Oleria provides identity security and access management teams with visibility and intelligence into who has access to what, where they got that access, how they use it, and if they should even have it. As part of that promise, we integrate applications such as Microsoft Entra ID and M365 SharePoint into the Oleria platform. We provide multiple options for each integration and this document provides step-by-step guidance for integrating Entra ID and M365 SharePoint with your Oleria workspace.
Pre-requisites:
- The user granting these permissions must have Global Admin privileges.
Note: Standard integrations are configured with read-only permissions. If you would like to take advantage of Oleria’s access remediation capabilities, which are completely optional, you need to configure additional privileges required for write access.
Please use a service account (and not an employee account) with the suggested privileges for the integration to ensure continuity
Integration approaches
Currently Oleria supports two approaches. Follow the one that is most appropriate for your organization.
- Authenticate via Microsoft (automated configuration via OAuth)
- Client Secret Authentication (manual configuration)
Authenticate via Microsoft (OAuth)
Step 1: Log in to your Oleria workspace, select Integrations
- Select Microsoft Entra ID to integrate Entra ID
(or)
- Select Microsoft SharePoint and OneDrive to integrate Entra ID, SharePoint, and OneDrive.

Step 2: A side page opens.
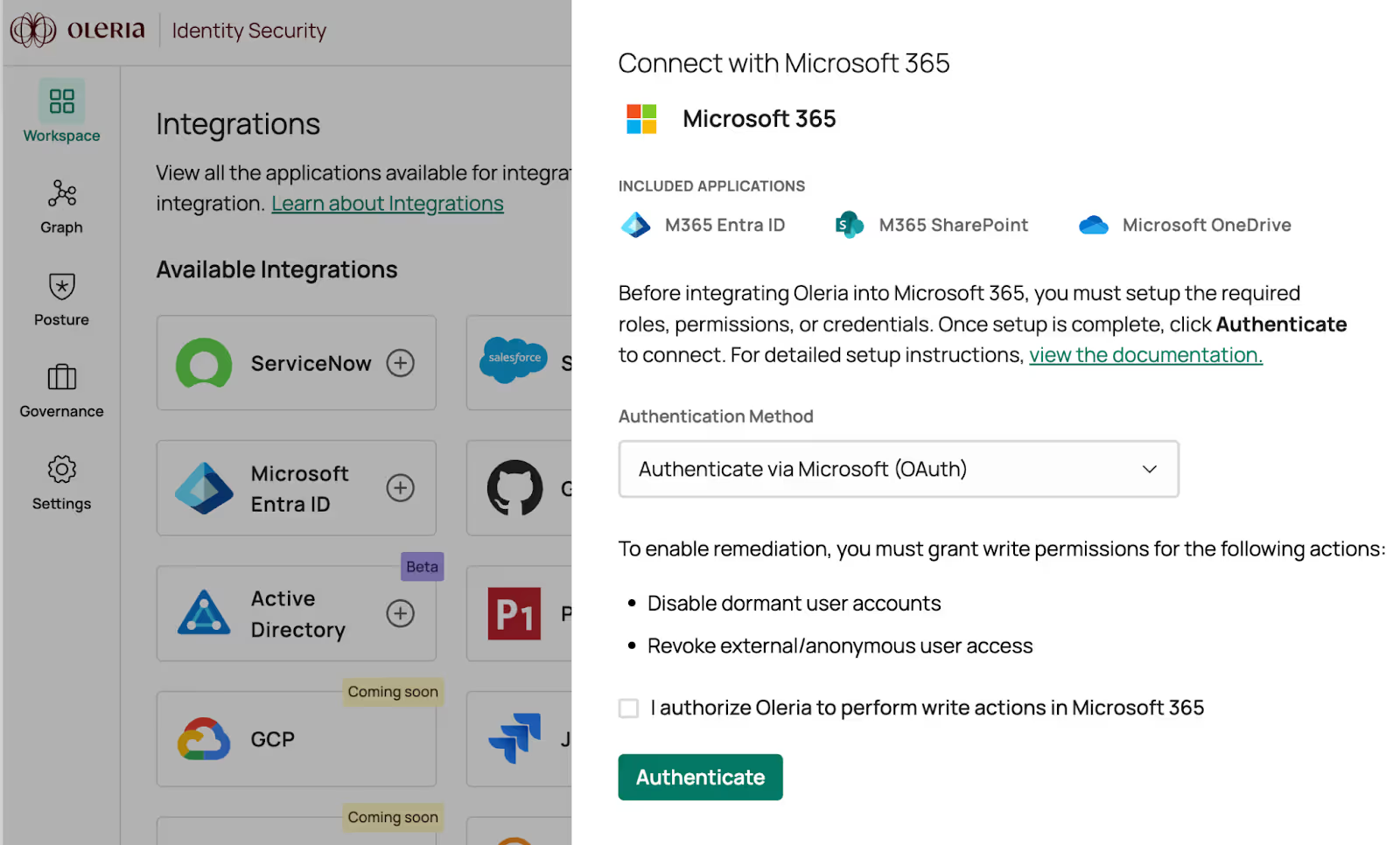
Step 3: The screen shows an option to enable write permissions to enable Oleria to perform select remediations. The Oleria remediation feature is optional. To enable remediations, select the check box. Otherwise, click Authenticate to proceed with the standard read-only permissions scope.
