Untangling the constellation of group access
Discover how Oleria Group Utilization addresses overprovisioned group and role-based access, providing organizations the ability to see exactly who is (and isn’t) using permissions within a group.

Featured event: A CISO’s take
Join Jim Alkove and Ramy Houssaini to learn how forward-thinking security teams are addressing Enterprise AI Copilot risks.
Untangling the constellation of group access
In the modern enterprise, new employees can’t be productive until they have access to the essential apps and systems where work happens. So, it’s no surprise that companies want to streamline employee onboarding and get users the access they need as quickly as possible.
Most fall back on common shortcuts: role-based permissions implemented using group memberships. Instead of the tremendous burden of granting access one app or resource at a time, the new user gets added to the relevant groups to create the constellation of access that their role may need — whether they actually do or don’t.
Access compliance reviews are supposed to be one remedial step to reign in unused permissions. But the tools available provide little, if any, context around access utilization. So, managers can’t make effective, data-driven decisions about whether group members should maintain their specific access privileges.
Most CISOs and security leaders know this role-based access shortcut is perhaps the biggest contributor to the rampant and risky problems of overprovisioned, unintended and dormant access. The problem is that they can’t see those unused permissions. And if you can’t see it, it’s hard to do anything about it.
Organizations do not have clear understanding of access utilization
Microsoft tells us that 95% of permissions are unused in the typical organization — and that 90% of identities are using just 5% of their granted permissions. It’s easy to see why role-based permissions based on group memberships are among the key root causes of this overprovisioning and unintended access: Just because one member of the HR team needs access to the payroll system does not mean the entire HR team needs access. Moreover, just because that HR employee needs access to the payroll system does not mean they need full admin privileges.
Like I said, security leaders largely know this is a flawed approach. They know they have risky open doors in the form of overprivileged access and dormant accounts. Until now, there hasn’t been a solution that allows security teams to easily see which members of which groups are actually using each of their permissions. So, identifying those unused or underutilized permissions and accounts would require an extremely time- and cost-consuming manual audit — across each and every app in their IT estate. Most simply don’t have the available resources to justify this — unless or until a breach or other incident forces a focus on the issue.
How to provide actionable visibility to group and role-based permission utilization
When I describe the visibility that Oleria provides as “powerful,” I’ll admit that it can sound like marketing speak. But when I start to tell CISOs about all the ways they can use this visibility, they see I’m not overselling it.
Case in point: Because the Oleria Trustfusion Platform brings together a composite view of access permissions across the enterprise IT estate, we can channel that comprehensive visibility into actionable information on account and access utilization.
