Why adaptive and autonomous security both protects and liberates today’s SaaS-based enterprise

Featured event: A CISO’s take
Join Jim Alkove and Ramy Houssaini to learn how forward-thinking security teams are addressing Enterprise AI Copilot risks.
The company’s adaptive and autonomous solution liberates businesses from traditional security bottlenecks while fueling collaboration and innovation.
Jim Alkove
Co-Founder and Chief Executive Officer, Oleria
The current digital landscape is highly distributed and rapidly evolving. Businesses depend on interconnected SaaS applications to drive global operations and innovation. However, these cloud-centric architectures put traditional enterprise security models under immense pressure. Based on CISOs and business leaders' feedback, we have already passed the breaking point.
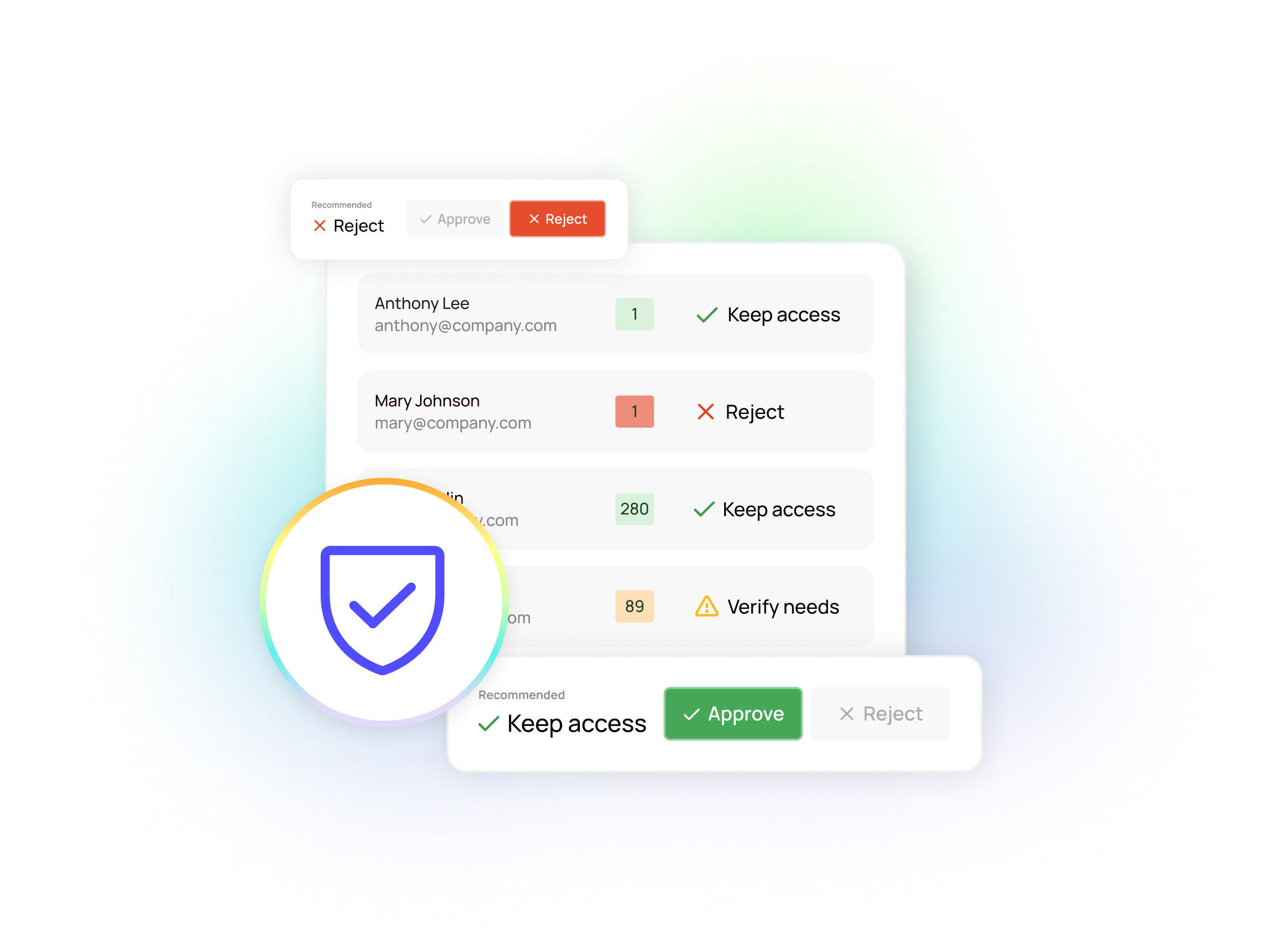
With the typical organization running hundreds or even thousands of applications to support an ever-changing mix of short-term projects and ongoing operations, assigning roles and access on a static basis is no longer sufficient or sustainable.. Modern IT has become a continuous, complex system, adapting dynamically to business needs. Security measures must be continuous and adaptive as well.
At Oleria, we are shifting the focus of our category from fear — the fear of data breaches that causes organizations to become increasingly restrictive — to freedom — the freedom to innovate without rigid security constraints. Security should be adaptive to your organization and sensitive to every context. It should protect data and maintain trust while allowing you to accelerate the pace of business without ever getting in your way.
It's Time for a New Security Model
Most CISOs know we are well past the days of the static and rigid security models.
The perimeter started to become porous a couple of decades ago when cloud applications began to take off. Now, of course, cloud technologies have become standard. Any business will fall behind if it fails to strategically adopt cloud technologies and applications.
Here's our reality, though: traditionally rigid security models simply don’t work in this distributed, dynamic environment. As a result, everyone loses. Security isn’t tight enough, and businesses don’t have the freedom they need to achieve their desired outcomes.
Blind spots caused by a lack of visibility into cloud applications make identifying and addressing access risks challenging. This, coupled with an inadequate understanding of the level of access required to perform tasks, leads to over-provisioning access. The current access governance system is complex and time-consuming, requiring significant manual effort and multiple management tools. It's time for a new model that allows businesses to manage access throughout an application, not just at login.
Without this new model, the consequences will be dire. When information is lost, it's typically unrecoverable, and rebuilding customer trust can take a significant amount of time. Therefore, it’s critical that businesses adopt a more sophisticated approach that provides real-time visibility and granular control over access. By doing so, businesses can ensure they're protected against increasingly sophisticated cyber threats while allowing users to access the resources they need to be productive.
The current static model is no longer sufficient. It's time to embrace a more flexible, adaptive approach to security. Gartner® notes: “By 2026, 70% of identity-first security strategies will fail unless organizations adopt context-based access policies that are continuous and consistent."
Importance of Identity-First Security
In a recent report, Identity-First Security Maximizes Cybersecurity Effectiveness, Gartner highlights the shortcomings of legacy approaches.
We agree that it’s time to switch from outdated, static, perimeter-based security models to a new identity-first security model.
