Ensuring multi-factor authentication coverage across your SaaS estate
See how Oleria gives you clear visibility on where MFA is enforced (and where it is not) across your SaaS estate — in minutes, not days or weeks.

Featured event: A CISO’s take
Join Jim Alkove and Ramy Houssaini to learn how forward-thinking security teams are addressing Enterprise AI Copilot risks.
I’m pretty sure I don’t need to explain, “Why multi-factor authentication?” to anyone reading this blog. But one of the biggest challenges I faced as the Chief Trust Officer at Salesforce was simply understanding where we had multi-factor authentication (MFA) enforced — and where we didn’t — across our growing footprint of SaaS apps.
I wish I had Oleria then. I’ll tell you why.
Finding MFA gaps keeps getting more difficult
MFA has long been recognized as a critical layer of security — like I said in my earlier Forbes column — and it’s unfortunately more important than ever. Poor password hygiene remains rampant, and the immense computing power at hackers’ fingertips means they can crack even strong passwords with relative ease and speed.
Ask any CISO if they have MFA setup and — at the enterprise level, anyway — the answer is almost universally, “Yes.” Roughly 9 in 10 large organizations use it today, according to a 2023 report. Yet the reality of MFA deployment is never that clear cut.
To boost speed and agility, organizations have moved toward a more decentralized model of app deployment. Business units decide what apps they need, and security teams are often brought in late in the deployment process — if at all.
Nevertheless, the responsibility for MFA enforcement almost always lies with CISOs and their teams. And in this decentralized SaaS environment, it gets challenging just to understand all the apps currently deployed, much less answer the question, “Where is MFA enabled — and where is it not?”
These gaps can have big consequences: Both the SEC and Mandiant (a leading cybersecurity firm) recently experienced hacks that stemmed from gaps in MFA coverage, not to mention probably the most prominent recent intrusion at Microsoft (aka Midnight Blizzard).
Manual multi-factor authentication reporting can’t keep up
With siloed SaaS estates, monitoring MFA coverage today requires diving into each and every app’s admin control panel — understanding how that admin functionality works and how to get an overview of status for all accounts. This is a manual, time-consuming workflow.
The best option most CISOs have right now is to look at manually generated reports. This approach is error-prone, since it’s easy to miss things when you’re reliant on manually combing through app after app. And the info in the reports is often a week old by the time it hits the CISO’s desk.
