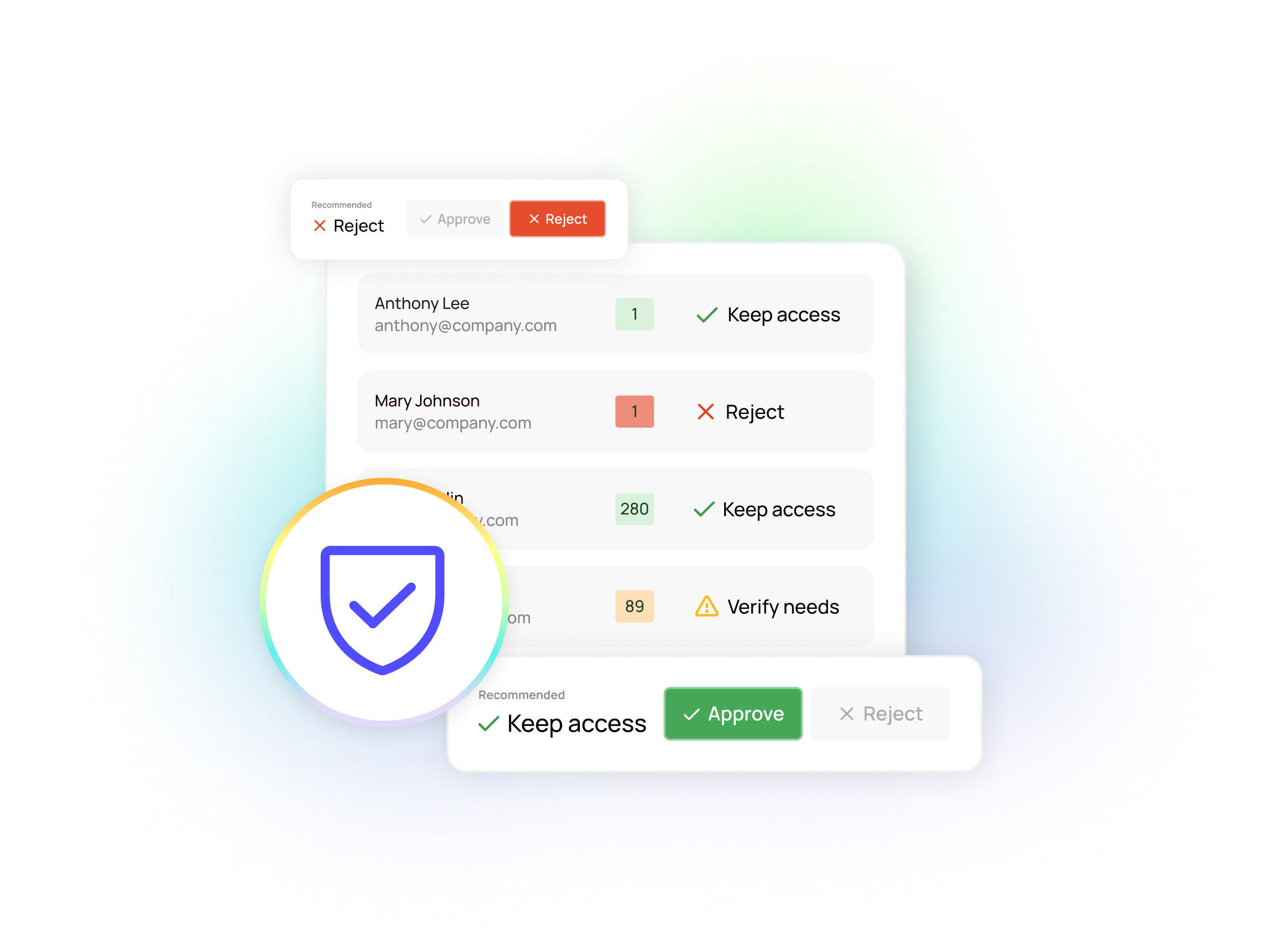
Incident response and data leak investigation in seconds — not days
Investigating data leaks can be time consuming and difficult, but it doesn’t have to be. Here is how you can get critical data leak answers in seconds: where a sensitive or confidential file lives, who has access to it, and what they did with that access.
.avif)
Featured event: A CISO’s take
Join Jim Alkove and Ramy Houssaini to learn how forward-thinking security teams are addressing Enterprise AI Copilot risks.
Discover how Oleria provides critical data leak answers in seconds: where a sensitive or confidential file lives, who has access to it, and what they did with that access.
Here’s a situation every CISO dreads: You get a call — seemingly always late at night — that you’ve had a breach. Hopefully, it’s someone from your security team. But sometimes, it’s the CEO in a panic, a reporter calling for comment, or (worst case scenario) a customer calling about an already-published news story.
