Oleria Identity Security: Bringing modern access management to the dynamic enterprise

Featured event: A CISO’s take
Join Jim Alkove and Ramy Houssaini to learn how forward-thinking security teams are addressing Enterprise AI Copilot risks.
Today marks a big step for Oleria — and the future of enterprise identity security: after months of testing with our early adopter customers, Oleria Identity Security is now generally available!
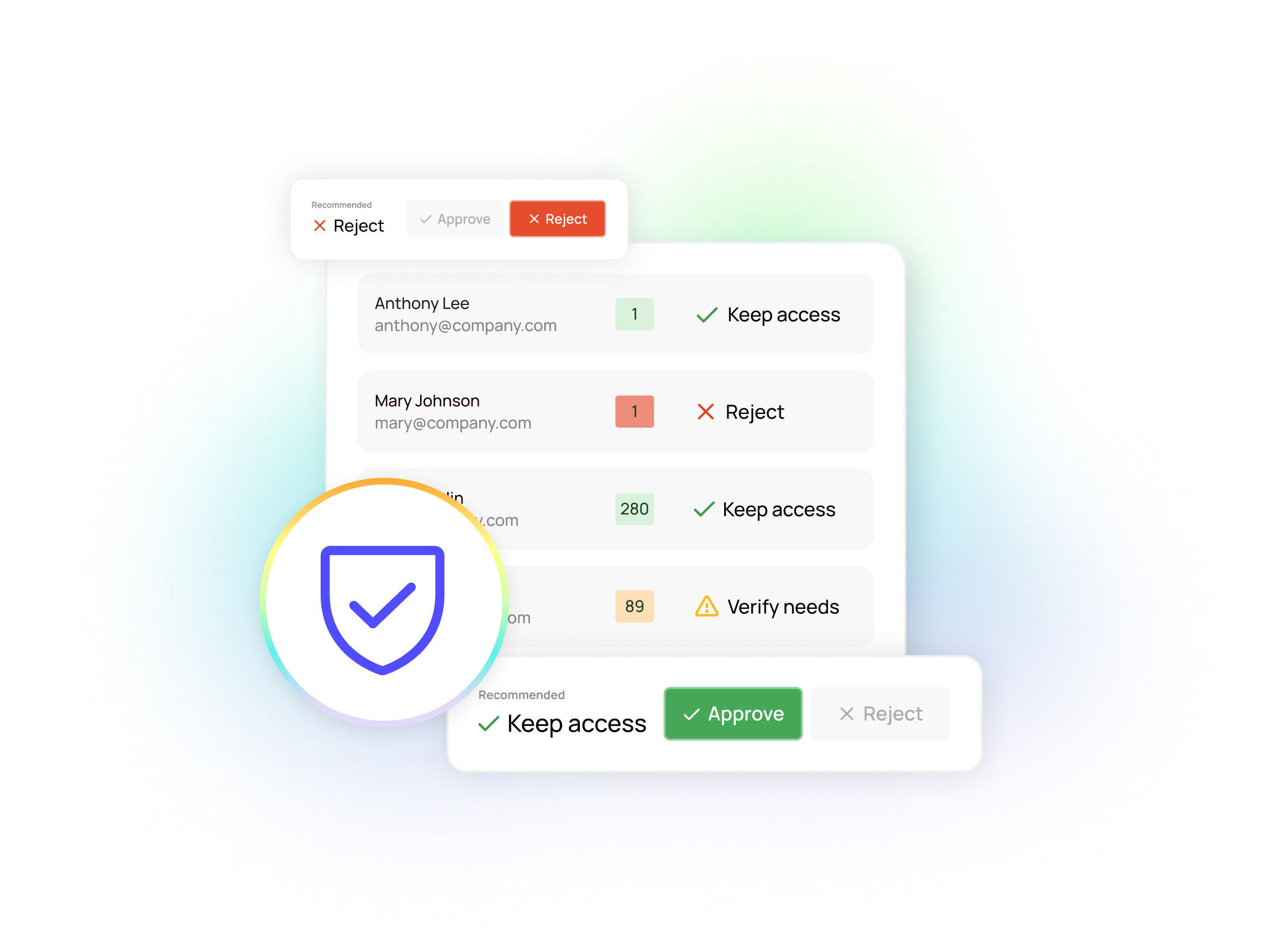
Oleria Identity Security provides first-of-its-kind fine-grained access visibility including access usage insights at an individual resource level, so CISOs can finally and confidently answer the critical questions: Who has access to what? How did they get it? What are they doing with it?
With this release, we're actively onboarding enterprise and Fortune 500 customers onto Oleria’s Trustfusion Platform.
Fast-moving and forward-looking organizations worldwide can now access the full capabilities of Oleria Identity Security to power key outcomes:
- Get an at-a-glance understanding and deep visibility into permissions and usage with Oleria's intuitive and comprehensive Access Graph.
- Enable real-time and continuous access risk monitoring to make informed, data-driven decisions about access risks.
- Identify and swiftly mitigate a wide range of access and configuration risks — from anomalous login attempts to unauthorized external sharing — to safeguard critical resources.
- Leverage proactive, actionable insights and remediation recommendations to reduce the attack surface and enhance security posture.
- Effortlessly identify and remove outdated accounts and unused permissions, reducing the organization's attack surface and ensuring compliance with ease.
Identity is the cybersecurity battlefront — legacy approaches can't keep up
Oleria Identity Security arrives at a critical moment: Identity security is now the front line of the cybersecurity battle. IBM says 2023 saw a 71% year-over-year increase in attacks targeting identities — and for the first time, abusing valid accounts became cybercriminals' most common entry point into victim environments, 1 in 3 incidents.
Why are malicious actors homing in on identity as an exploitable weak point? Because CISOs and their teams are increasingly vexed by the limitations of legacy Identity and Access Management (IAM) systems.
The modern enterprise digital ecosystem has become incredibly complex and dynamic. The typical organization now runs hundreds or even thousands of applications to support an ever-changing mix of short-term projects and ongoing operations. Yet, identity security models haven't evolved to match this dynamic environment. They're too rigid, too static and too reliant on manual workflows and patchwork visibility.
Over-provisioning is a rampant problem in most organizations. Microsoft reports that 95% of permissions are unused in the typical organization — and that 90% of identities are using just 5% of their granted permissions. However, blind spots caused by limited visibility (especially into cloud applications) make identifying and addressing access risks challenging. Moreover, today's approaches are complex and time-consuming — costing organizations a fortune to manage access using multiple tools and enormous human effort.
As a result, everyone loses. Security isn't tight enough. End users are frustrated by excessive friction. Businesses don't have the freedom they need to drive speed, agility and innovation. I've experienced this firsthand, but it's not just anecdotal: Gartner says that by 2026, "70% of identity-first security strategies will fail unless organizations adopt context-based access policies that are continuous and consistent."
Building adaptive identity security to enable and protect today’s dynamic enterprise
I know the pain and costs of this problem. In security leadership roles at Salesforce and Microsoft, my teams and I found ourselves juggling the frustrating reality that access to applications and data was failing to meet our security goals, yet also placed maddening obstacles in the way of employees' productivity, collaboration and innovation. Essentially, today’s approach results in most users having significantly more access to tools and data than they need, while simultaneously not providing appropriate access to those who need it. This first-hand experience is shared by other leaders here at Oleria — and that's what drove us to begin building a better solution more than a year ago.
We believe today's identity technologies are holding companies back. We don't think companies should have to choose between security and business agility. Security should be adaptive to the organization and sensitive to every context. It should protect data and maintain trust while allowing you to accelerate the pace of business, without ever getting in your way. In short, we believe that identity systems should enable — not inhibit.
