Seven adaptive security trends from the 2023 RSA Conference

Featured event: A CISO’s take
Join Jim Alkove and Ramy Houssaini to learn how forward-thinking security teams are addressing Enterprise AI Copilot risks.
The RSA Conference is one of the most eagerly anticipated events in the cybersecurity industry, and this year was, once again, excellent. As a team from Oleria, we were thrilled to be able to attend and hear directly from leading minds in the field - vendors, customers, government leaders, and analysts alike. We also had the opportunity to share our vision for adaptive and autonomous security with industry professionals and colleagues.
During the conference, we previewed an early version of our product, and we were delighted by the positive response from customers. Listening to their feedback, we noticed several key trends in our conversations. These trends align strongly with what we're building at Oleria, and we believe they will shape the future of cybersecurity.
Whether you attended keynotes, walked the show floor, or grabbed coffee with friends, these seven trends were impossible to miss, and we're excited to be at the forefront of addressing them.
7 trends at RSA that shape the future of Adaptive Security
1. Data breaches continue to be a significant challenge.
Organizations need to secure their data and networks from attackers. This includes implementing asset management, pathing hygiene, and strong access controls. Further, this issue has solidified itself as a boardroom issue, given not only the direct costs of these breaches but the increasingly costly impacts on the companies’ brands and their customers’ trust. Customers are looking for solutions that adapt to their business needs.
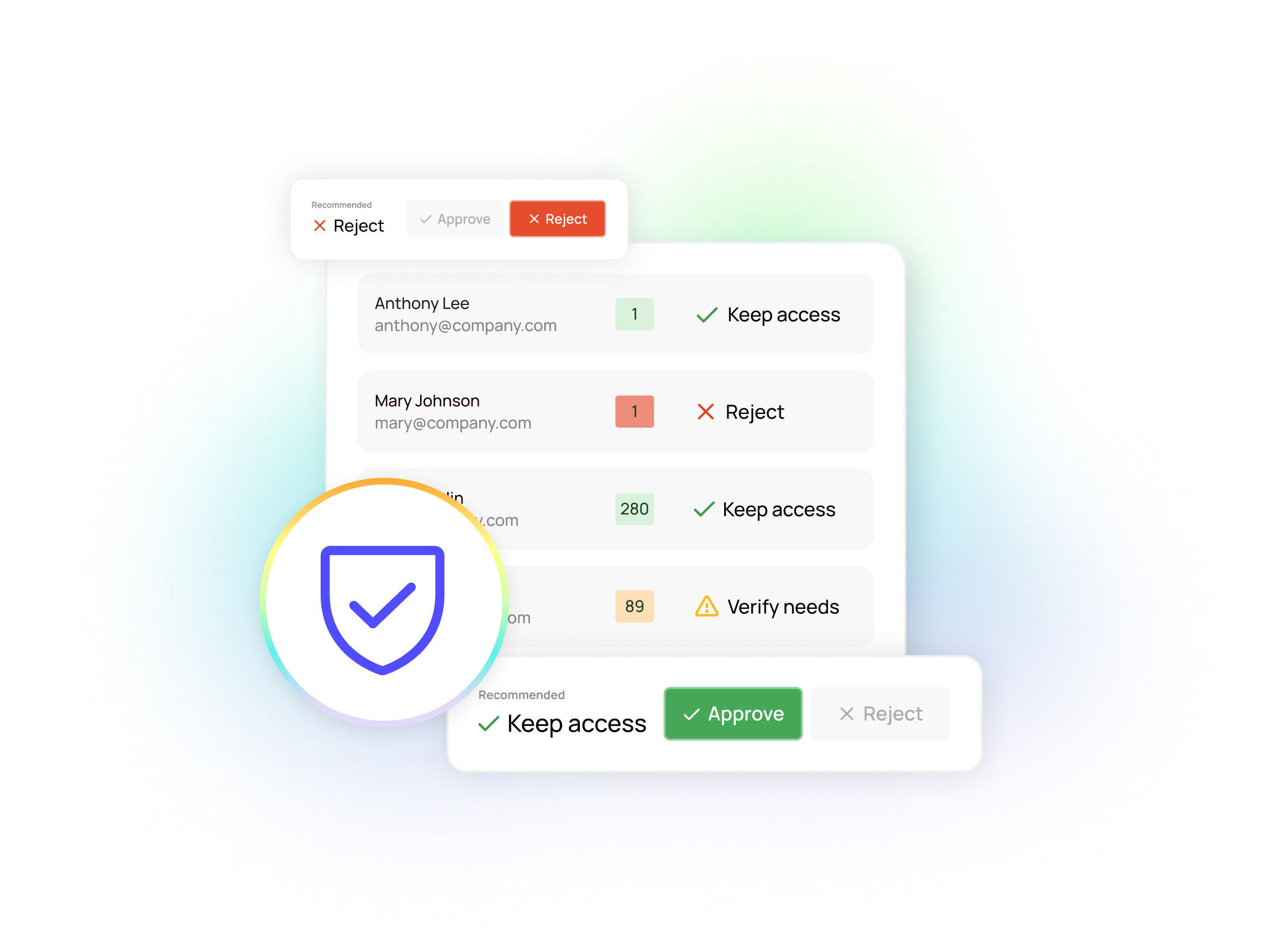
2. There’s a mainstream focus on identity and access management (IAM)
IAM has become an essential component of enterprise security, and many organizations are investing in solutions that enable them to better manage access to their resources and data. However, customers are also wary of the total cost of deploying technologies such as access governance.
3. Zero Trust is more important than ever.
Zero Trust is an approach to security that assumes that all devices, software, and users accessing resources are potentially untrustworthy. As a result, all requests must be verified before granting access. At this year's conference, zero trust was more prominent than ever before, and it was treated almost as a product category instead of being just a feature.
4. Automation is desperately needed to address staffing shortages and rising costs.