What is identity-first security? It’s “an approach that makes identity-based controls the foundational element of an organization's cybersecurity architecture. It marks a fundamental shift from reliance on static perimeter-based controls that have become obsolete due to decentralization of computing resources, channels, entities (human and machines) and devices."
To achieve identity-first security, Gartner recommends to focus on the following three Cs:
- Consistent: Use centralized policies to control access across decentralized, distributed digital assets in a consistent manner
- Context-sensitive: Use contextual data associated with identities and assets to drive dynamic decisions. Identify what context can be sourced and from where, and make the context available for access controls.
- Continuous: Apply adaptive controls throughout the session, not just at login.
With consistent, context-sensitive, and continuous identity controls, enterprises can better protect people, data, and operations, whether threats target SaaS applications, remote workers, or software development pipelines.
Adaptive and Autonomous Security from Oleria
At Oleria, we fully agree with the Gartner insight on identity-first security. We believe that most businesses will too, if they haven’t already.
Businesses will have this lightbulb moment for two reasons. First, data breaches continue to increase in frequency and impact. The top-down, rigid approach to security clearly isn’t living up to its promise of protecting enterprises, data, and people.
Second, I have witnessed firsthand the increasing complexity of access management and access governance, despite organizations spending countless resources and time requesting, approving, and managing access manually. But these organizations are still vulnerable to data breaches due to the decentralized ownership of access and the difficulty of building the right access posture.
In the past year or so, it became obvious to me that there had to be a better way. That’s why Jim Alkove and I co-founded Oleria. With our decades of experience leading security teams within large and complex organizations, we’re excited about the impact we can have on organizations' security posture. Our vision is to help organizations reduce access management and governance complexity and ultimately make the world a safer and more trustworthy place for all.
What does that safer world look like?
It’s a world that changes that cautionary “No” to an enthusiastic “Yes, here’s how.”
It’s a world that lets organizations move as fast as they want, leveraging all the amazing new cloud technologies and data available today to achieve their boldest ambitions.
At Oleria, we know from experience that traditional security products can create more work and strain collaboration between business and security teams, making it difficult for them to try new things.
That's why we are developing an adaptive and autonomous solution that brings security practitioners together to achieve optimal security outcomes while enabling faster innovation and preserving trust.
Our solution aims to break down boundaries and create bridges to promote effortless collaboration, reducing the burden of operational tasks and remediations so that our customers can focus on driving business outcomes. Plus, our solution will constantly learn and improve so that organizations can stay ahead of evolving threats without sacrificing agility.
Instead of holding businesses back in the name of security, our solution helps them move faster than ever, freeing them to collaborate and reshape technology as quickly as they like, confident that their data is safe.
So if you're ready to take your security to the next level, let's talk.

What a 58% IGA failure rate tells us about the future of identity governance

Heading

.png)