We believe today's identity technologies are holding companies back. We don't think companies should have to choose between security and business agility. That's where Oleria comes in.
So, we built Oleria Identity Security and the Oleria Trustfusion Platform to give CISOs and their teams a cloud-based solution to control all access in one place, adaptively and autonomously. Oleria Identity Security delivers full clarity and control of access, freeing our customers' organizations from the restrictions and risks of rigid legacy security operations and allowing them to collaborate and innovate at the speed of business.
Adaptive & autonomous identity security: visibility, intelligence and action
The Oleria Identity Security solution is centered on two core principles: First, identity security should be adaptive — meaning that every account should have just the access that it needs, at the right time, for the right duration. Second, identity security needs to become autonomous.
That's more than the shift from today's manual workflows to humans clicking through automated workflows — that means intelligent software managing access continuously, freeing up security teams to apply their expertise where it counts.
To deliver on these two principles, Oleria Identity Security provides three key outcomes:
- Visibility: Some of the most dangerous security blind spots in the typical enterprise revolve around decentrally managed access across the vast network of applications and infrastructure. The conventional approach leaves security teams to manually patch together all of this identity access information — meaning it happens infrequently and is highly subject to error. The Oleria Trustfusion Platform resolves this challenge by seamlessly connecting with both centrally managed access systems (Okta, Active Directory, etc.) and decentrally managed access (applications and infrastructure). But this isn't just an aggregation of logs. Oleria Identity Security brings all of your access and usage information into the universal and human-readable Oleria Access Graph, so you can clearly see who has access to what, how they got it, and what they're doing with it.
- Intelligence: Too many security solutions stop at aggregated visibility, leaving security teams with yet another giant pool of information to sift through.Oleria Identity Security transforms that centralized access visibility into usable insights that empower your identity, incident response and compliance engineers — helping them investigate access-related incidents and identify unused or unintended access. We’re hard at work developing functionality that will enable Oleria to provide intelligent recommendations to remediate access, including removal of unused access, without negatively impacting your business operations.
- Action: I worked as a CISO for most of my career, and I know I didn't just want tech to tell me about problems. I wanted tools that helped me fix them. Oleria Identity Security gives your team a single control point for rapidly and effectively remediating access risks. Even better, we're building out intelligently automated workflows that will autonomously remediate access risks and manage access independent of applications — closing security gaps faster while reducing the time and cost burdens of this ongoing challenge.
I was impressed by the comprehensive visibility we had into our access, including over-provisioned accounts, unintended access, and our coverage of multi-factor authentication. Oleria’s simple user-friendly experience gave us both clarity and direction on where to focus our efforts and the tools to easily detect access issues.
Mark Carter
CIO and CISO of Vimeo, an Oleria customer
We're changing the paradigm of enterprise identity security
In the coming weeks and months, we're excited to share firsthand perspectives from our enterprise customers on how the Oleria Identity Security solution is freeing up business leaders to focus on their core business objectives while offering CISOs peace of mind that access is appropriate and risk is minimized. We're also eager to deliver even more capabilities to extend the value and impact of Oleria Identity Security and the Oleria Trustfusion Platform.
It's been a year of tremendous progress at Oleria. We're well on our way toward helping the business world fundamentally shift the paradigms on enterprise identity security.

Built for the AI Era: How Oleria’s Unified Identity Security Approach Is Validated by the Industry

Heading