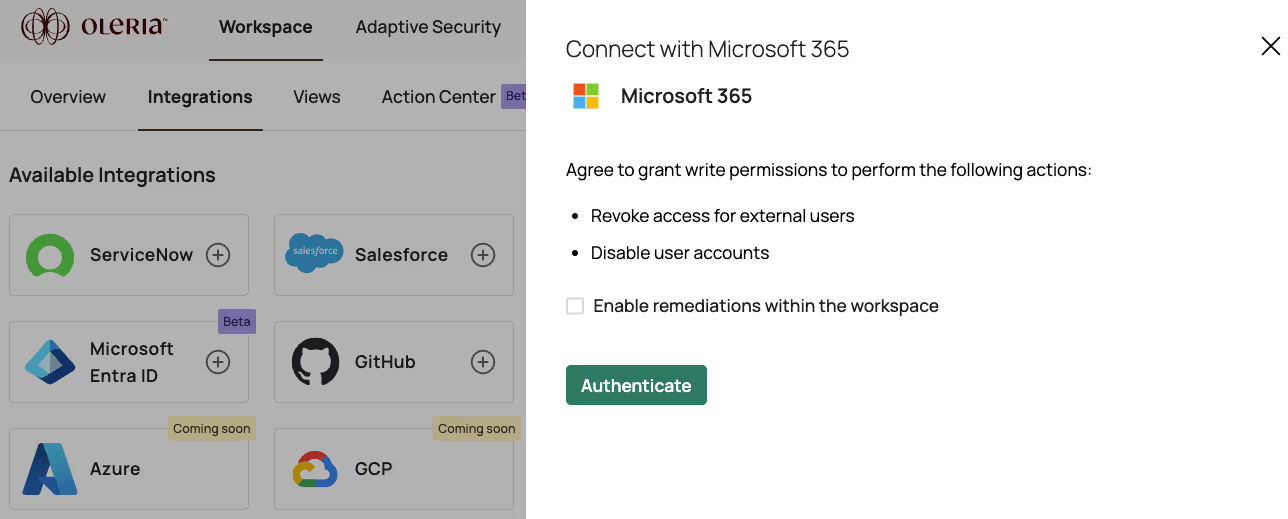
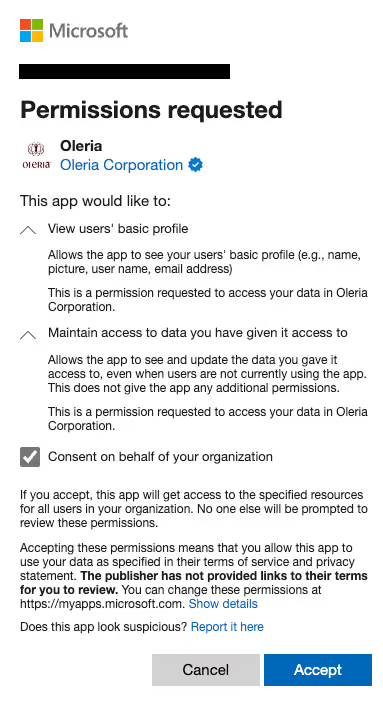
Step 4: A consent form shows up to grant permissions for the Oleria application to view the basic profile and read access. Complete the consent form by selecting “Accept.”
Step 5: Select your Microsoft account and complete authentication
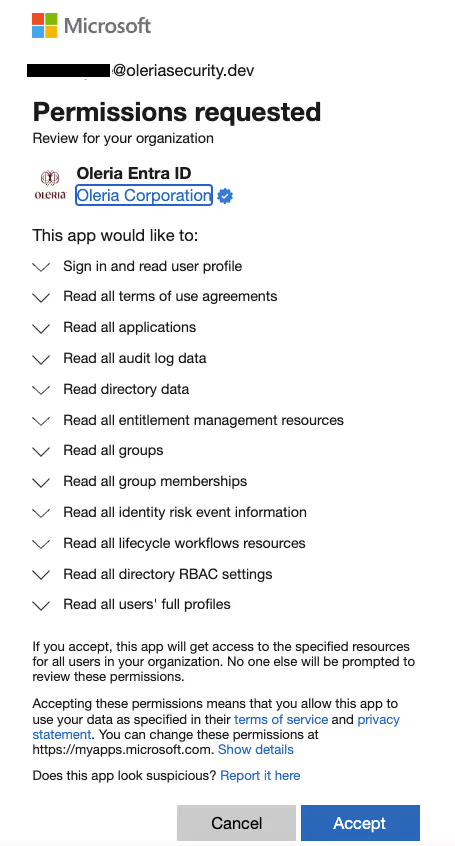
Step 6: Microsoft’s application consent form will appear with a list of requested permissions, which varies depending on your selected application and whether you wish to enable the optional remediation capabilities. The following options are available based on the application you prefer to integrate.
6.1 Microsoft Entra ID Integration without optional remediation capabilities - Standard read-only permissions are required.
6.2 Microsoft Entra ID, SharePoint, and OneDrive Integration without optional remediation capabilities—Standard read-only permissions are required.
6.3 Microsoft Entra ID Integration to allow optional remediation capabilities - Read and Write permissions are required.
6.4 Microsoft Entra ID, SharePoint, and OneDrive Integration to allow optional remediation capabilities - Read and Write permissions are required.
6.1 Standard read-only permissions required for Entra ID integration (without optional remediations capabilities)
6.2. Standard read-only permissions required for SharePoint and OneDrive integration (without optional remediation capabilities)
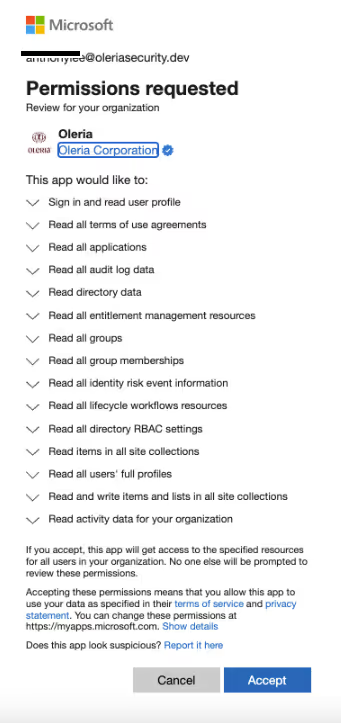
6.3. Permissions required for Entra ID integration to allow optional remediation capabilities (includes some write permissions)
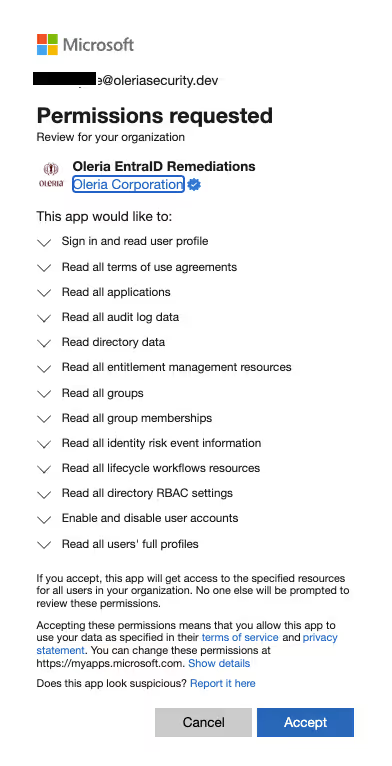
6.4. Permissions required for SharePoint and OneDrive integration to allow optional remediation capabilities (includes some write permissions)
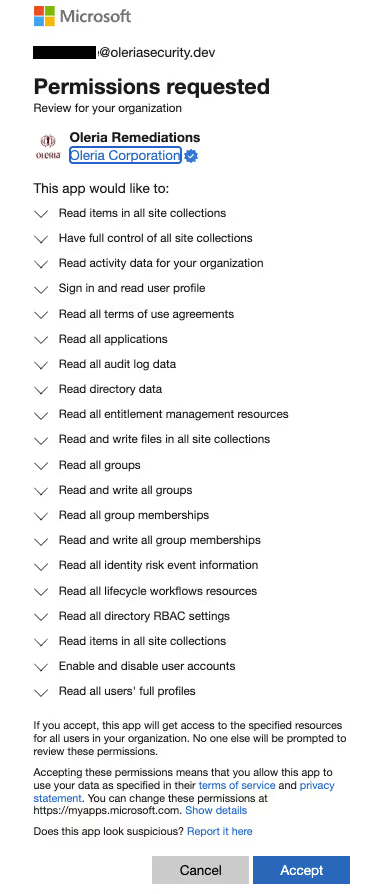
Step 7. Complete the consent form by selecting “Accept.”
