A smarter approach to managing sharing at scale
CISOs know over-privileged and unintended access are big problems. Learn how Oleria gives you a single point of control to right-size sharing permissions across your IT estate.
.avif)
Featured event: A CISO’s take
Join Jim Alkove and Ramy Houssaini to learn how forward-thinking security teams are addressing Enterprise AI Copilot risks.
File sharing is a growing elephant in the room for CISOs. It’s essential to productivity and collaboration today, so there’s no slowing it down. But when it comes to gaining visibility into file sharing across their IT estate, I’ve seen CISOs throw their hands up in frustration.
Most organizations struggle to see when employees mistakenly over-share sensitive information internally and externally. They don’t know (until it’s too late) when departing employees sneak IP out through self-sharing. They can’t effectively offboard vendors, leaving dormant shares open to exploit. And they can’t crack down on the rampant self-sharing among vendors and contractors that vastly expands the risk to business-critical documents.
Why can’t most organizations stop these sharing risks? Because security teams do not have a central point of control to find the simple answers they need: Who has access to what? How did they get it? And what are they doing with it?
Without easy visibility, file-sharing risk gets swept under the rug
How big is the file-sharing risk that security teams struggle to see? A report from Concentric AI found that 16% of the typical organization’s business-critical data is overshared — totalling 802,000 at-risk, overshared, business-critical files in every organization, on average.
But the harsh truth is that the business value of file-sharing largely overshadows the risk in many organizations. Moreover, the lack of central visibility means that security teams can’t even wrap their heads around the magnitude of that risk.
Instead, what represents the best attempt at orchestrating secure sharing hinges on an inelegant swivel-chair approach: security teams are manually jumping from the directory system (Active Directory or Okta) to each and every application (Salesforce, ServiceNow, Oracle, SAP, etc.), one by one. It’s chaotic. It’s inefficient. It’s stressful. And it still doesn’t give security teams the visibility and answers they need.
Oleria provides a central point of visibility and control for internal & external sharing — across your IT estate
We built Oleria’s Trustfusion Platform to deliver on one need, above all else: Create centralized visibility across the entire enterprise IT estate, while providing the level of granularity and control needed to act on the insights from that visibility.
In the case of secure sharing, Oleria eliminates the swivel-chair approach, instead fixing your chair in front of a single point of control for managing access across your IT estate.
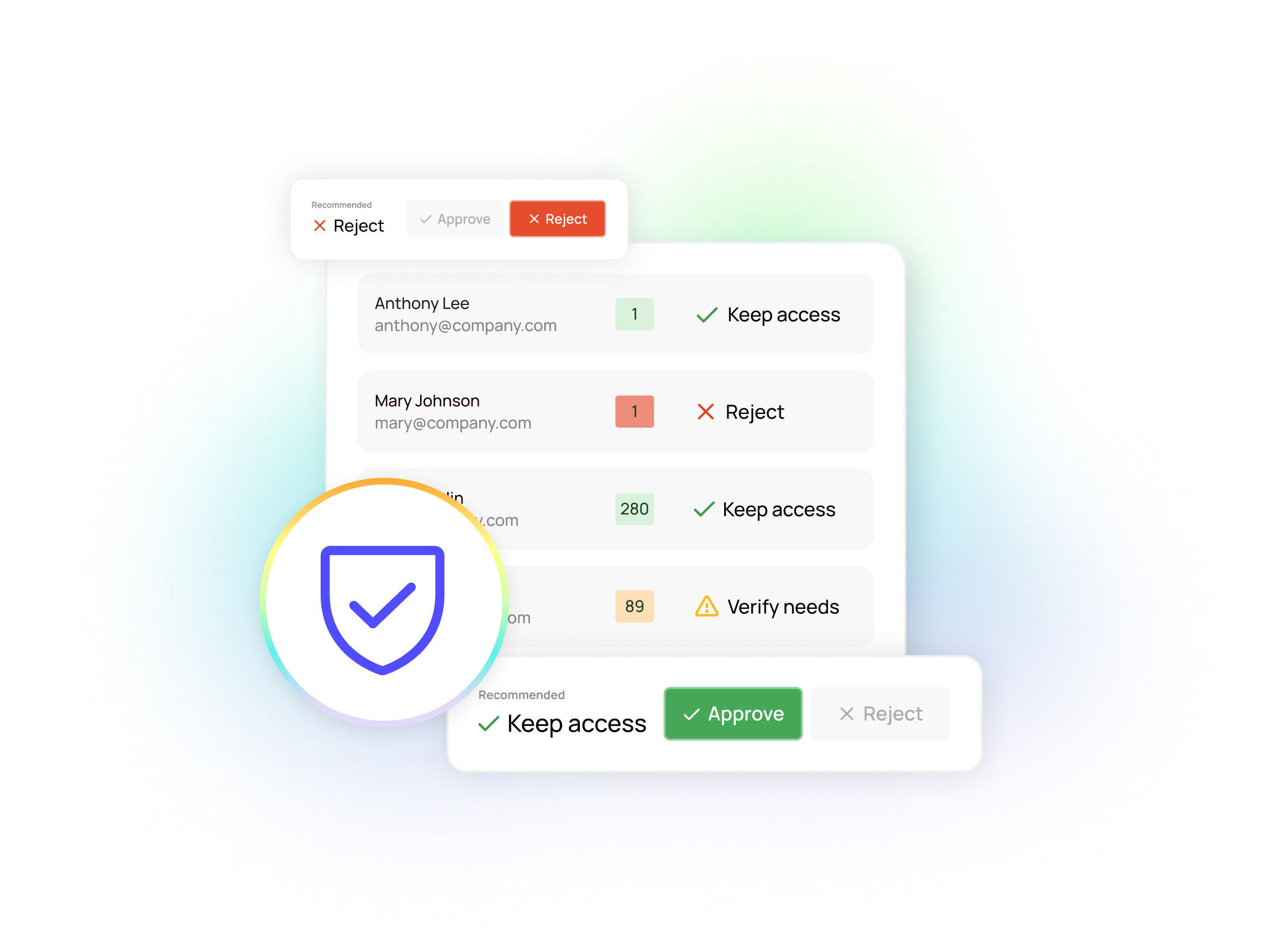
Oleria provides a composite view of access permissions, including centrally and decentrally provisioned access, all the way down to the specific permission on the individual resource — including detailed usage information. This in and of itself saves a lot of time and a lot of stress for security and IT teams.
