Oleria provides identity security and access management teams with visibility and intelligence into who has access to what, where they got that access, how they use it, and whether they should even have it. As part of that promise, we deeply integrate your Ping Directory into the Oleria platform. Follow these steps to integrate Ping Directory with your Oleria workspace
Pre-requisites:
1.Administrator permissions on the Oleria workspace.
2.Administrator permissions on the machine where PingDirectory will be installed.
3.Administrative access within PingDirectory to create a user.
4.If PingDirectory is hosted on one machine and the agent is deployed on another, it is essential to ensure that both VMs can communicate with each other without any firewall restrictions blocking the connection.
Step 1: Create a Service Account in Ping Directory
This process involves creating an LDIF file to define the new service account and its permissions, then using the ldapmodify command to apply these changes to the directory.
1.1: Create the LDIF File
An LDIF (LDAP Data Interchange Format) file is a plain text file that contains a series of instructions for adding, deleting, or modifying entries in an LDAP directory. The file you'll create, create_readonly_user.ldif, will perform these specific functions:
- Create the Service Account: A new user entry will be created with the UID (User ID) readonlyoleriauser and the common name Read Only User. The inetOrgPerson object class is used, which is a standard object class for representing people in an LDAP directory.
- Assign Read-Only Access: The most critical part of this file is the ACI (Access Control Instruction). This instruction grants the readonlyoleriauser account read and search permissions on all attributes within the entire directory subtree. This is what makes the account "read-only."
The content of the create_readonly_user.ldif file is as follows. Remember to replace <replace-with-your-base-dn> with your directory's base distinguished name (e.g., dc=example,dc=com) and Oleria@5 with a secure password.
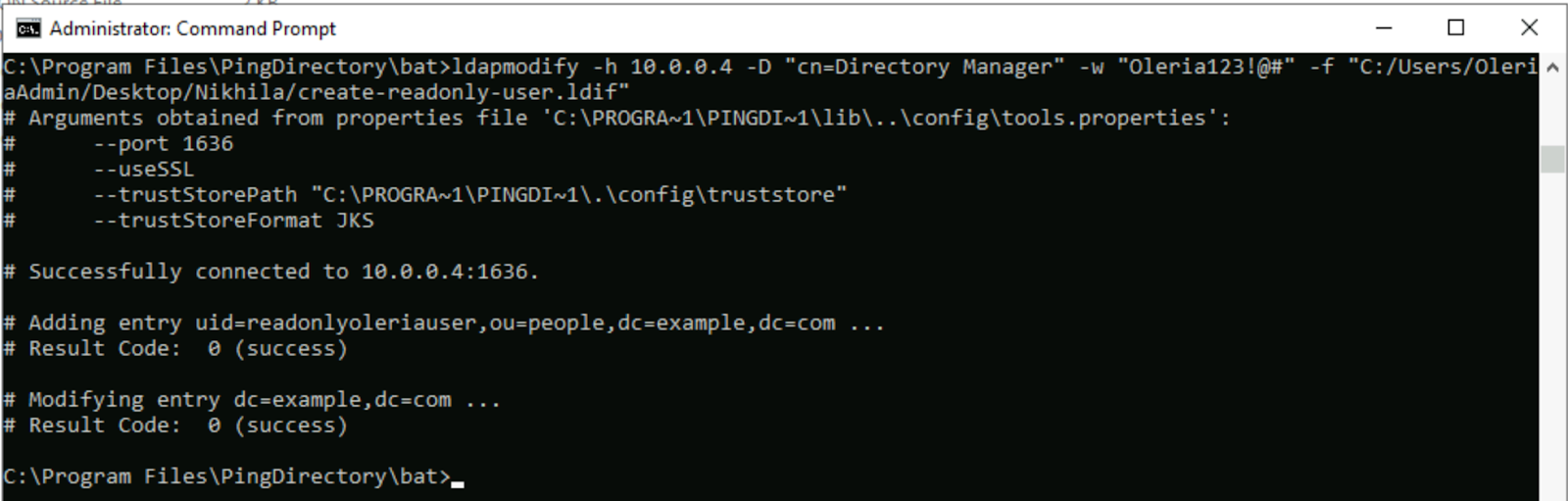
1.2: Execute the LDAP Modify Command
After creating the LDIF file, you need to use the ldapmodify command-line tool to apply the changes to your Ping Directory instance. This tool connects to the directory using an administrative account and executes the modifications defined in your LDIF file.
To execute this, open a command prompt, navigate to the bat directory inside your Ping Directory installation, and run the following command as a single line:
- <hostname>: The hostname or IP address of your Ping Directory server.
- "cn=Directory Manager": The DN (Distinguished Name) of the administrative user with the necessary permissions. The default administrative user is cn=Directory Manager.
- <password>: The password for the administrative user.
- create_readonly_user.ldif: The path to the LDIF file you just created.
Step 2: Configure Syslog-Based Forwarder
This step uses the dsconfig command-line utility to configure a syslog-based log forwarder in Ping Directory. This is crucial for forwarding directory logs to a centralized log management system, like Fluentd, for monitoring and analysis. The provided command enables a publisher named "Fluentd Syslog Access Logger" and configures it to log a wide range of operational events, including search entries, security negotiations, and client IP addresses.
To execute this, open a command prompt, navigate to the Ping Directory installation's bat directory, and run the following command as a single line:
Please replace <IP-ADDRESS-OF-AGENT-MACHINE> with the IP address of the machine where the agent is running.
Step 3:Integrate Ping Directory with your Oleria workspace
Log in to your Oleria workspace and select Workspace > Integrations → Ping Directory
Provide a name for your agent and click continue.