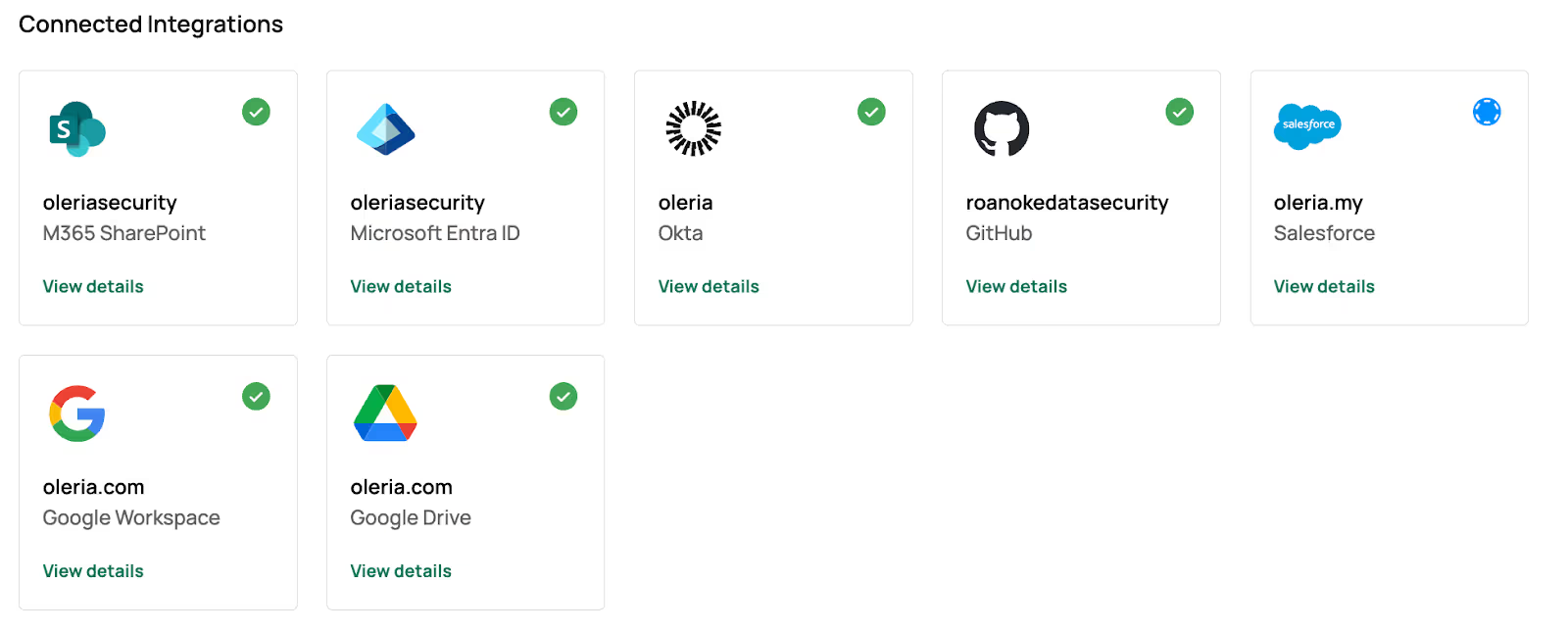
Step 8: Find the newly integrated Entra ID and M365 SharePoint instances in your Oleria workspace connected integrations
Client Secret Authentication
Step 1: Create an application in your Entra ID tenant.
Log in to Microsoft Entra ID, navigate to the App registrations, and select New registration.
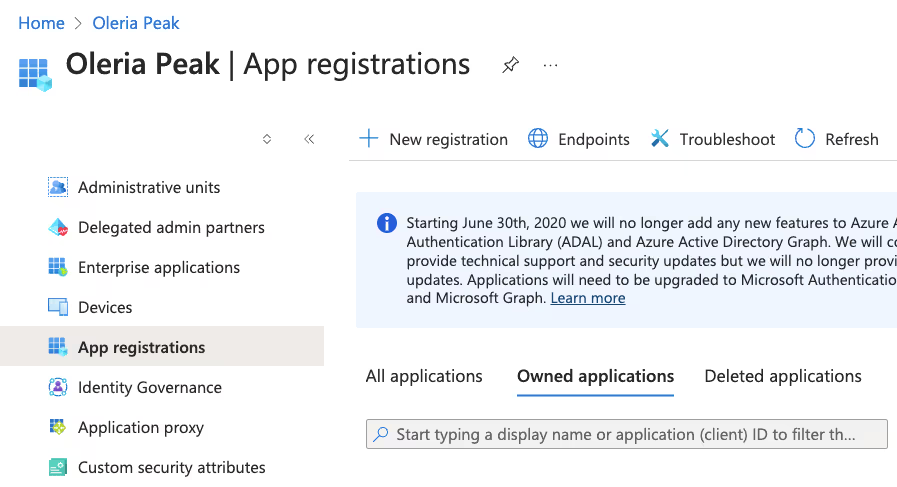
Step 2: Give a name to the application, e.g., Oleria, and select the radio button option Accounts in any organization directory (Any Microsoft Entra ID tenant - Single tenant). Click Register.
Note: If you add any tenants in the future, you must add another App registration for each individual tenant. Alternatively, you can select the option for Accounts in any organizational directory (Any Microsoft Entra ID tenant - Multitenant) and this will cover all tenants by default.