Automation helps security teams in many ways, such as significantly reducing the time it takes to respond to a threat. But automation addresses another need as well. Nearly every security team is understaffed. There were over 750,000 cybersecurity job openings in the U.S. alone in February 2023. Deploying sophisticated products that require lots of manual steps and ongoing maintenance simply won’t work when organizations lack the personnel to perform all those steps. Security teams need automation to cover the basics, let alone perform advanced tasks quickly and effectively.
5. Collaboration is key to achieving security outcomes.
Technology is breaking down silos and building bridges between different teams and organizations; we can work towards achieving security outcomes that go beyond simple execution. Effective security requires collaboration across different teams and departments to better understand their needs and enable their success. It also requires collaboration with external partners and stakeholders, like sharing threat intelligence, best practices, and other information that can help improve an organization’s overall security posture.
6. Organizations show strong interest in leveraging artificial intelligence (AI) and machine learning (ML) for security.
Teams want to use AI and ML for a wide range of use cases, including automating security workflows, improving the accuracy of threat detection, and identifying security gaps before they can be exploited by attackers. Vendors and customers alike understand that AI and ML need to be transparent and explainable so that stakeholders can always understand the reason for an AI or ML system’s decisions or recommendations. This is especially important when it comes to identifying and mitigating potential biases in these systems.
7. Graphs are beginning to complement or even replace tables in security dashboards.
Graph analytics, time series analysis, and other data-driven approaches are being increasingly used to quickly identify anomalous behavior patterns and detect potential security threats in real-time. These rich, graphical interfaces are a relief for security teams used to peering at screenfuls of tabular data as they race to understand a possible threat or to take action to remediate an attack in progress.
If we missed you at RSA and you’d like to learn more about what we’ve been up to, please reach out. We’d be happy to hear about your cybersecurity priorities and show our vision for a new approach to IAM. And if you’d like to follow us on our journey to delivering adaptive and autonomous security, follow us on LinkedIn and Twitter.

Built for the AI Era: How Oleria’s Unified Identity Security Approach Is Validated by the Industry

Heading