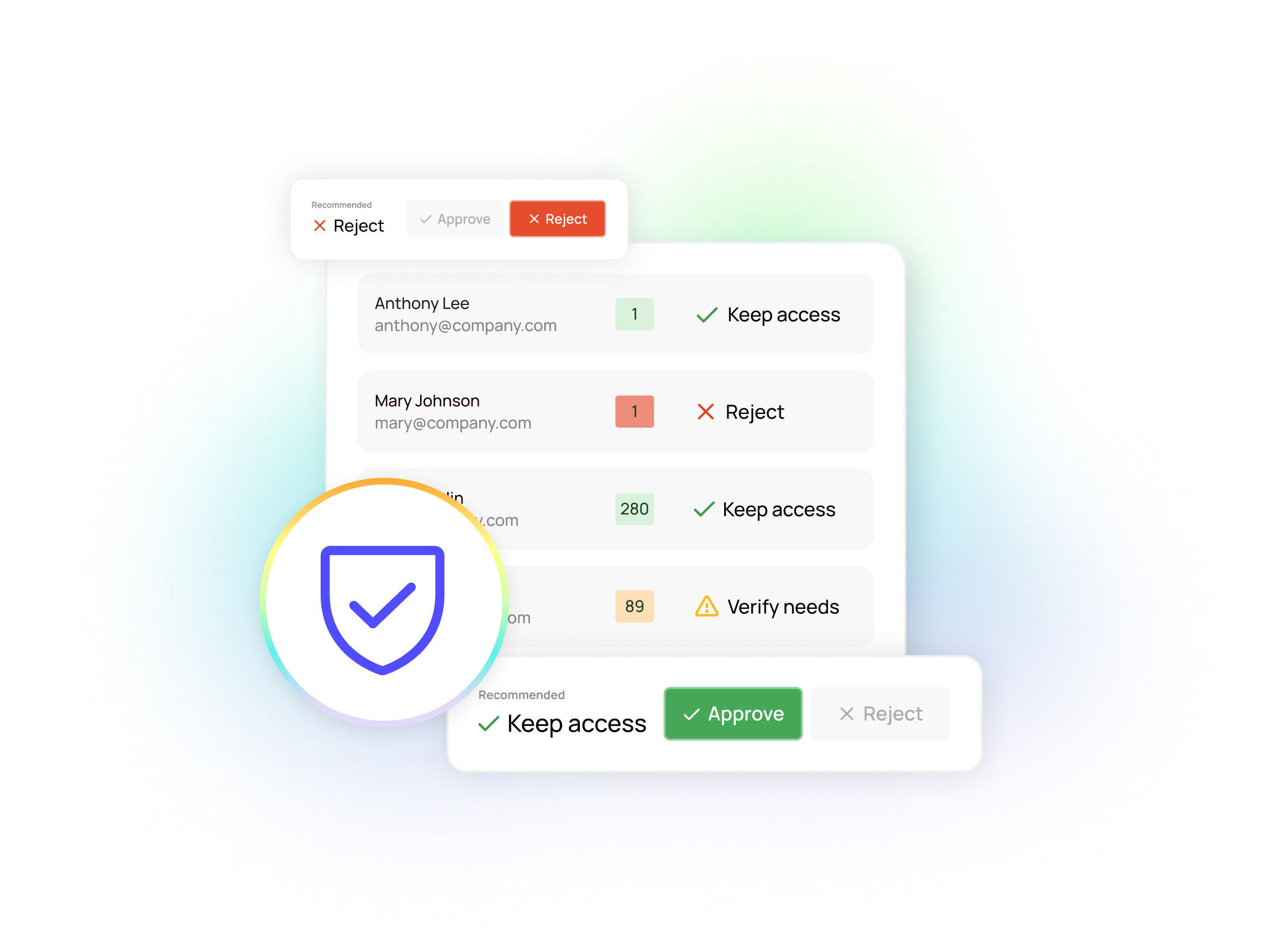
We built the Group Utilization feature specifically to address the issue of overprovisioned and unintended group access. We’re giving organizations the ability to see exactly who is (and isn’t) using permissions within a group — including fine-grained visibility of when an individual last used access, and what they did with it (down to the specific file or resource level).
That resource-level usage monitoring is the key ingredient, because it solves the main problem with conventional means of access review: Lots of security teams try to use Active Directory to monitor usage. But AD tokens often do not refresh for days (or even weeks), making dormancy analysis pretty much impossible. By contrast, Oleria gives you a near-real-time answer to the question, “When did this user last interact with this app?”
This level of fine-grained visibility is something I could never get easy access to when I was a CISO — certainly not across multiple applications in one single view.
Oleria automatically surfaces unused permissions
We know from experience that security and IT teams are already stretched thin and don’t necessarily have time to manually work through logs and group access graphs. So, Group Utilization automatically flags unused permissions, along with flagging groups with a low percentage of active use.
This makes it simple and quick to enforce least privilege principles by removing unused accounts and moving from role-based access based on group memberships to providing more targeted individual-level permissions to the critical, high-utilization users. In other words, Oleria makes it easy to ensure the people that really need access have it — and those that don’t, do not.
I cannot stress how much of a no-brainer this is: These are permissions and accounts that we know users are not using and do not need to get their work done. Eliminating these unused permissions is one of the few instances in cybersecurity where taking action brings literally zero downsides. You’re dramatically reducing the risk surface area while not impacting end users or the business in any negative way.
Closing security gaps — without slowing down the business
It’s tempting to look at this situation and say it’s the approach to onboarding that needs to change — that organizations shouldn’t be taking the role-based permissions shortcut. And we’re hard at work developing additional functionality that can help to address the front end of the group provisioning problem — making it faster and easier for IT teams to grant more fine-grained permissions in the first place.
Yet, there’s no question that role-based permissions based on group memberships will remain a pragmatic approach to accelerate onboarding, because the modern enterprise lives and dies on the delicate balance between enabling speed and agility, while mitigating risk.
With Oleria, we’re making it easy to identify and remove the 95% of access that we know people are not using. So, CISOs have a reliable way to close these open doors and significantly decrease the risk to their organizations — without slowing down employee onboarding and with zero impact on productivity and business operations.
.png)
Built for the AI Era: How Oleria’s Unified Identity Security Approach Is Validated by the Industry

Heading