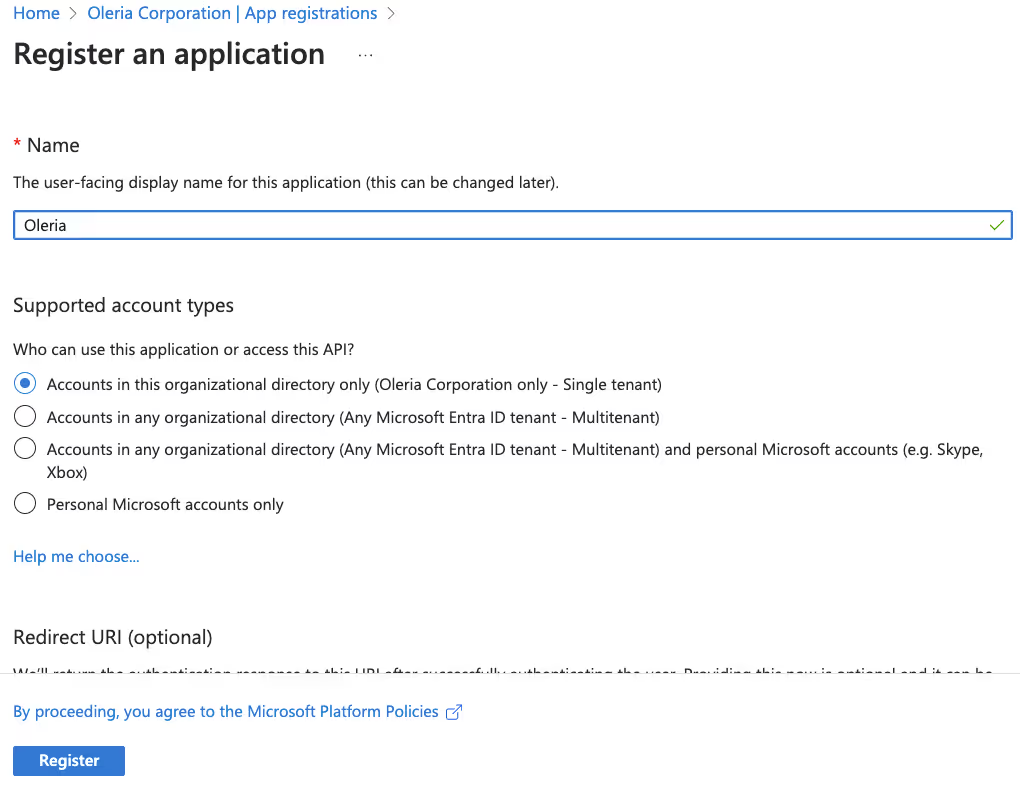
Step 3: Open the application and select Manage → API permissions. Select Add permission
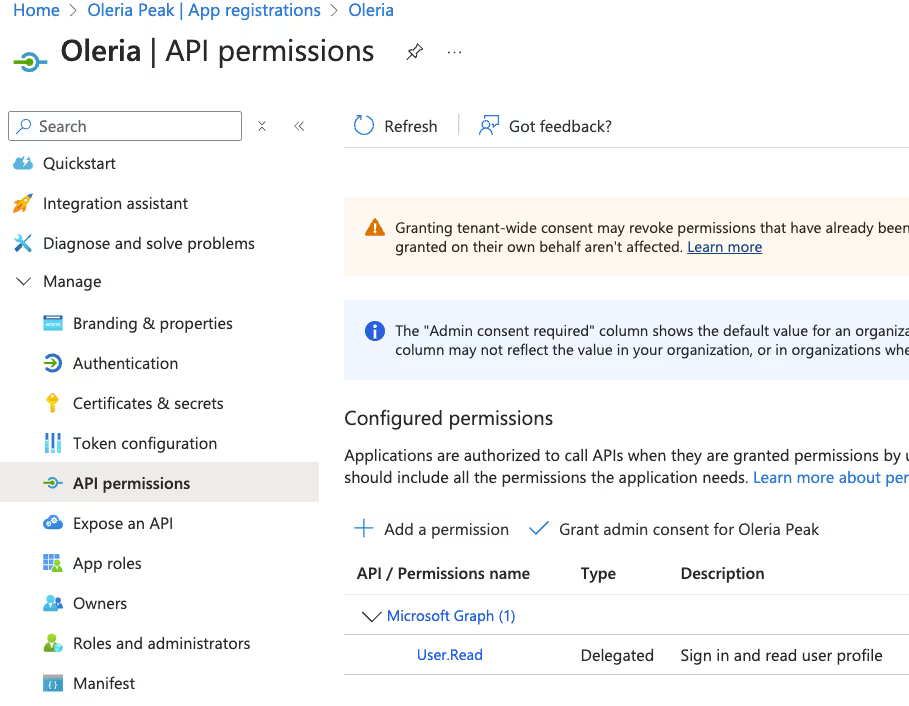
Step 4: Select Microsoft Graph and select Application permissions. Add permissions
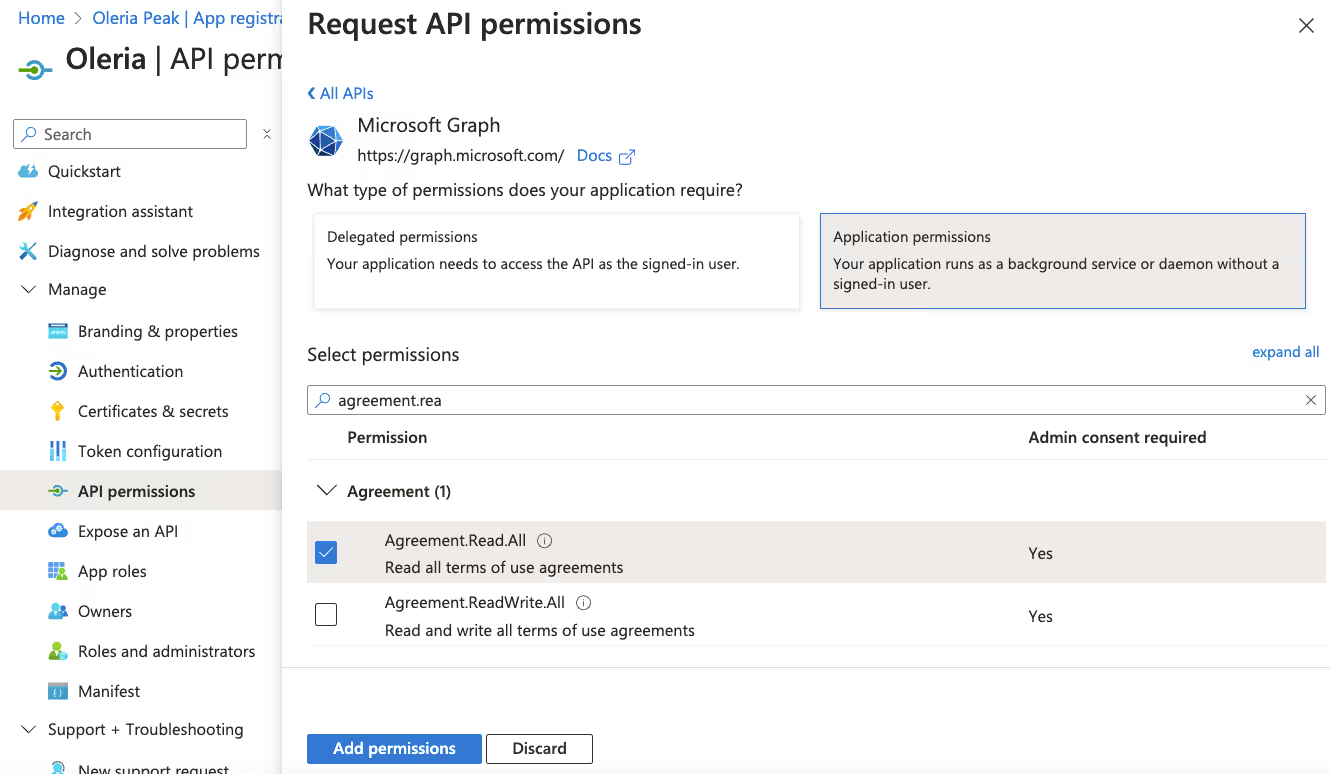
4.1 Standard read-only permissions required for Entra ID integration (without optional remediations capabilities)
4.2 Standard read-only permissions required for SharePoint and OneDrive integration (without optional remediation capabilities)