Surfacing the biggest sources of file-sharing risk
Visibility is powerful, but we all know that unfiltered visibility is often just overwhelming. CISOs need tools that make it easier and faster for their teams to separate risky shares from the sea of necessary sharing — and they also need tools that cut down the gap between intelligence and action.
Oleria makes it easy to focus on some of the biggest and most common sources of risky sharing — like inadvertent over-sharing, departing employees taking files, dormant shares with long-gone vendors, and self-sharing among vendors and contractors.
Within Oleria Identity Security, you can use smart filters to hone your focus.
- Departing or high-risk employees: Key in on a short list of departing or high-risk employees and easily see if they have self-shared documents with personal accounts.
- Offboarded vendors: Filter by all external users, or even filter by a specific email domain, to control your third-party access risk.
- Highly sensitive files: Oleria makes it easy to pull up that specific file or asset and see a full list of all users with access, so you can figure out who might not need (or perhaps shouldn’t have) access.
- Dormant shares: Oleria also makes it simple to surface dormant shares — files that were shared with other entities, but those entities have not accessed the files in a long time (or never). In Oleria, you can define a dormancy period, based on a number of days, and then see all shares that have not seen activity within that period. This dormancy is a good indicator that the sharing is no longer necessary, or was unintentional, so you can revoke those shares and close those open doors.
Of course, finding risky shares is one thing; but CISOs can’t require their teams to go back into each specific application and find the exact permissions to revoke. Oleria lets you revoke access with a few clicks — for a specific user and specific file; for a group of external users; for all users with an associated domain; for all dormant accounts; etc.
These are the purpose-built capabilities that I see security teams get really excited about, because they can save a tremendous amount of time — and act on risky sharing much, much sooner.
Empowering the flow of information — without adding risk
Enabling seamless access to information — while keeping the organization safe from the growing challenges of identity-based breaches — is a fundamental mandate for CISOs. The challenge here is that “access to information” now encompasses an enormous and rapidly growing landscape of more channels, more apps, more machines, and more human identities.
Secure sharing is probably the most visible frontier of this push and pull. You can’t default to “yes,” nor can you over-rotate to “no” on sharing permissions with internal users, customers, and third parties.
Right-sizing sharing permissions needs to start with comprehensive, single-pane visibility. Once you understand the breadth and depth of your sharing landscape, you can find and address your high-risk exposures, allow the business to move quickly and share information in agile ways, without opening the door to risk.
Ready to learn more? Schedule a demo.

Built for the AI Era: How Oleria’s Unified Identity Security Approach Is Validated by the Industry

Heading