Oleria provides adaptive and autonomous access security that sets your business free. As part of that promise, we integrate your AWS into the Oleria platform. This document provides step-by-step guidance on integrating your instances at the AWS organization level and at the AWS account level with your Oleria workspace.
Pre-requisites
- AWS Admin role
Note : Please use a service account (and not an employee account) with the suggested privileges for the integration to ensure continuity
Steps to Integrate AWS Account with Oleria Workspace
Currently Oleria supports two approaches. Follow the one that is most appropriate for your organization.
- Integrate AWS Account
- Integrate AWS Organization
Integrate AWS Account
Step 1: Log in as an admin user to the AWS Management Account (also known as the master account) that will be connected to Oleria. This creates a session.
Step 2: In the same browser, open a new tab and log in to Oleria workspace. Select Integrations → select AWS Management Plane, and S3. A side page opens, and select Account from the Connector scope dropdown and select Launch AWS CloudFormation.
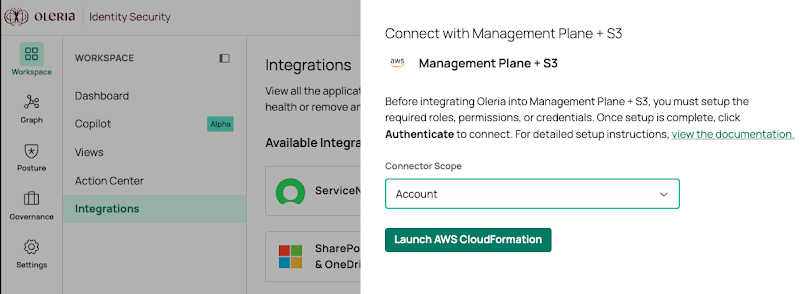
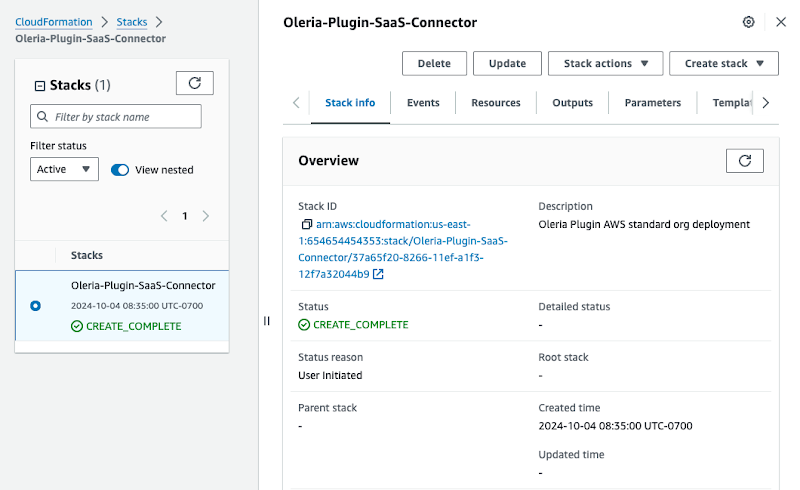
Step 3: It will redirect you to your AWS instance. You will see a CloudFormation stack. The stack name Oleria-Plugin-SaaS-Connector is preselected. Acknowledge and click create stack.

Step 4: You will see the Cloud Stack creation completes
Note: The account that is used for Oleria integration should have the following privileges
- cloudformation:CreateStack
- cloudformation:CreateUploadBucket
- cloudformation:DescribeStacks
- cloudformation:DescribeStackEvents
- cloudformation:GetStackPolicy
- cloudformation:GetTemplateSummary
- cloudformation:ListStacks
- cloudformation:ListStackResources
- iam:AttachRolePolicy
- iam:CreatePolicy
- iam:CreateRole
- iam:ListRoles
- iam:GetRole
- iam:DeleteRolePolicy
- iam:PutRolePolicy
- s3:GetObject
- s3:CreateBucket
- s3:PutObject
- sns:ListTopics
To enable remediations, take the following steps
To remove user from group and add user back to group (i.e. for reversing your decision/undo), grant the following privileges
iam:AddUserToGroup
iam:RemoveUserFromGroup
Step 5: Select the Resources tab and navigate to the oleriaConnectorRole.