4.3 Permissions required for Entra ID integration to allow optional remediation capabilities (includes some write permissions)
4.4. Permissions required for SharePoint and OneDrive integration to allow optional remediation capabilities (includes some write permissions)
Step 5: After adding all application permissions, select Grant admin consent to complete the consent
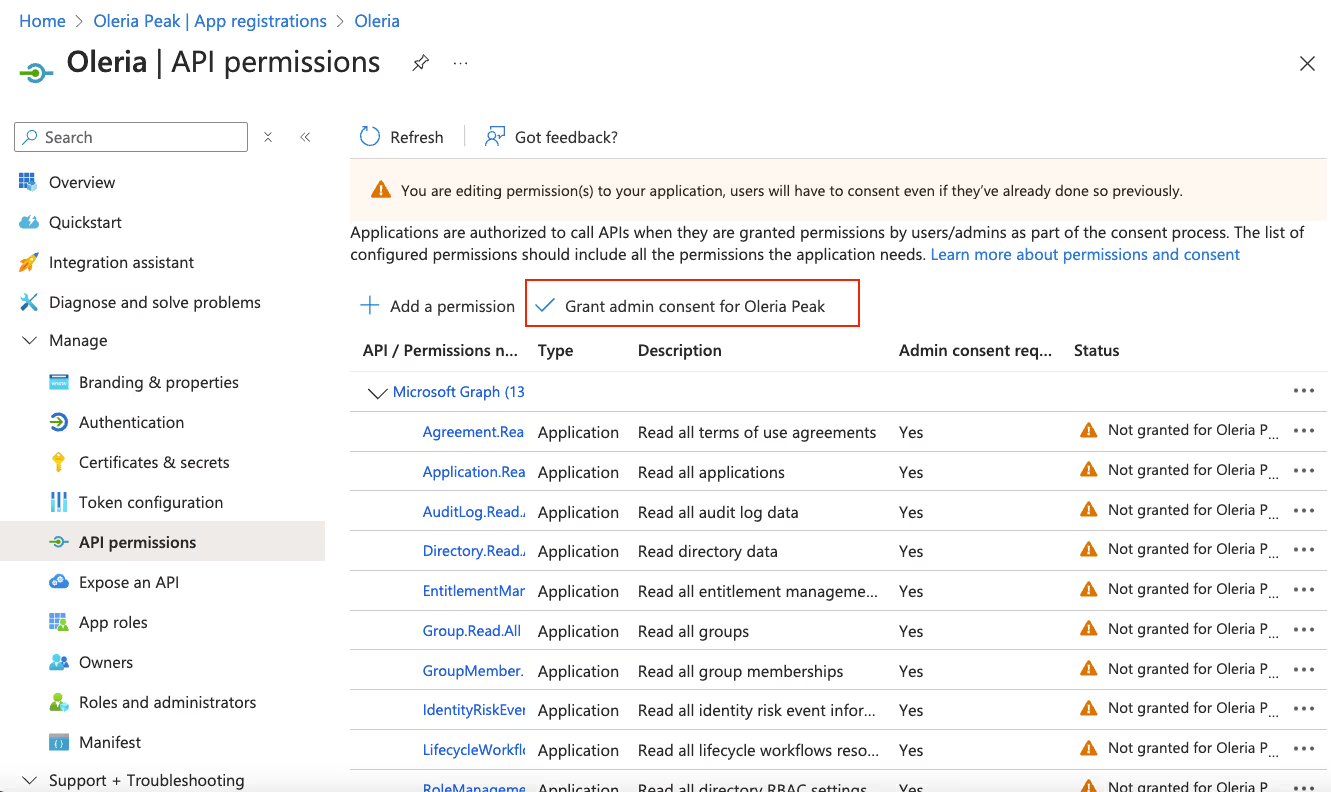
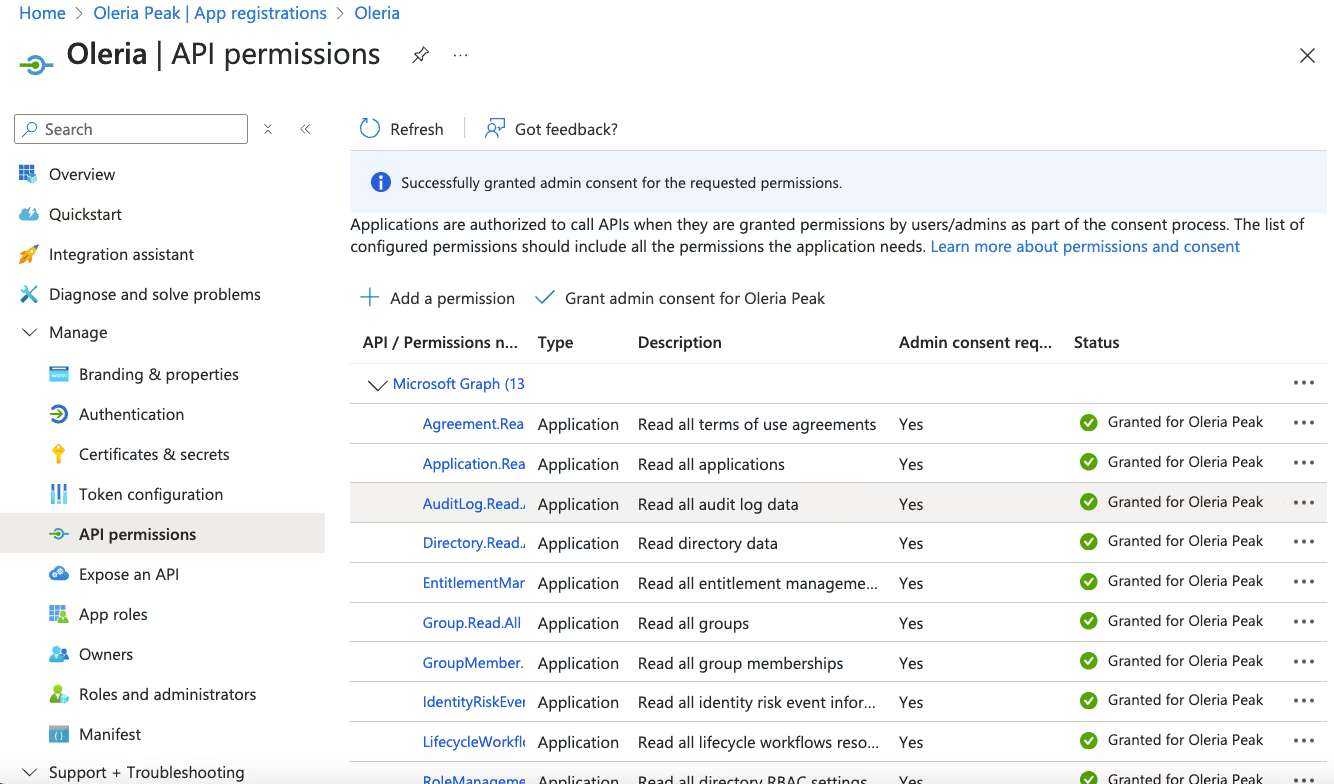
Step 6: Successful completion of Admin grant consent should mark granted status green.
