Protect your GitHub from identity threats
The Wake-Up Call You Didn't Know You Needed

Attackers aren't hacking in - they're logging in
Right now, a threat actor could be browsing your company's private GitHub repositories — not because they found a zero-day exploit or launched a sophisticated attack, but because they're logged in with stolen credentials. In 2023 alone, over 12 million authentication secrets were leaked on GitHub. Major brands including Uber, Okta, Samsung, and LastPass learned this the hard way.
If you're thinking,"We have MFA enabled, we're safe," think again. This guide was created because we've seen too many organizations discover critical identity security gaps only after a breach. By then, their code, credentials, and API keys were already exposed.
This guide is for you if:
- You worry if your team's GitHub access is actually secure
- You need to make changes to your repository permissions but don't know where to start
- Your developers keep asking for admin access "just for this one project"
- You suspect former employees or contractors might still have access
- Your audit team is asking questions you can't confidently answer
- You can’t easily answer key questions about GitHub access: Who has access to what? What are they doing with that access? And do they actually need that access?
The common blind spot in code hygiene & supply chain security
The shift-left movement has transformed how organizations approach security, bringing unprecedented focus to code hygiene and supply chain security. Development teams are writing more secure code than ever before, integrating security scans into their pipelines, and catching vulnerabilities before they reach production.
While organizations have fortified their code, many have one dangerous blind spot: identity security within their development environments.
Critical exposure points:
- Compromised credentials (now the #1 attack vector)
- Privilege abuse from insider threats
- Unauthorized access through legitimate logins
- Complex permission structures that hide security gaps
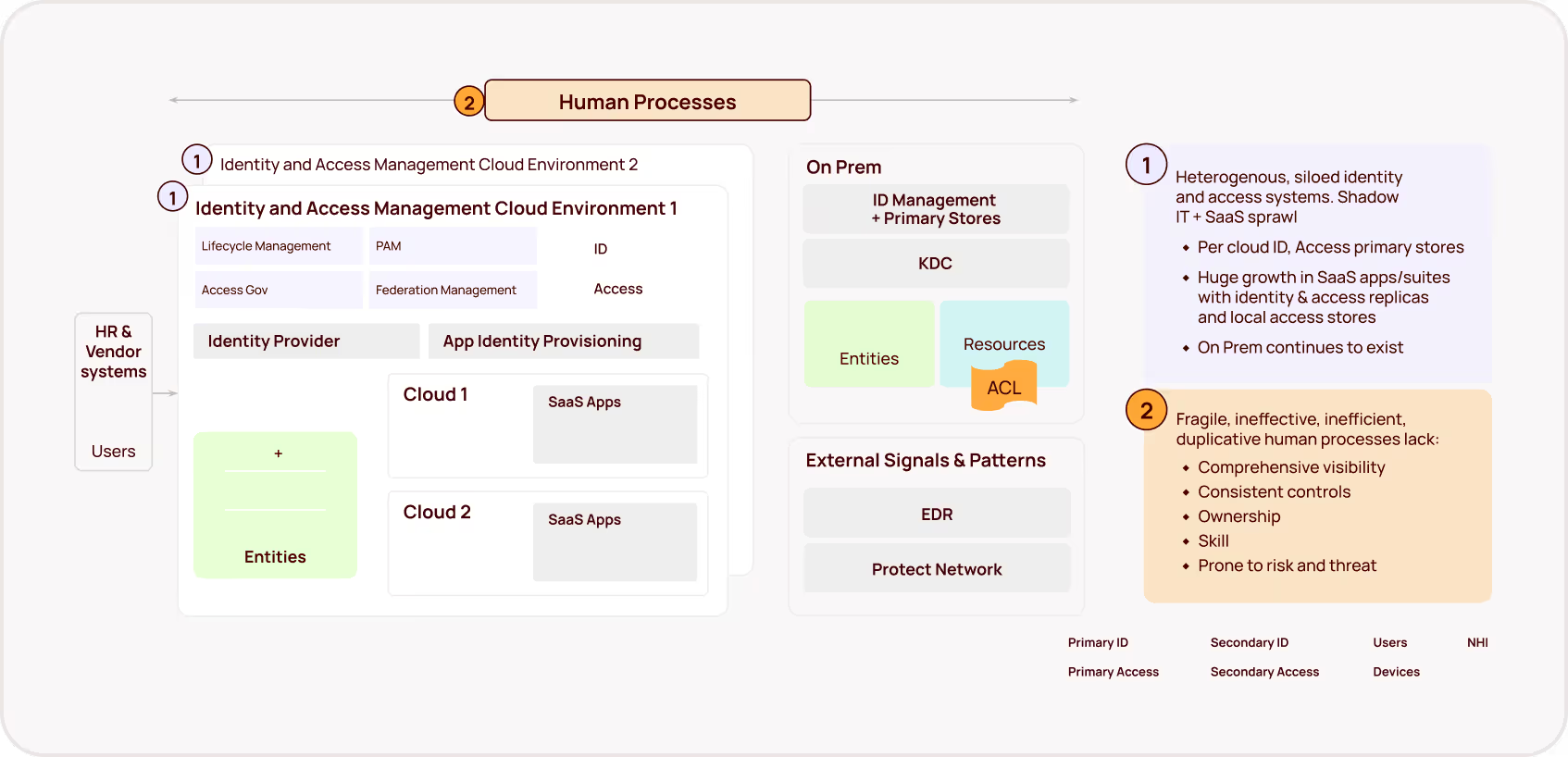
