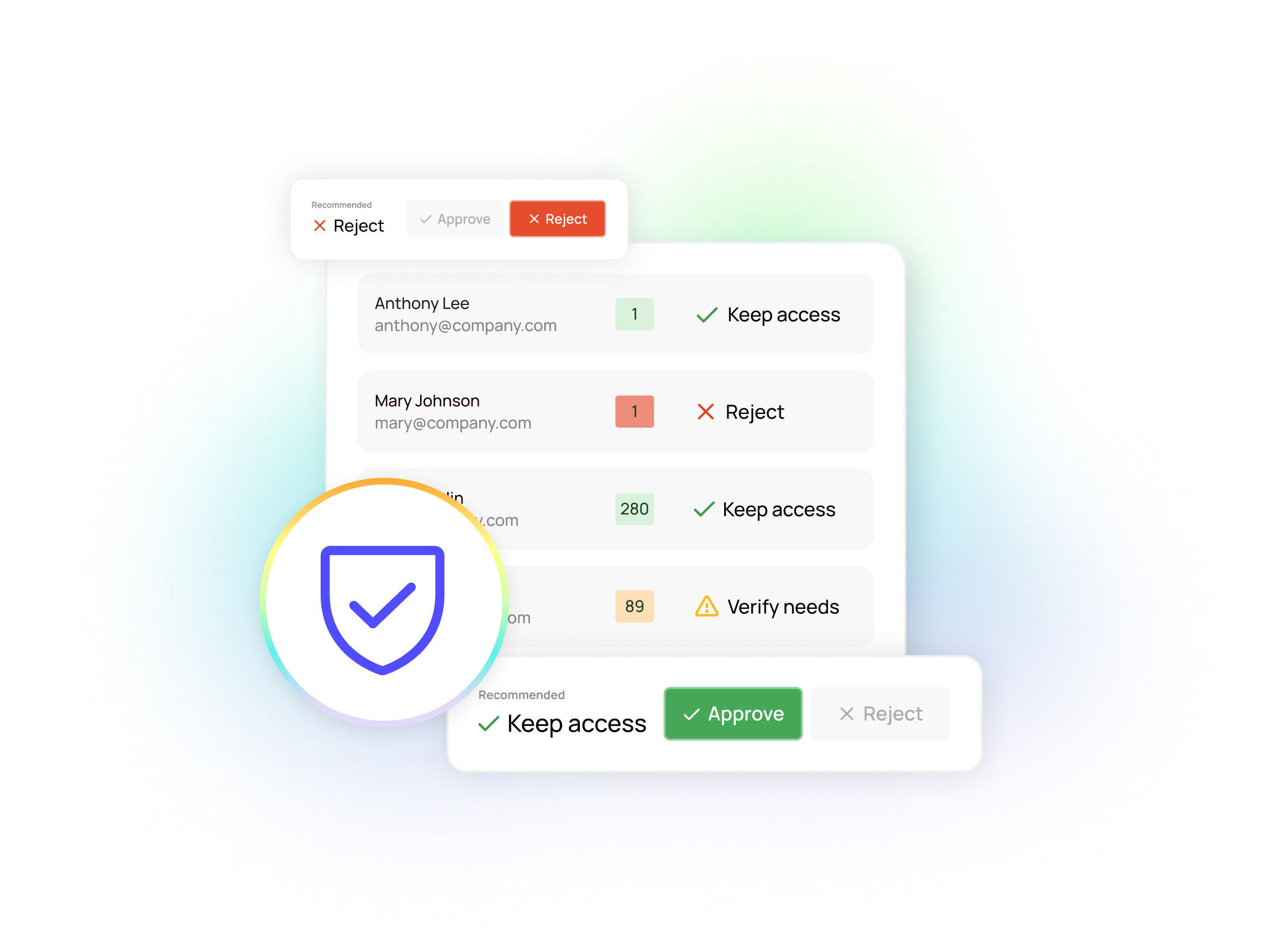
Oleria offers a unique, AI-driven approach to identity security, purpose-built for the modern workplace. Our comprehensive and automated solution provides the visibility, control, and intelligence you need to confidently and securely deploy M365 Copilot.
.png)
With Oleria, you can:
- Gain real-time visibility across all systems, including on-premises infrastructure, cloud applications, and AI copilots.
- Map out the complete chain of access inheritance to identify and address unintended access pathways.
- Track historical access patterns to identify anomalies, detect suspicious activity, and understand the context of access requests.
- Leverage detailed usage analytics to identify unused accounts, over-privileged users, and potential security risks.
- Rapidly identify and remove excess permissions, ensuring that users and AI copilots have only the access they need.
- Continuously monitor access activity, looking for anomalies and potential security violations.
- Enforce access policies in real-time, preventing unauthorized access attempts.
- Maintain compliance with relevant regulations and industry standards.

Don't let security worries hold back the promise of AI assistants. Oleria provides the foundation you need to confidently embrace the future of work.
Watch a recorded demo to learn how Oleria addresses identity security risks unique to Microsoft 365 Copilot, empowering your organization to securely leverage AI-powered productivity.
Recent articles

Oleria Identity Security: Bringing modern access management to the dynamic enterprise

Heading
.png)
Built for the AI Era: How Oleria’s Unified Identity Security Approach Is Validated by the Industry

Heading




.svg)

.png)

.avif)
.avif)
.avif)