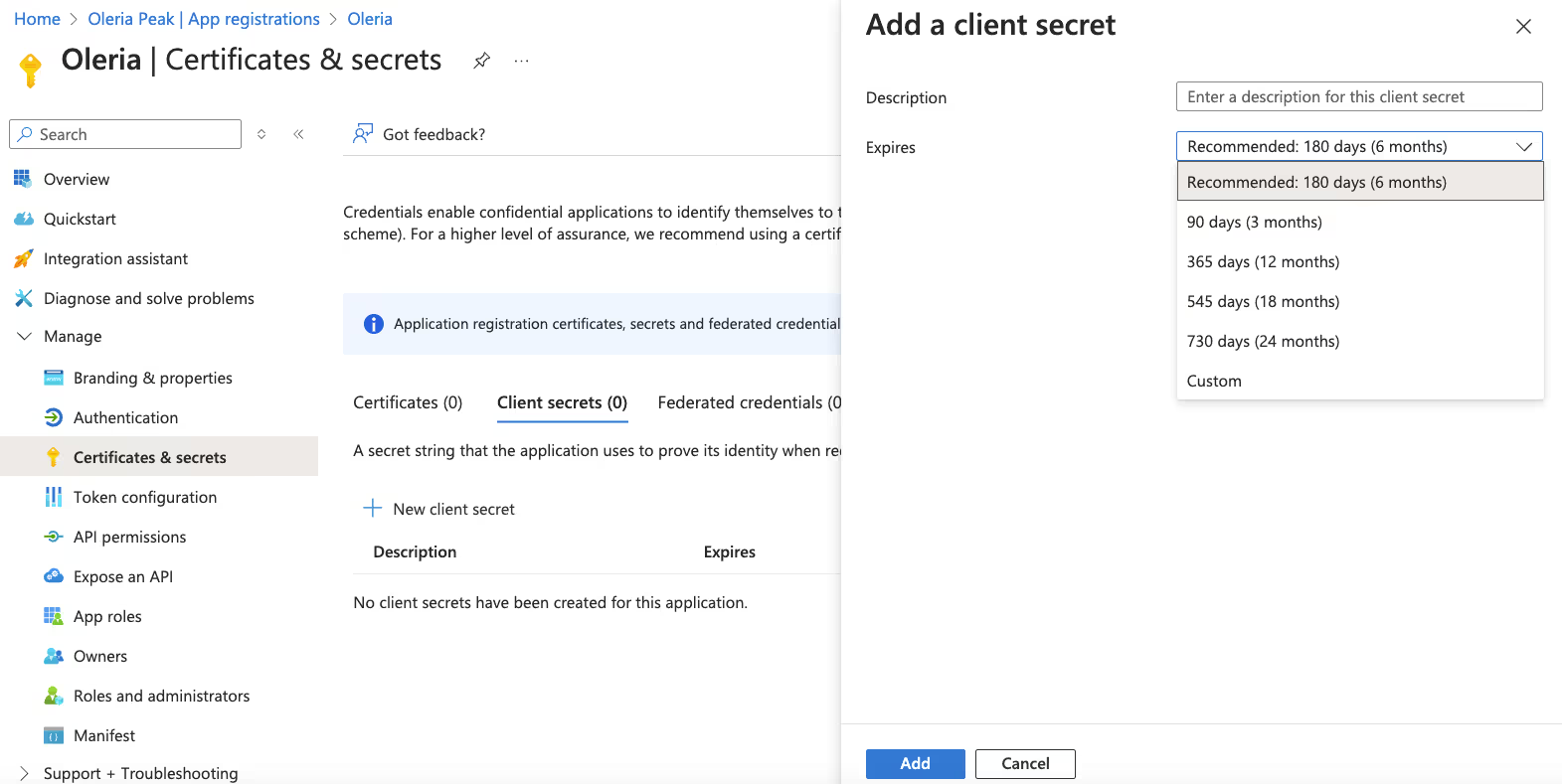
Step 7: Navigate to Certificates & Secrets, and create a client secret as shown below
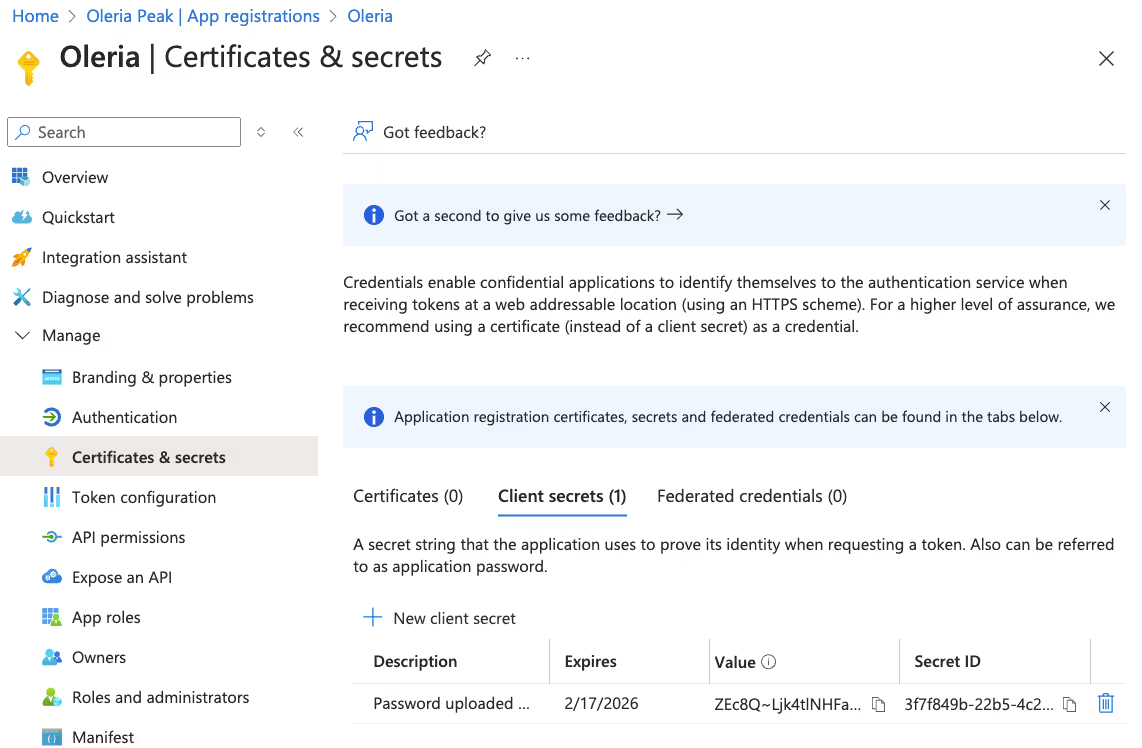
Step 8: The generated client secret will be shown as follows. Copy the Client Secret Value.