Whether it’s a malicious external actor using stolen credentials or a disgruntled insider who has been planning a sabotage for months, if you can’t see who has access to what across your GitHub environment, you’re bound to be reacting too late to these incidents.
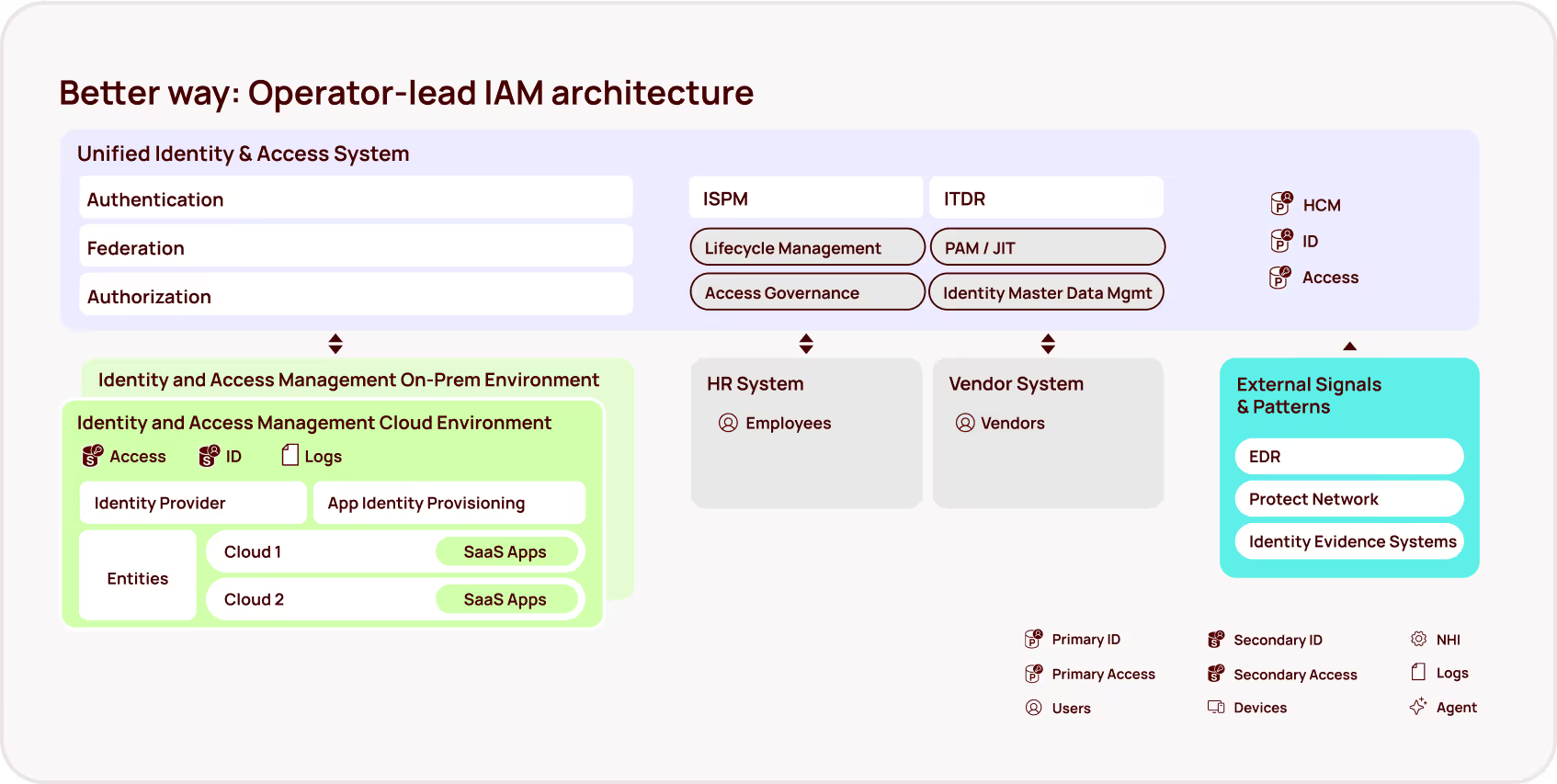
The GitHub configurability paradox
.png)
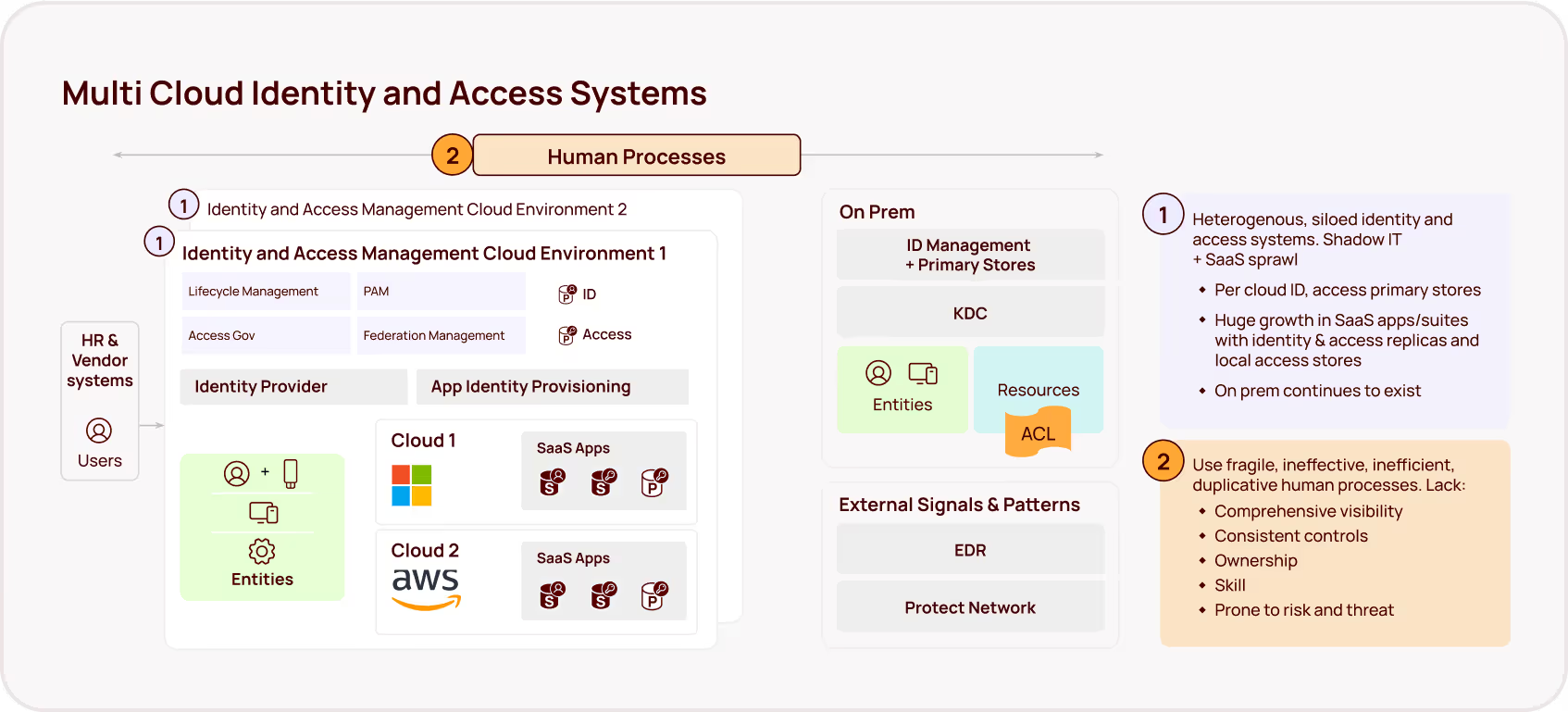
GitHub's greatest strength — its incredible flexibility — has become security teams' biggest challenge. The platform's extensive configurability means that even small changes to deployment settings can have massive, often unexpected impacts on who can access what and how. This complexity creates a perfect storm where security teams struggle to:
- Track permission inheritance patterns
- Audit access effectively
- Maintain least-privilege principles
- Respond quickly to security incidents
Security and IT teams also feel pressure to enable development teams and support their Agile development workflows. Developers want rapid access to repositories, fast onboarding of new users, speedy rollout of new tools — and minimal friction through it all.