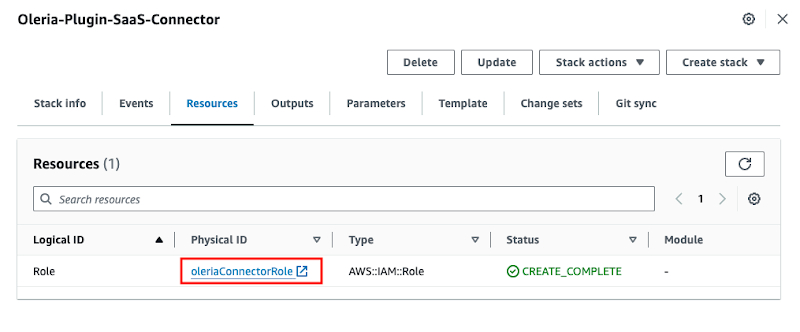
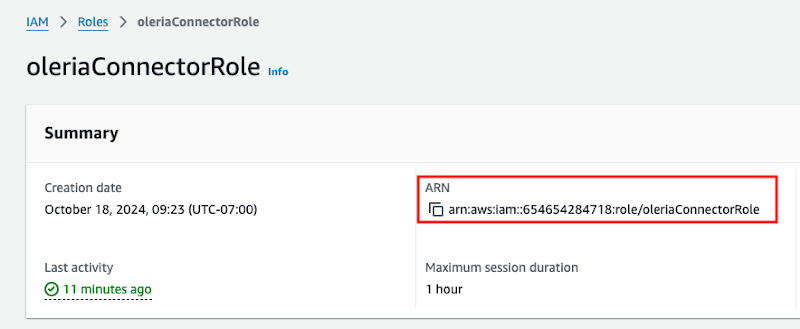
Step 6: Copy the oleriaConnectorRole ARN
Step 7. This step is required if the S3 bucket is encrypted with a KMS key. Update the KMS key policy to allow access to the Oleria connector role.
7.1. Search CloudTrail → select Management Events
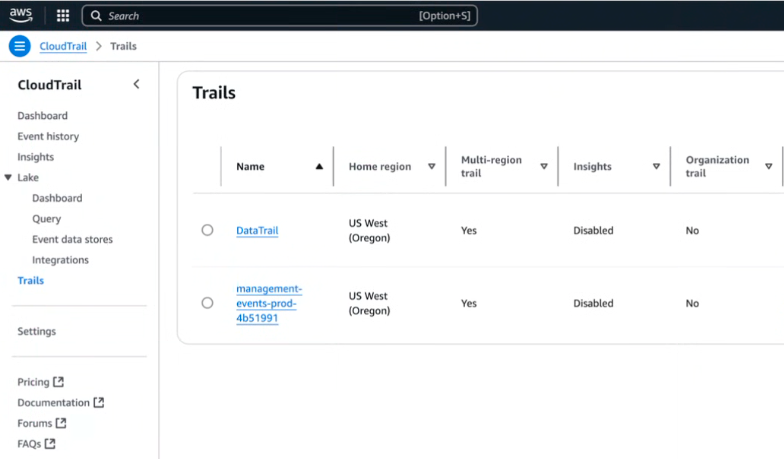
Note: If they have multiple trails, they need to select the first trail and check for encrypted KMS key. If S3 is encrypted, you will see KMS key link
7.2. Select the AWS KMS key link
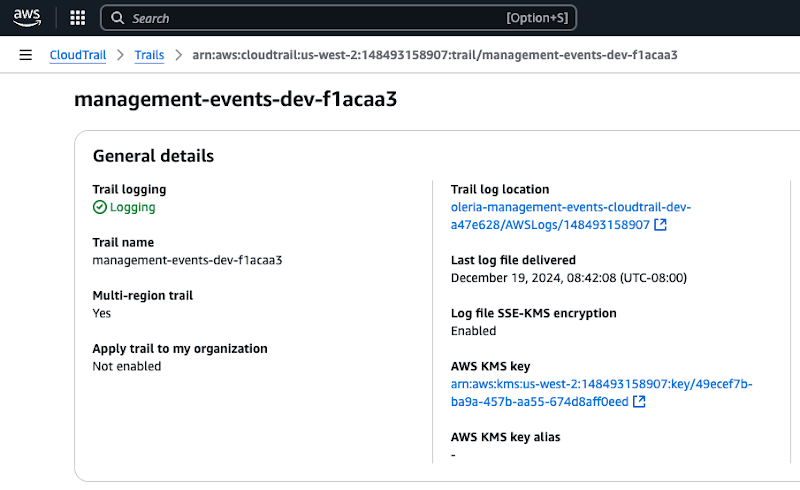
Update the KMS key policy as shown below.