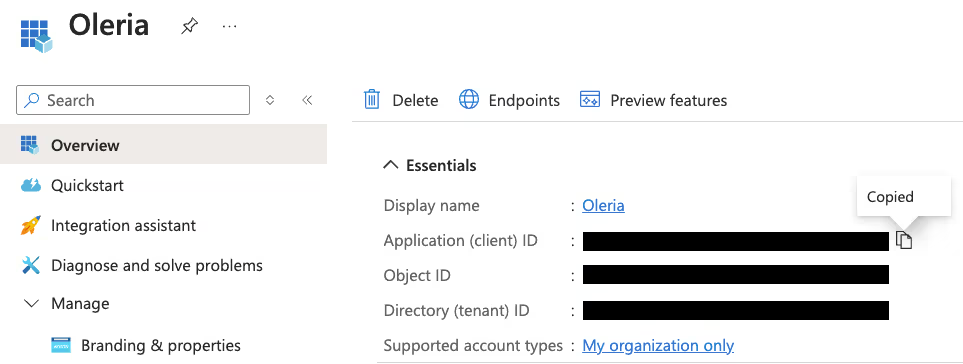
Step 9: Capture your Client ID and Directory tenant ID
Step 10: Integrate Microsoft SharePoint in the Oleria workspace.
Log in to Oleria workspace using the Oleria Administrator role → select Integrations, and select Microsoft SharePoint and OneDrive.

A side panel opens
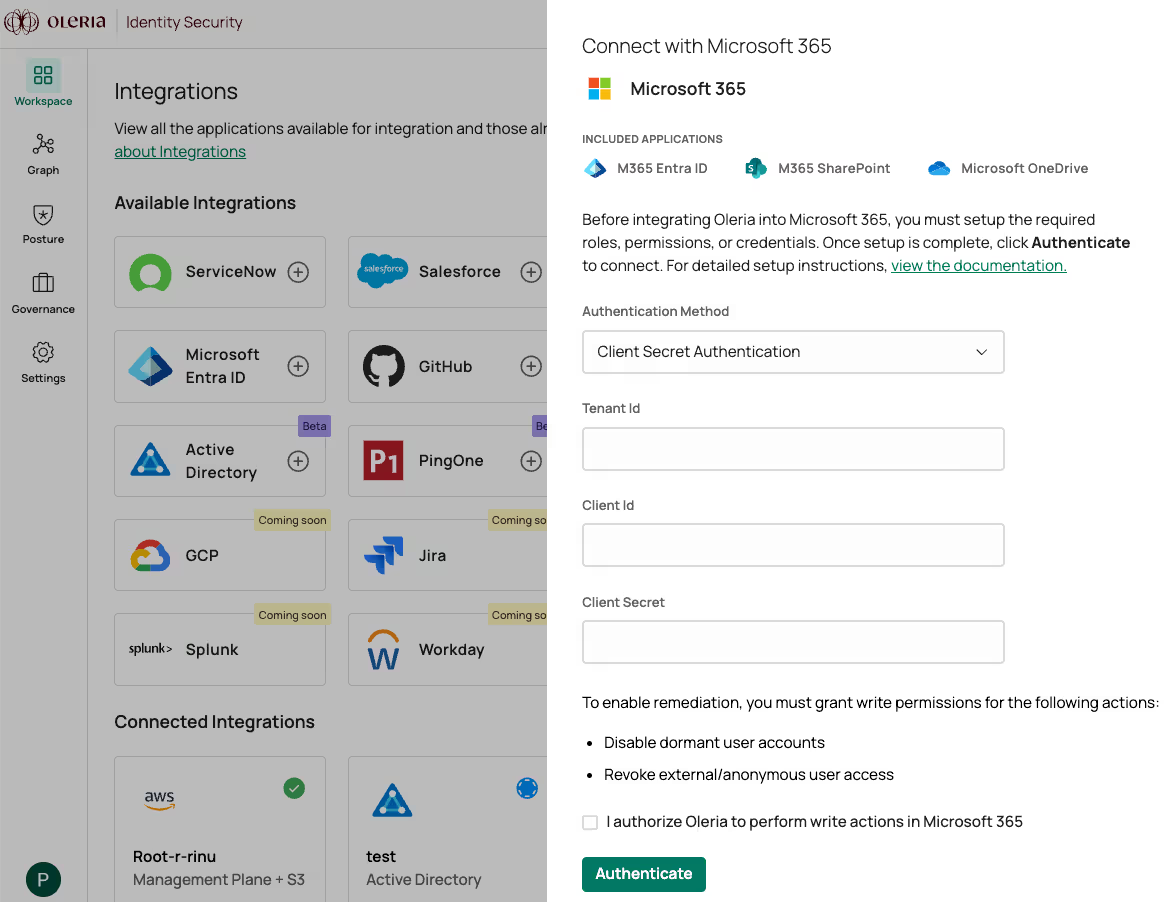
Step 11: Select the Authentication Method dropdown and select Client Secret Authentication.
Provide Client Secret Value captured in step 8, Tenant ID and Client ID captured in step 9.