Over-provisioning becomes the default leaving risky open doors
This leads to a common but dangerous pattern: over-provisioning access "just to be safe" or "just for now" — temporary solutions that become permanent security risks. In short, misconfigurations around access permissions, repository settings, and workflows can lead to unintended access. Identities have more access than necessary, and security teams often lack the visibility and capabilities to clean up those excessive permissions proactively.
The hidden access crisis: alarming findings
When we audit GitHub and other environments, we consistently find the same dangerous patterns hiding in plain sight that organizations have suspected but lacked the tools to identify. We are able to discover tens or even hundreds of excess permissions, dormant accounts still holding sensitive access, and authentication tokens that never expire.
The scope of this crisis is staggering:
But these aren't just statistics – they're ticking time bombs. Every unused permission, every dormant account, and every excessive access right represents an attack vector waiting to be exploited.
The MFA misconception
Many security leaders look at stats on unauthorized access and think, “We have MFA enabled, we're safe." This dangerous assumption overlooks two unfortunate realities: Many organizations do not have clear visibility to ensure MFA is enabled for all accounts; and not all MFA factors are created equal. While basic MFA provides a layer of protection, modern attackers have evolved their tactics to bypass traditional second factors.
If you're thinking,"We have MFA enabled, we're safe," think again. This guide was created because we've seen too many organizations discover critical identity security gaps only after a breach. By then, their code, credentials, and API keys were already exposed.
Understanding the MFA hierarchy:
- SMS Authentication: Vulnerable to interception and social engineering
- Time-based OTP: Better, but still phishable
- FIDO2/WebAuthn: The current gold standard in MFA
Critical gaps in traditional MFA:
- No protection against authenticated session hijacking
- Limited visibility into access patterns post-authentication
- Bypass potential through personal access tokens
- Inconsistent enforcement across integration points
Building your GitHub defense strategy
Securing identity and access across your GitHub environment requires a multi-layered approach that balances security priorities with developer productivity demands.
[fs-toc-omit]Layer 1: Foundation
The foundation of GitHub security requires attention some critical control areas that can help form your first line of defense. Here is a set of foundational best practices for helping your organization address identity and access risks within your GitHub environment:
[fs-toc-omit]Layer 2: Access Structure
A well-designed access structure is essential for maintaining security at scale and can help simplify management. This layer focuses on creating sustainable, manageable permission systems that grow with your organization while maintaining security integrity.
[fs-toc-omit]Layer 3: Monitoring & Detection
Effective monitoring requires sophisticated tools and well-defined processes to maintain security posture while enabling rapid response to potential threats.
How Oleria simplifies effective GitHub identity security
On the surface, this long list of best practices can look daunting — particularly given how GitHub’s extensive configurability makes it difficult to stay on top of all of these access and identity hygiene principles. More to the point, implementing this framework — and doing it continuously — likely requires a new set of tools and capabilities built for the future that many organizations do not have today.