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "AllowOleriaConnectorAccess",
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::accountID:role/oleriaConnectorRole"
},
"Action": [
"kms:Decrypt",
"kms:DescribeKey"
],
"Resource": "*"
}
]
}
Replace accountID with your AWS account ID.
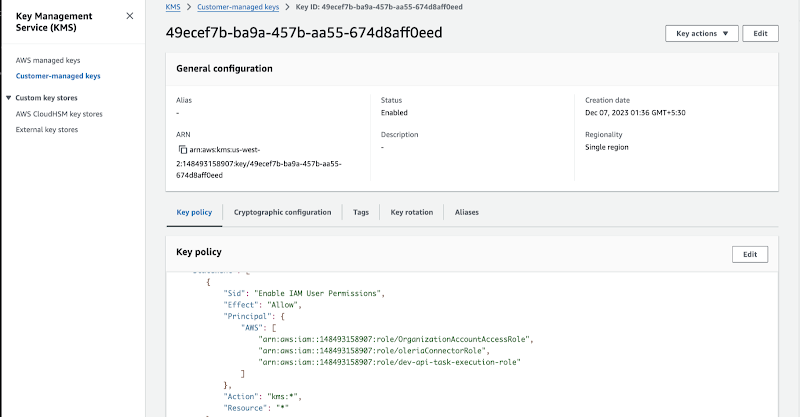
This policy allows the Oleria connector role to use `kms:Decrypt` and `kms:DescribeKey` for KMS-encrypted S3 access.
Step 8: Return to your Oleria Workspace, provide Role ARN copied in step 6. Select the checkbox and click Authenticate.
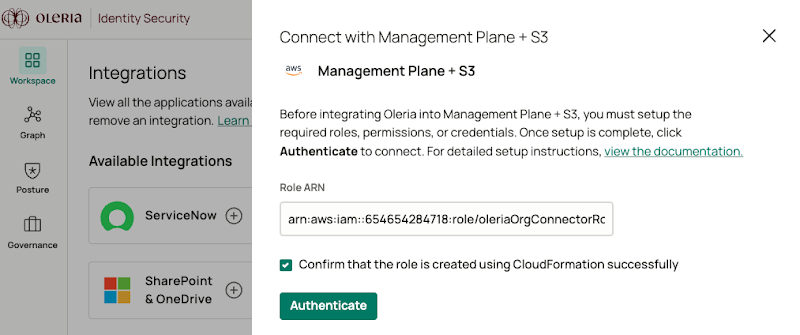
Step 9: Find a newly integrated AWS Management Plane + S3 in your Oleria workspace connected integrations
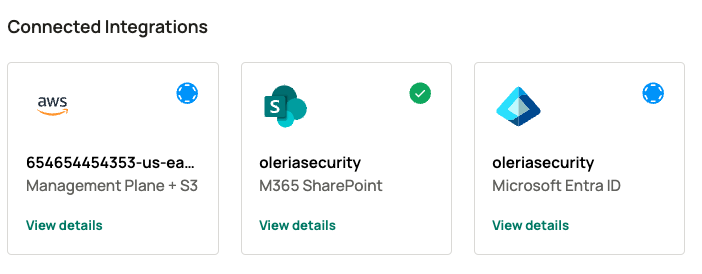
Integrate AWS Organization
Step 1: Log in as an admin user to the AWS Management Account (also known as the master account) that will be connected to Oleria. This creates a session.