You will see a PowerShell Script with a copy option. You need to execute this script on a server where you want to install the Oleria PD Agent.

Step 4:Install Oleria PD Agent
Log in to the machine, open PowerShell with administrator privileges, and run the script downloaded from step 2.
4.1 You will see the Fluentd installation process
Accept the license terms and select Next
Follow any subsequent prompts to complete the installation.
Before proceeding with the agent installation, we need to update the Fluentd configuration file using the script below. This ensures that environment variables are set correctly and logs are sent to the desired location.
4.2 Oleria PD Agent installation process
Accept the license terms and select Next
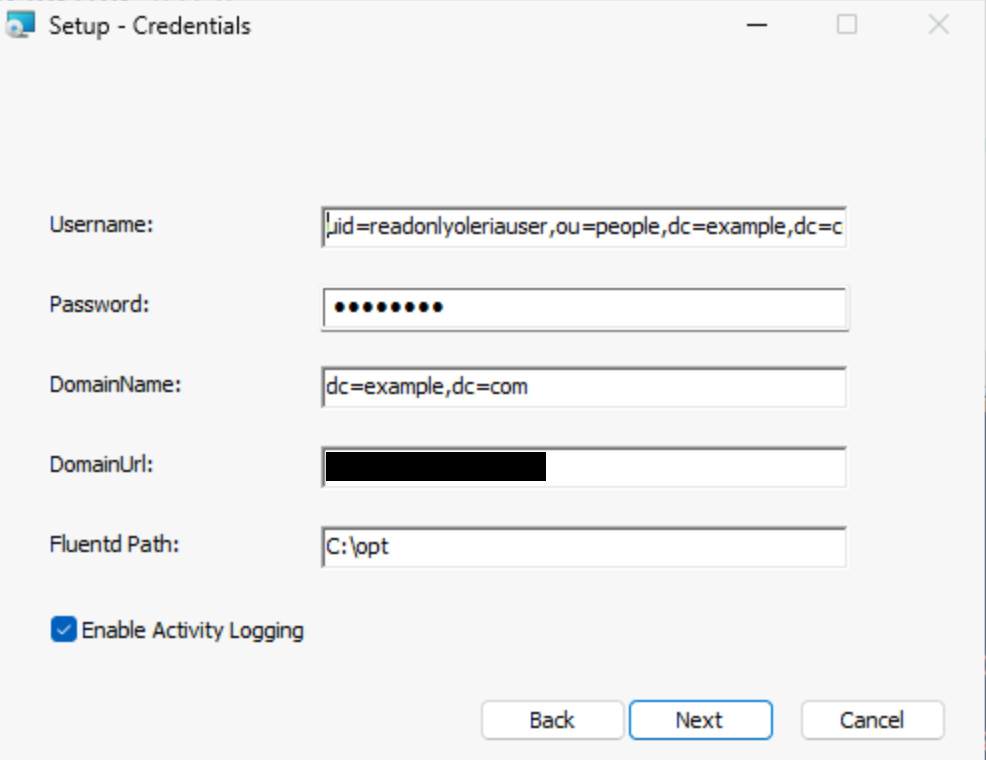
On the next page, provide the following.
- Username: Provide the Service Account name created in step 1
- Password: Provide the Service Account password
- DomainName:: Provide your domain name. Example if your domain name is example.local, provide dc=example,dc=local
- DomainUrl: Provide your domain controller ip address
Select Next, and follow the prompts to complete the installation.
- Fluentd Path: Enter the path where you installed Fluentd in Step 4.1.
- Activity Enabled Checkbox: Enable this checkbox only if Fluentd is installed and its path has been correctly provided.
Click Next and follow the remaining prompts to finalize the installation.
Once the installation is completed, you will see an OleriaPDConnectAgent service in the services.
Step 5: Verify the Ping Directory status from the connected applications
Log in to your workspace → connected integrations → Ping Directory → select View Details to open the side pane to view the agent health status.

Contact us
For questions about this integration, please contact us at support@oleria.com.