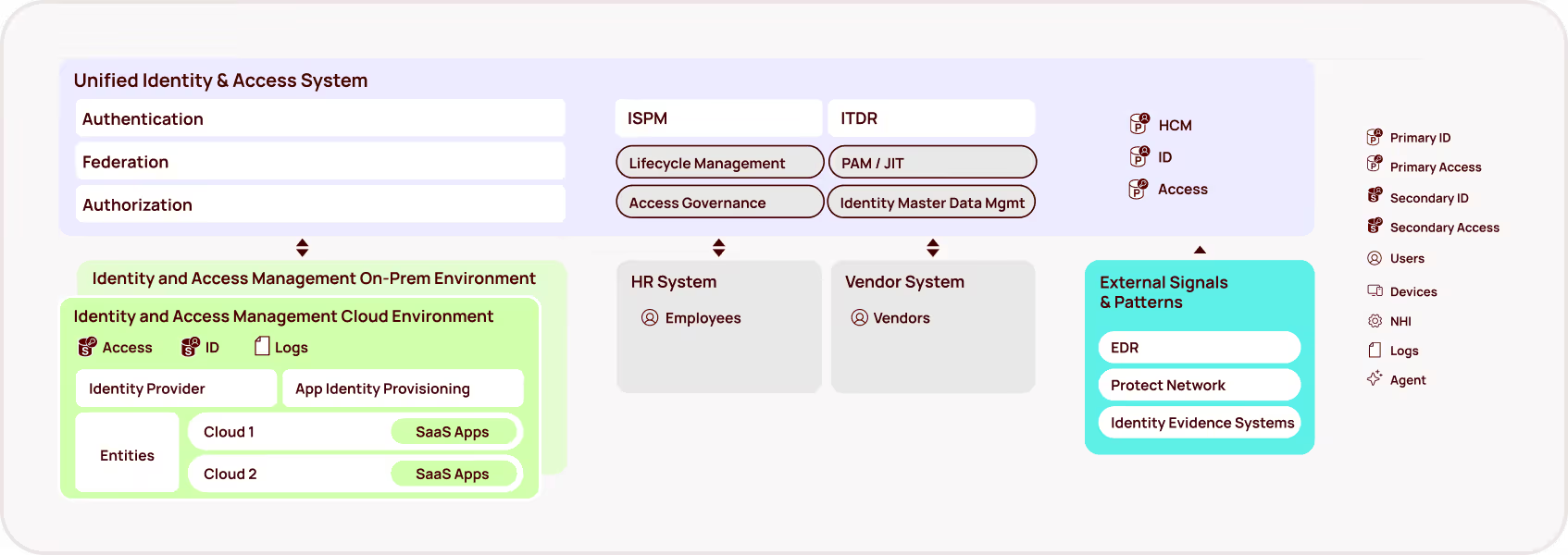
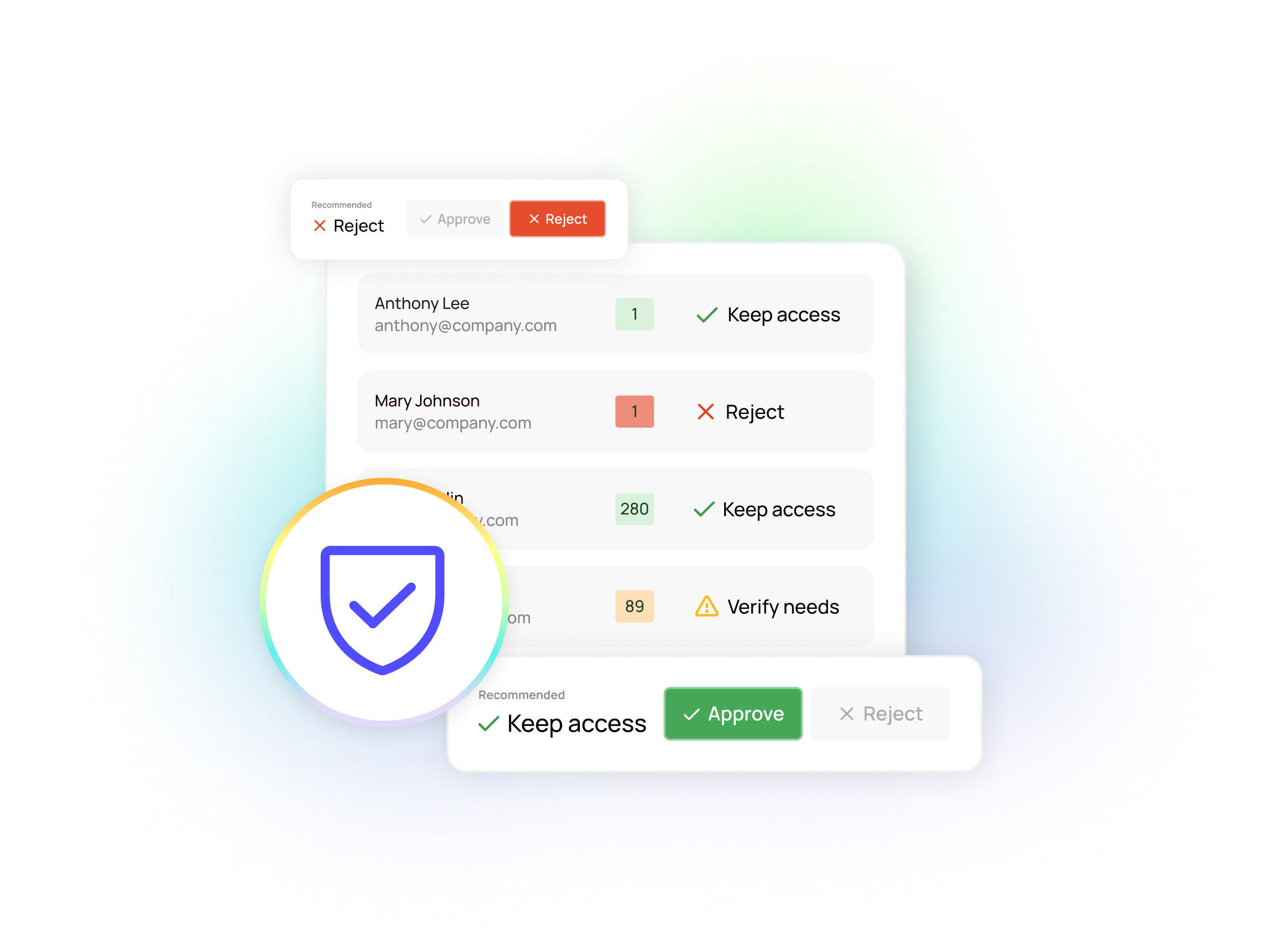
Oleria transforms GitHub security from a manual, time-consuming process into an automated, intelligence-driven system that proactively identifies and mitigates risks. With Oleria you get a single intuitive visualization of all of your GitHub identities and permissions that is plug and play – no long and expensive installation and onboarding.
Intelligent access management
Oleria's platform provides unprecedented visibility into your GitHub environment through sophisticated permission mapping and relationship analysis. The system automatically identifies risky permission combinations, unused access rights, and potential security gaps. Rather than manually tracking permissions, security teams get real-time insights into who has access to what, how that access is being used, and where potential risks exist.
.png)
Risk response
The platform goes beyond simple monitoring by providing rapid incident investigation with fine-grained details options. When risky patterns are detected — whether it's unused permissions, excessive access rights, or suspicious behavior — Oleria can help you implement corrections or initiate review workflows. This proactive approach helps maintain your GitHub security without creating additional work for security teams.

Track group & user activity
Oleria offers a powerful solution to enhance security and streamline access management on GitHub. By automatically tracking user activity and identifying unused or dormant permissions, you can proactively eliminate security risks and optimize your organization's security posture. With Oleria, you can easily identify and remove "ghost accounts," enforce least-privilege principles, and gain valuable insights into user behavior. By analyzing group utilization, you can optimize role-based access policies and ensure that permissions are granted only to those who truly need them.
.png)
A secure GitHub environment
Protect your GitHub environment with Oleria’s comprehensive security solutions, empowering you to understand, identify, detect, and accelerate responses to risks.
Recent articles

Oleria Identity Security: Bringing modern access management to the dynamic enterprise

Heading
.png)
Built for the AI Era: How Oleria’s Unified Identity Security Approach Is Validated by the Industry

Heading




.svg)

.png)

.avif)
.avif)
.avif)