Select the user on the top right corner, and select Organization
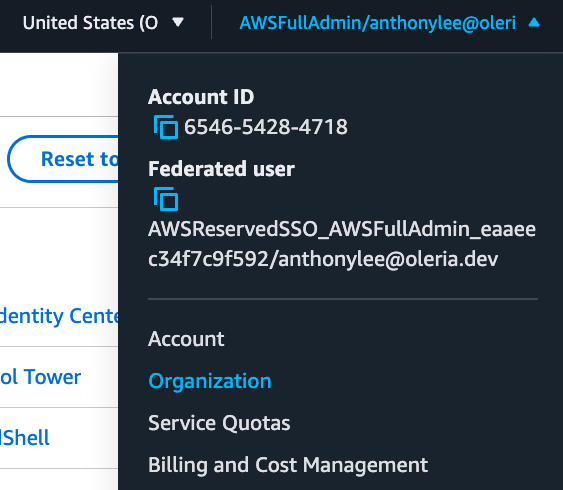
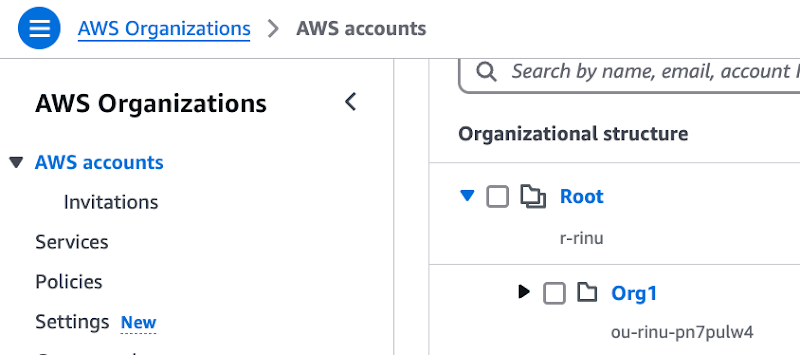
Step 2: Copy the Root name
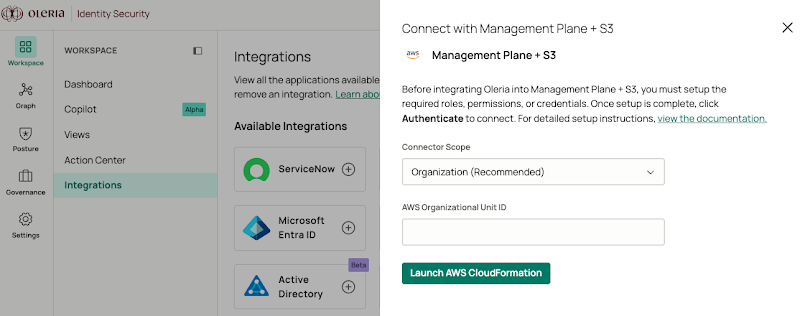
Step 3: Log in to Oleria workspace. select Integrations → select AWS Management Plane + S3. A side page opens, select Organization (Recommended), provide the organization unit ID copied in step 2 and click Launch AWS CloudFormation.
Step 4: It will redirect you to your AWS instance. You will see a CloudFormation stack. The stack name Oleria-Plugin-SaaS-Connector is preselected. Acknowledge and click Create Stack.
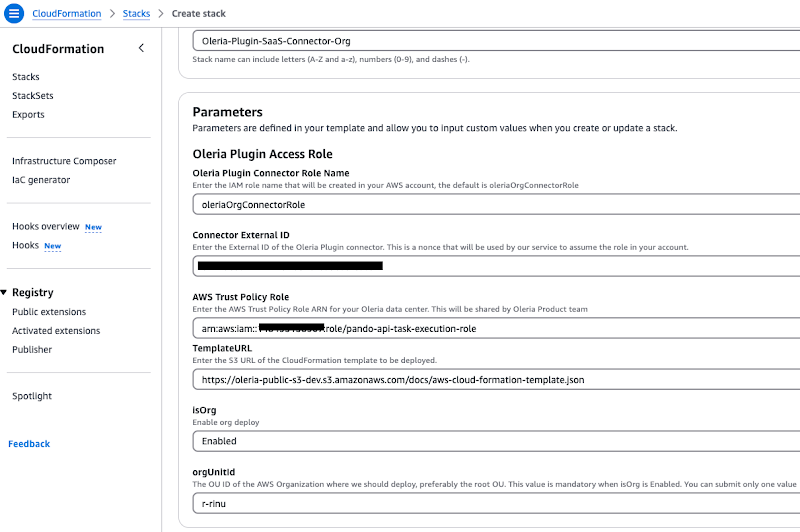
Step 5: You will see the Cloud Stack creation completed. It takes ~1min.