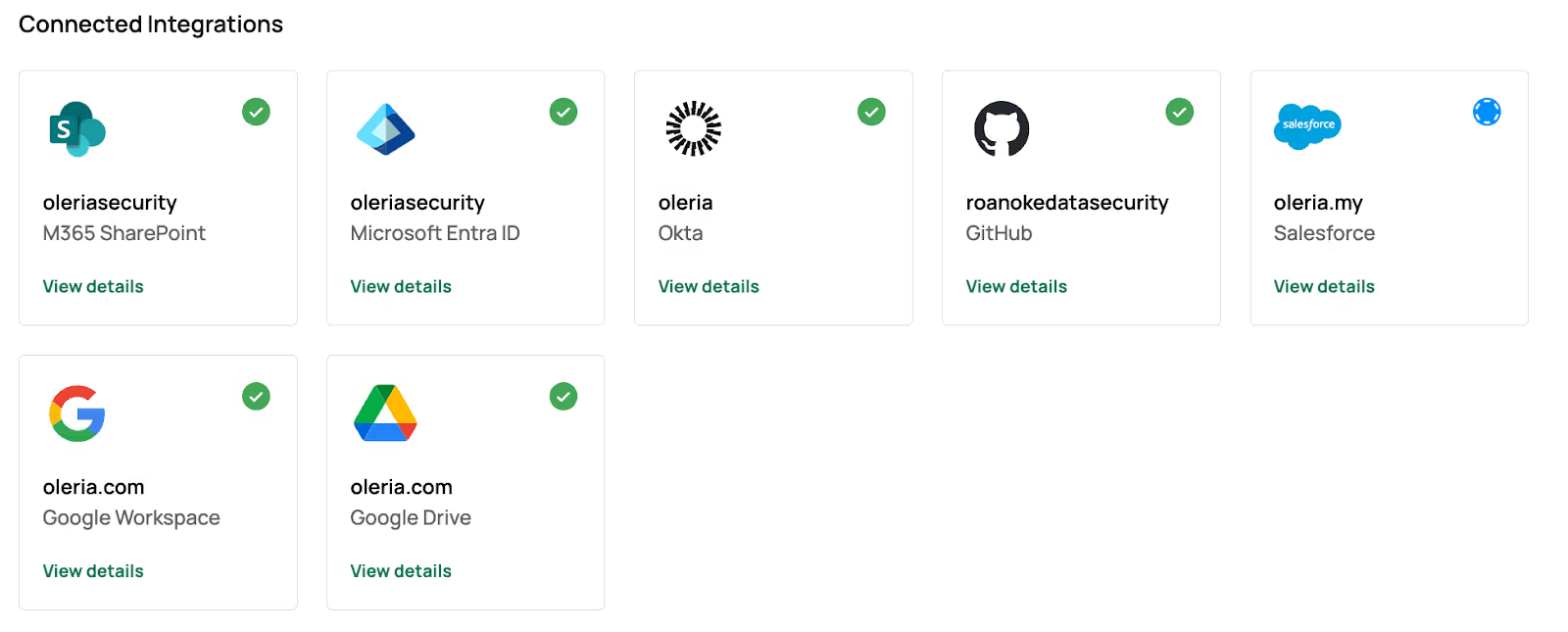
Step 12: Find the newly integrated Entra ID and M365 SharePoint instances in your Oleria workspace connected integrations
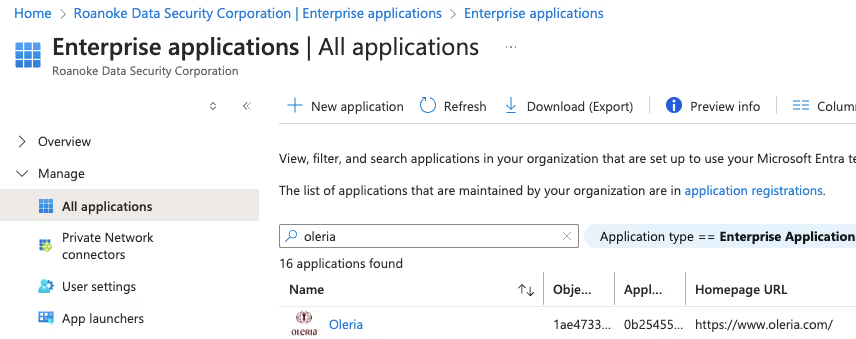
Check the Oleria App in your Entra ID instance
1. Login to your Entra ID instance, navigate to “Enterprise applications” → Select “All applications”
You will find the Oleria application in the Enterprise applications.
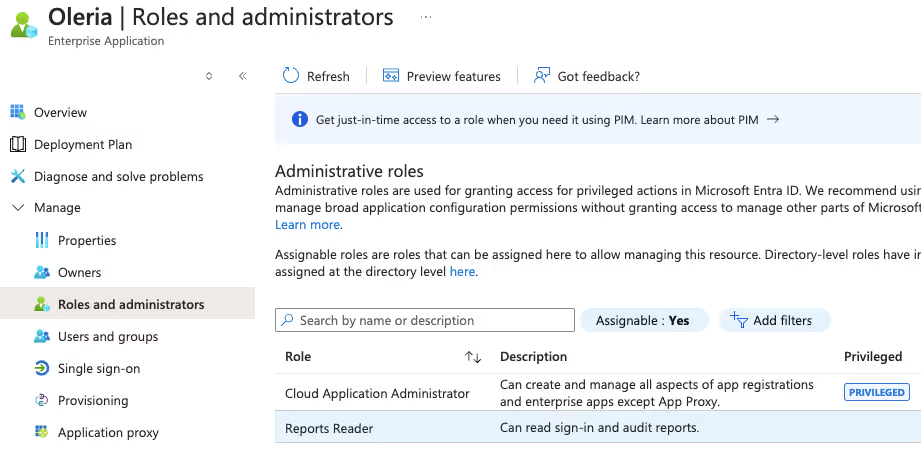
2. Select the Oleria application, navigate to “ Roles and administrators.”
You will find 2 roles
- Cloud Application Administrator
- Report Reader
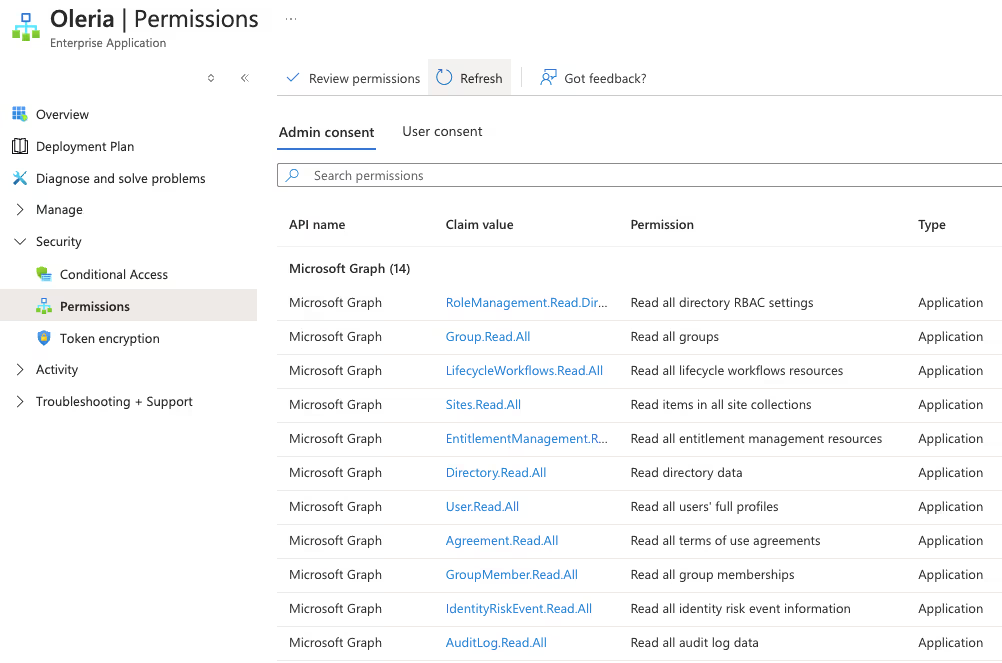
3. Select permissions to view the read permissions granted to the Oleria application
Contact us
For questions about this integration, please contact us at support@oleria.com.