The issue of outdated information points to a bigger problem: Organizations need this level of monitoring to be continuous. New apps and new accounts are being added constantly, and users/admins modify multi-factor deployment for various reasons. In fact, in the Mandiant hack, the multi-factor authentication gap resulted from recent changes in how the X (formerly Twitter) policy works. So, a manually generated point-in-time report could give companies in Mandiant’s situation a false sense of security based on out-of-date information.
Oleria highlights your MFA gaps — across your SaaS estate in minutes
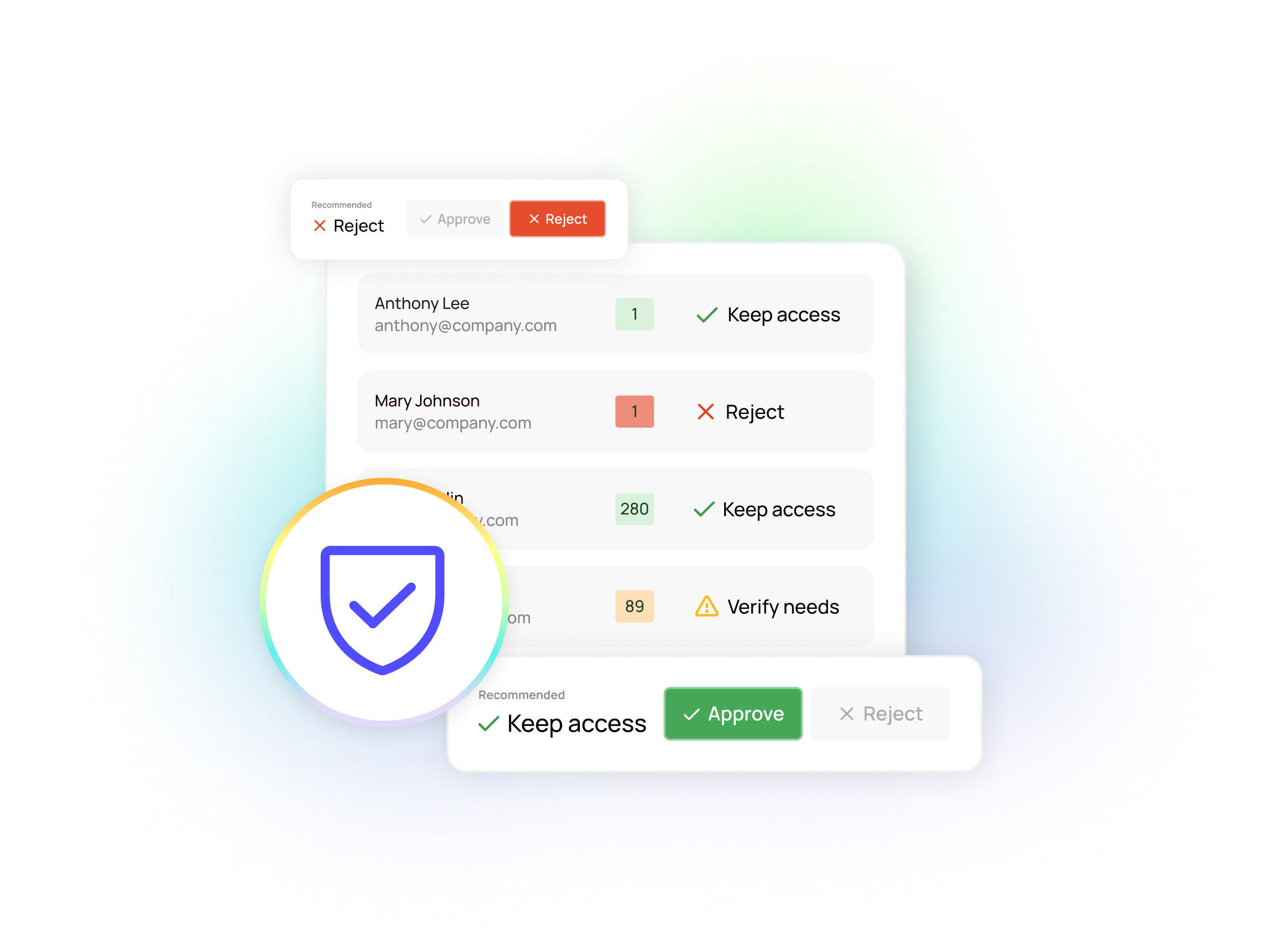
The most fundamental value of the Oleria Trustfusion Platform is how it provides a composite view across your identity access management (IAM) and SaaS estate. That single, centralized view allows Oleria to do a lot of important things to enhance identity security. But one of the highest-impact and easiest ways to use Oleria is to see and plug your MFA gaps.
Because the Oleria platform automatically aligns all integrated SaaS apps under one consistent access control schema, you can see MFA status for all apps and all accounts, all in one place. Moreover, the Risk Monitoring capability can also automatically look across all those apps and highlight MFA gaps.
The value to CISOs is immediately clear: Oleria gives you a real-time, composite understanding of MFA coverage — without having to dedicate significant weekly time to generating manual reports.
The next level: stepping up to phishing-resistant MFA
Let’s be clear: Any MFA is always better than no MFA. However, not all MFA factors are created equal. Legacy MFA such as email and SMS have significant security vulnerabilities. First, these MFA factors use communications systems that themselves can be hacked. Second, their use of user-inputted codes makes them more easily "phishable."
We’re seeing a rising incidence of cyberattacks cracking MFA. In fact, the SEC hack stemmed from an MFA compromise. And Generative AI promises to make these attacks even more successful, making it easier for malicious actors to generate convincing messages at scale.
This is why I’ve been pushing for stronger, phishing-resistant MFA for years now: adding factors like push notifications to trusted devices, hardware tokens, and biometric authentication.
As phishing-resistant MFA becomes the new standard — and SaaS vendors increasingly uplevel to support more sophisticated, phishing-resistant MFA factors — it will amplify the urgency of understanding your MFA coverage across your entire SaaS estate.
The core lesson is an important one: Having the security tools or functionalities is not enough; CISOs need to be able to monitor and validate that critical security layers are actually being used. And that starts with bringing holistic and fine-grained visibility into accounts and access architecture — all in one place.
Get a modern view of your organization’s MFA deployment: schedule a demo.
.png)
Built for the AI Era: How Oleria’s Unified Identity Security Approach Is Validated by the Industry

Heading