Note: The account that is used for Oleria integration should have the following privileges
- cloudformation:CreateStack
- cloudformation:CreateUploadBucket
- cloudformation:DescribeStacks
- cloudformation:DescribeStackEvents
- cloudformation:GetStackPolicy
- cloudformation:GetTemplateSummary
- cloudformation:ListStacks
- cloudformation:ListStackResources
- iam:AttachRolePolicy
- iam:CreatePolicy
- iam:CreateRole
- iam:ListRoles
- iam:GetRole
- iam:DeleteRolePolicy
- iam:PutRolePolicy
- s3:GetObject
- s3:CreateBucket
- s3:PutObject
- sns:ListTopics
To enable remediations, take the following steps
To remove user from group and add user back to group (i.e. for reversing your decision/undo), grant the following privileges
iam:AddUserToGroup
iam:RemoveUserFromGroup
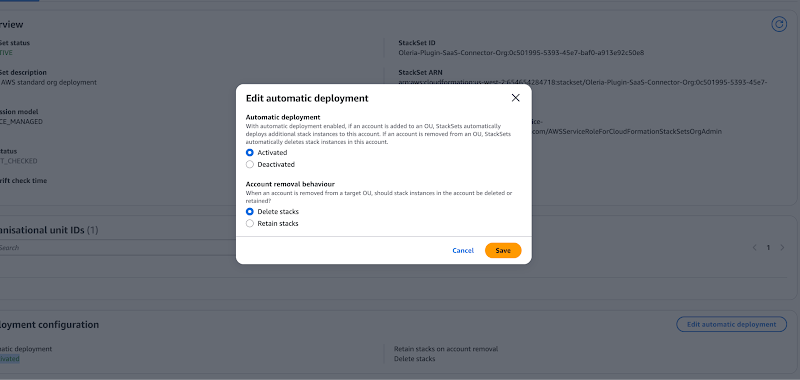
Note : Before adding stacks, verify the Stackset’s configuration
- For the integration to automatically apply to new AWS accounts added to your organization in the future, you should ensure auto-deployment is active.
- In the CloudFormation console, navigate to StackSets from the left-hand menu. -> Select the Oleria-Plugin-SaaS-Connector-Org StackSet.-> Under the Deployment configuration section, click Edit automatic deployment. Ensure that Automatic deployment is set to Activated
Step 6: Select the Resources tab and navigate to the oleriaConnectorRole.

Step 7: Copy the oleriaConnectorRole ARN

Step 8. This step is required if the S3 bucket is encrypted with a KMS key. Update the KMS key policy to allow access to the Oleria connector role. You need to perform on each account CloudTrail.
8.1. Search CloudTrail → select Management Events

Note: If they have multiple trails they need to select the first trail and check for encrypted KMS key. If S3 is encrypted, you will see KMS key link
8.2. Select the AWS KMS key link

Update the KMS key policy as shown below.
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "AllowOleriaConnectorAccess",
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::accountID:role/oleriaConnectorRole"
},
"Action": [
"kms:Decrypt",
"kms:DescribeKey"
],
"Resource": "*"
}
]
}
Replace accountID with your AWS account ID.

This policy allows the Oleria connector role to use `kms:Decrypt` and `kms:DescribeKey` for KMS-encrypted S3 access.
Step 9: Return to your Oleria Workspace and select the region copied in step 6. Select the checkbox and click Authenticate.

Step 10: Find a newly integrated AWS Management Plane + S3 in your Oleria workspace connected integrations