You can hardly go a week without a major breach in the headlines — from consumer brands like Change Healthcare to AT&T to tech giants like Snowflake and Microsoft to some of the same companies that build modern cybersecurity solutions.
These calls have become almost inevitable — a question of when, not if. Breaches keep increasing, despite rising security spend, in part because the threat landscape keeps getting more complex: more apps and more tools mean new risks and new attack tactics.
You’ve been breached — now what?
As a CISO, I got that dreaded call more than a few times. And the first thing I wanted to know was simple: Who has access to the breached information? Where did they get that access? And what have they done with that access?
These seem like straightforward questions. But I knew that it was likely going to take me and our incident response team at least long hours (if not a few days) to get those answers. And that was with as much of a state-of-the-art security tech stack and highly mature security posture as any organization.
The stress in that period is intense — for everyone. And I know that most of my CISO colleagues have felt the same pain because I can see it in their eyes when we share stories.
Lack of visibility is the biggest flaw in incident response
Those simple questions (Who? How? What?) outline the core problem with incident response today. Cyber Security Incident Response Teams (CSIRTs) don’t have the centralized and fine-grained visibility they need to quickly and easily answer those questions.
Instead, they have to manually pore over piles of access logs to find three things:
- Where the breached information (data, file, etc.) lived — which might exist on multiple systems and applications, in multiple locations within an app, and in multiple versions.
- Who had access to each of those instances or locations of the information — requiring them to wade through different access control frameworks for each system or application to understand the different access paths (usually multiple) a particular user might be able to take to get to that information.
- What those users with access to the information had actually done with that access. Who recently accessed the file? Who shared the file? Who copied it, downloaded it, moved it, etc.?
On top of these distinct, manual needle-in-the-haystack searches, CSIRTs have to translate the log-speak into human-readable language. And then piece together the story of what happened.
This manual process takes far too much time — when time is of the essence. And these are not situations where you clock out at 5pm and pick it back up in the morning.
Moreover, this painstaking manual investigation overstrains security teams that are already typically stretched thin across a rapidly expanding threat landscape. And staff burnout only exacerbates the whole situation.
Oleria gives you critical answers in seconds not days
Oleria changes all of that. Because Oleria was built by security operators who know the stress and impacts of leak investigation, we created a solution that gives you critical answers in seconds: where a sensitive or confidential file lives, who has access to it, and what they did with that access — to dramatically accelerate your incident investigation and response process.
What does that automated and accelerated incident response look like with Oleria?
1) Pinpoint where a breached file lives.
Oleria gives you one centralized, composite view across your identity stack, SaaS platforms and applications. You can search for the file in question and instantly see (every)where it lives within your IT estate. This is the instant foundation you need to start your investigation and response.
2) See exactly who has access to the breached file — and how.
Oleria’s Access Graph gives you an immediate, intuitive visualization of access paths to the file or asset in question. You can immediately see which users have access permissions and where they got them, greatly narrowing your investigation on the right users and identities. No more manual needle-in-the-haystack searching.
3) Identify risky activities immediately.
With Oleria’s fine-grained visibility, we can tell you each and every transaction — every read and every write — that happened on a breached file during the time period in question. You can instantly see whether (and what) risky or malicious actions were taken related to the breached file. This is the critical insight you need to kickstart your response, based on what actually happened to the information in question (rather than a worst-case scenario estimation).
4) Revoke access instantly.
We built Oleria not just to solve the visibility problem, but to give you the functionality you need to respond faster. This starts with closing any risky open doors. Whether that means revoking all access for a single compromised user, revoking access for a breached third party, or temporarily revoking all access to a breached file or system, Oleria turns what used to be a slow, manual process into a rapid response in just a few clicks.
5) Remediate identity security gaps.
Oleria is a powerful tool for incident response, but it’s even better when used proactively. We help security teams enhance security resilience with targeted insights that highlight identity security gaps and strengthen security posture to prevent future breaches:
- Account Utilization + Group Utilization: Understand how identities are using their access permissions, identify underutilized or dormant permissions, and enforce least-privilege principles.
- Activity Analysis and Risk Monitoring: Surface anomalous user activities to enable even more immediate, proactive response.
Is your incident response plan keeping up?
The pace of breaches isn’t slowing. CISOs are getting those panic-inducing calls more frequently. So, while CISOs and their teams must continue working to prevent breaches, they need to put at least as much emphasis, budget, and resources behind building out a modern cyber incident response program.
Moreover, the question now isn’t, “Do you have an incident response plan?” It’s, “Can your incident response plan handle the volume, velocity, and complexity of today’s risks and attacks?”
Want a deeper look at how Oleria plugs in to fill gaps in incident response plans? Check out this use case
.png)
Built for the AI Era: How Oleria’s Unified Identity Security Approach Is Validated by the Industry

Heading